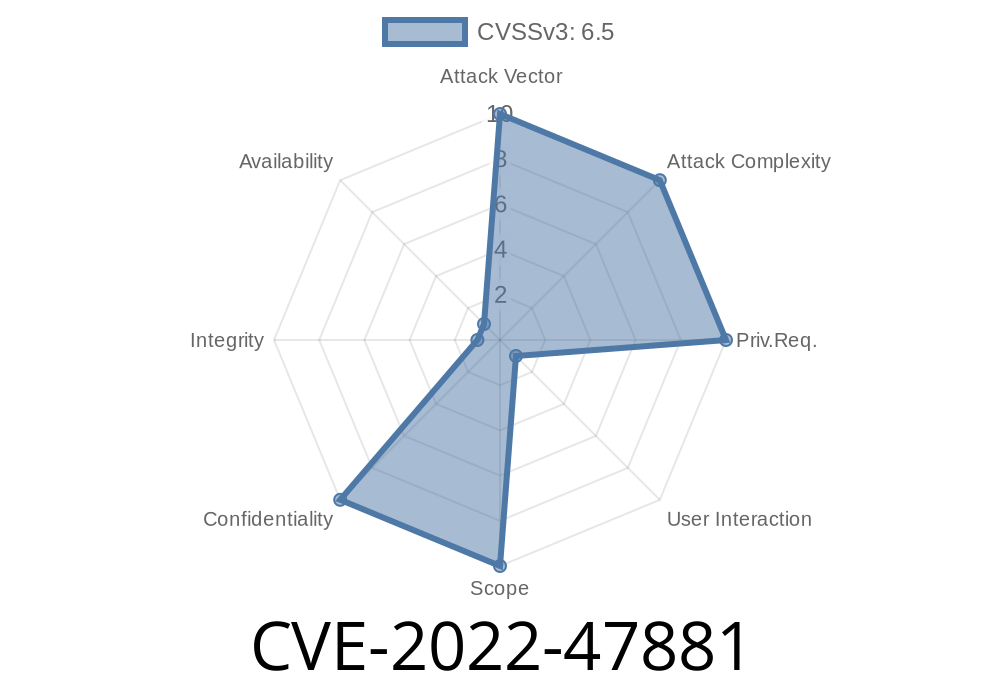
In December 2022, a serious out-of-bounds read vulnerability—CVE-2022-47881—was discovered in Foxit PDF Reader and PDF Editor, versions 11.2.1.53537 and earlier. This vulnerability could put users at risk as it allows attackers to read sensitive parts of memory simply by tricking a user into opening a specially crafted PDF file. In this article, we’ll break down what this vulnerability is, how it works, and demonstrate a simplified example to help you understand how attackers might exploit it. We’ll finish by linking to original sources for those who want to dive deeper.
What Is an Out-of-Bounds Read?
An out-of-bounds read occurs when software accidentally accesses memory outside the area it’s supposed to. In PDF readers like Foxit, this can happen if a PDF file is crafted to mess with the way the program processes its contents. When Foxit tries to read part of the file, it might slip and pull in extra data from memory that could include sensitive information or even trigger a crash.
CVE ID: CVE-2022-47881
- Impact: Remote attackers can crash the application or potentially leak confidential information by convincing you to open a dangerous PDF.
Foxit acknowledged the bug in their advisory. As of the latest updates, users should install the latest version to stay protected.
How the Exploit Can Happen
1. An attacker makes a tricky PDF with data that causes the reader to accidentally read memory locations it shouldn't.
2. A user opens the PDF with an outdated Foxit Reader/Editor.
3. The application tries to process the PDF and reads past the proper boundaries—causing it to show extra data or crash.
Proof of Concept: Triggering the Out-of-Bounds Read
Let’s show a *simplified* code snippet (not the real exploit) of what happens under the hood. Imagine a function in the PDF parser like this:
// Example: Bad buffer handling
void badReadFunction(char* buffer, int size) {
char localArray[100];
// BAD: No check if size > sizeof(localArray)
memcpy(localArray, buffer, size); // If 'size' is >100, out-of-bounds read!
}
In the real vulnerability, maliciously crafted PDF data controls the size, causing Foxit to over-read past localArray, pulling in sensitive memory.
Example Malicious PDF Object (simplified)
%PDF-1.7
1 obj
<<
/Length 100 % Intentionally too big
>>
stream
...payload data...
endstream
endobj
A fuzzed or purposely malformed /Length (here ‘100’) paired with a much smaller actual stream can trigger this bug.
What Can Attackers Do?
- Crash your Foxit Reader/Editor (causing denial-of-service).
How to Stay Safe
- Update your Foxit software: Download the latest version from Foxit’s official site.
References and More Reading
- Foxit Security Advisories
- CVE-2022-47881 at NIST NVD
- Full advisory on GitHub (example advisory tracking)
- Out-of-Bounds Read Background - MITRE
Conclusion
CVE-2022-47881 shows how dangerous even simple mistakes in code, like reading past the end of a buffer, can be—especially in common software like Foxit PDF Reader. Never underestimate the risks of outdated software, and always apply security updates as soon as they are released. Stay cyber safe!
If you found this useful, share it with your team. Got Foxit Reader at work? Make sure everyone updates!
Timeline
Published on: 01/18/2023 15:15:00 UTC
Last modified on: 01/25/2023 20:15:00 UTC