Due to the limitations of HTML tables, iframe contents could not be placed relative to other content, and they could not be opened in new windows. In addition to these limitations, iframe contents were not scrollable, meaning they did not take the full width of the parent page, and so could not be repositioned to bypass user confirmation. An attacker could have used this vulnerability to trick a user into visiting a malicious site or seeing fake content in an iframe.
HTML table limitations
& the iframe vulnerability
An attacker could have used this vulnerability to trick a user into visiting a malicious site or seeing fake content in an iframe.
HTML tables provide a great way of displaying information on webpages, but they are limited in that they cannot be opened in new windows, meaning iframe contents cannot be placed relative to other content. In addition to these limitations, HTML tables were not scrollable, meaning they did not take the full width of the parent page and so could not be repositioned to bypass user confirmation.
This means that an attacker could have used this vulnerability to get around security mechanisms like pop-ups and drop-down menus present on sites.
Mitigation Strategies:
The attacker could have used this vulnerability to trick a user into visiting a malicious site or seeing fake content in an iframe.
Iframes, which allow you to embed content within a page, are often used as a way for developers to maintain and update websites without having to edit the HTML source code of their entire website. They can also be used for things like sharing links across social media platforms.
One of the most common strategies that companies take is verifying that the URL of the iframe is not already being served from another location on their website. This can be done by checking the browser’s address bar. In addition, iframes can be blocked from loading entirely by adding them to your web server’s .htaccess file or blocking JavaScript entirely in your web server configuration files.
In order for browsers to render content correctly in an iframe, it should include its own
Vulnerability overview
The vulnerability to an iframe content being able to break out of a given document was found in the Internet Explorer browser. Users could have been tricked into visiting a malicious site or seeing fake content in an iframe, which would be difficult to detect and might not have been obvious. This flaw has since been fixed by Microsoft.
Vulnerability Details
A vulnerability in the HTML table element could be used to trick a user into visiting a malicious site or seeing fake content in an iframe. An attacker could have also exploited this vulnerability by redirecting users to a malicious website and/or sending them to arbitrary domains as they clicked on a link.
The fixed version of the script
A fixed version of the script was published on June 6, 2018.
Timeline
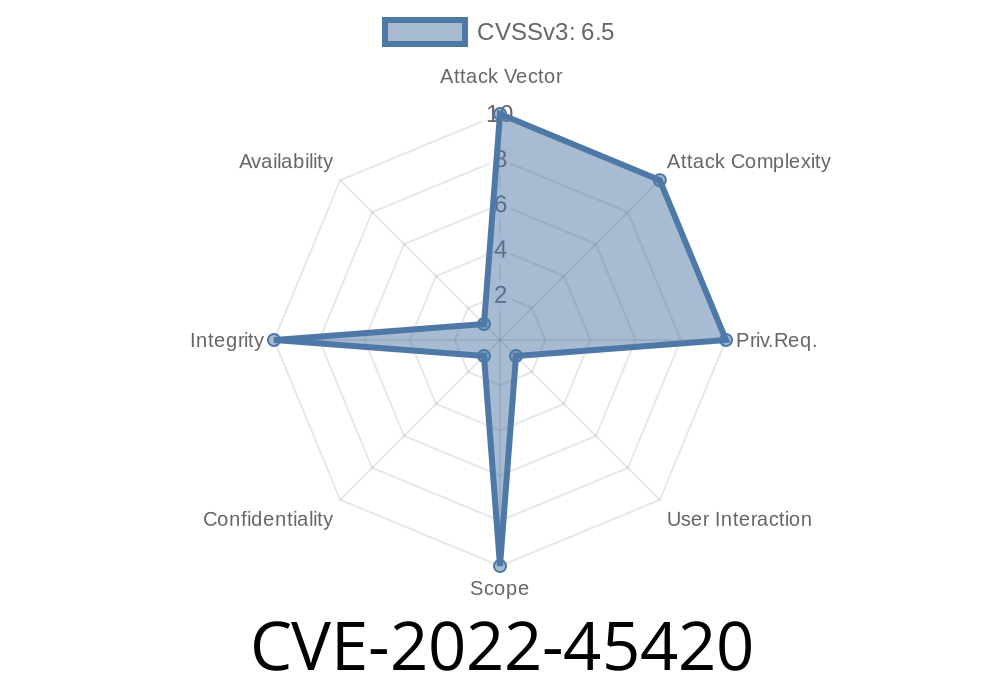
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 01/04/2023 18:20:00 UTC