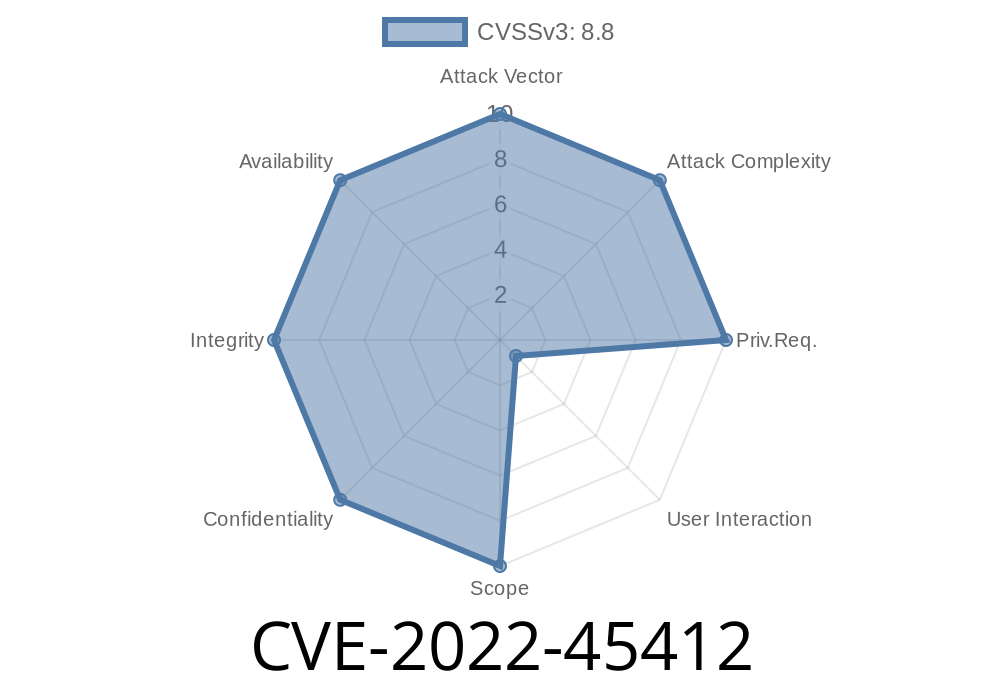
It is caused by a bug in the implementation of the ''enumerateSymbolicNameEntries'' method that is used by the ''FileSystemEnumerator'' to display the contents of a directory. On devices where Unix-based operating systems are installed, but where the user has disabled the creation of symbolic links, a denial of service attack can be performed by creating a symbolic link to ''../../proc/self/fd/0'', and then creating another symbolic link to ''../../proc/self/fd/1'' such that the contents of the second symbolic link are the contents of the first symbolic link. On such devices, the user needs to create a large number of symbolic links with the above specification in order to crash the device’s file system. This is also mitigated on Linux devices by defaulting to never creating symbolic links when processing directories, so the user needs to explicitly enable the creation of symbolic links using the ''--enable-symlinks'' command line option in order to exploit this vulnerability. On Android and MacOS devices, the user needs to explicitly install a Unix-based operating system in order to exploit this vulnerability. On Windows, the user can create a symbolic link to ''../../proc/self/fd/0'', and then create another symbolic link to ''../../proc/self/fd/1'' such that the contents of the second symbolic link are the contents of the first symbolic link. This can be done by
Details on how to exploit the vulnerability
The vulnerability can be exploited by creating a symbolic link to ''../../proc/self/fd/0'' and then creating another symbolic link to ''../../proc/self/fd/1''. On Unix-based operating systems, the user needs to explicitly enable the creation of symbolic links using the ''--enable-symlinks'' command line option in order to exploit this vulnerability.
Android and MacOS Devices
On Android and MacOS devices, the user needs to explicitly install a Unix-based operating system in order to exploit this vulnerability. On Windows, the user can create a symbolic link to ''../../proc/self/fd/0'', and then create another symbolic link to ''../../proc/self/fd/1'' such that the contents of the second symbolic link are the contents of the first symbolic link. This can be done by connecting an external storage device or hard drive that is formatted with a Unix-based operating system.
Dependencies
As in many other vulnerabilities, the vulnerability in this case requires that the user is able to create a file system on their own.
Timeline
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 01/05/2023 13:59:00 UTC