Through a malicious video or image tag on a website, an attacker can potentially trick a user into going fullscreen without the user knowing. This vulnerability affects Firefox ESR 52.5, Thunderbird 52.5, and Firefox 52.
Though not technically a vulnerability, these issues are worth mentioning due to the fact that users often have limited knowledge of fullscreen access in general and how to navigate around websites when in fullscreen.
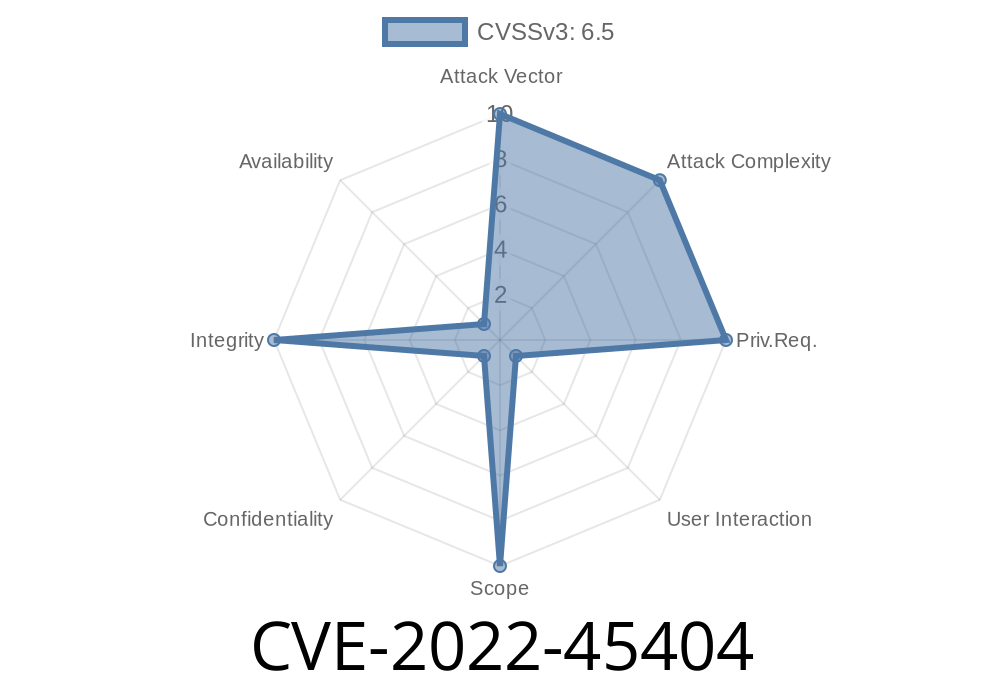
Vulnerability overview
Fullscreen is a feature that allows users to navigate the browser window while retaining their previous content. There are some cases where fullscreen will be initiated without user interaction, such as when clicking on a link that opens in fullscreen mode.
The vulnerability exists because of how the browser handles non-default fullscreen settings and how it interacts with the built-in Flash plugin. When a user goes into fullscreen mode, Firefox will send all the information about what's happening in the fullscreen tab to the server. This includes any changes made to text, images, and other properties of web pages within this tab. The attacker can insert malicious HTML tags into webpages that monitor for changes made within this fullscreen mode and then send them back to Firefox or another third party website when it's not in fullscreen mode, namely when it's in normal browsing mode.
This allows an attacker with access to Firefox or another third-party website hosting these malicious tags to execute JavaScript code on unsuspecting targets' computers if they view these tagged websites while in fullspace mode or have JavaScript enabled on their machines.
WebRTC leak vulnerability affects Firefox ESR
A recently discovered vulnerability in Firefox ESR presents a serious concern for anyone using the browser. The vulnerability affects the WebRTC protocol which is an open standard for real-time voice, video, and data communication on the web. A malicious video or image tag on a website can potentially trick a user into going fullscreen without the user knowing. This vulnerability affects Firefox ESR 52.5, Thunderbird 52.5, and Firefox 52.
The issue has been addressed in an update to Firefox which you can install by clicking here .
ContentWindow.open() unsafe access
One example of a misuse of fullscreen is when someone sends you a malicious image or video that takes users to the page, but they do not know the functionality of the fullscreen button. This means that possibly going into unintended areas of websites.
Furthermore, ContentWindow.open() can potentially be used for different purposes than intended and can lead to unintended consequences for websites.
Timeline
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 01/04/2023 16:07:00 UTC