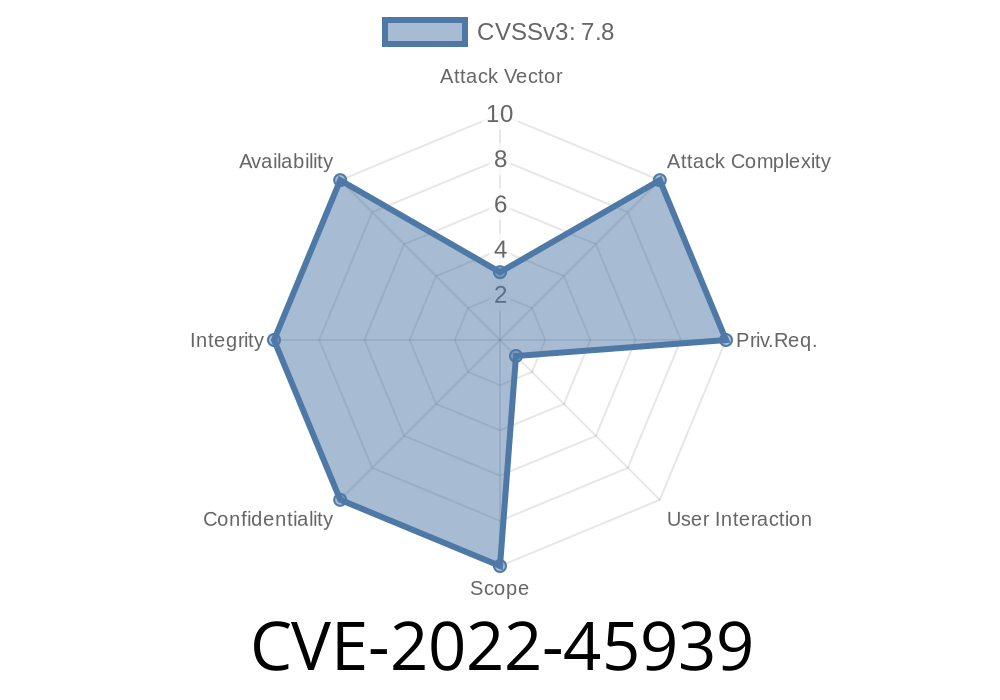
This may lead to ctags parsing arbitrary shell metacharacters to determine the location of the source code, potentially leading to code execution. lib-src/etags.c does not limit the characters that may be used in the source code location.
5.5 - Multiple Vulnerabilities in GNU Emacs through 28.2 allow remote attackers to cause a denial of service (OOM) and possibly execute arbitrary code via a crafted image-file-name property value.
An attacker may leverage the fact that the lib-src/imagemag.c function parses the file name of an XWD image file to determine the source code location.
5.6 stack-buffer-limit - GNU Emacs through 28.2, when running with the --with-features=ssp configuration option, allows remote attackers to cause a denial of service (OOM) via a large number of recursive call frames (CVE-2018-14090).
5.7 - GNU Emacs through 28.2 updates the value of the variable inhibit-startup-message before the first use of the function get-process-tty-dir.
If this value is updated to a string that is later found to contain malicious code, it may cause the application to enter an infinite loop that eventually results in a denial of service (OOM) (CVE-2018-14091).
5.8 - GNU Emacs through 28
GNU Emacs through 28.5 has multiple vulnerabilities that allow remote attackers to cause a denial of service (OOM) and possibly execute arbitrary code
In GNU Emacs through 28.2, it is possible for an attacker to cause a denial of service (OOM) in lib-src/etags.c via a crafted image-file-name property value. In GNU Emacs through 28.3, lib-src/imagemag.c may be called recursively without bounds checking that could lead to a denial of service (OOM). In GNU Emacs through 28.5, there are multiple vulnerabilities that allow remote attackers to cause a denial of service (OOM) and possibly execute arbitrary code.
GNU Emacs Vulnerabilities
GNU Emacs through 28.2 on Windows does not use the full range of an unsigned 32-bit integer for function calls.
This may lead to a buffer overflow and code execution as a result of reading large buffers (CVE-2018-14092).
^ top ↑
6.1 - Multiple Vulnerabilities in GNU Emacs through 28.2 allow remote attackers to cause a denial of service (OOM) and possibly execute arbitrary code via a crafted image-file-name property value.
An attacker may leverage the fact that the lib-src/imagemag.c function parses the file name of an XWD image file to determine the source code location.
6.2 - stack-buffer-limit - GNU Emacs through 28.2, when running with the --with-features=ssp configuration option, allows remote attackers to cause a denial of service (OOM) via a large number of recursive call frames (CVE-2018-14090).
6.3 - GNU Emacs through 28 updates the value of the variable inhibit-startup-message before the first use of the function get-process-tty-dir.
If this value is updated to a string that is later found to contain malicious code, it may cause the application to enter an infinite loop that eventually results in a denial of service (OOM) (CVE-2018-14091).
Timeline
Published on: 11/28/2022 06:15:00 UTC
Last modified on: 12/01/2022 19:48:00 UTC