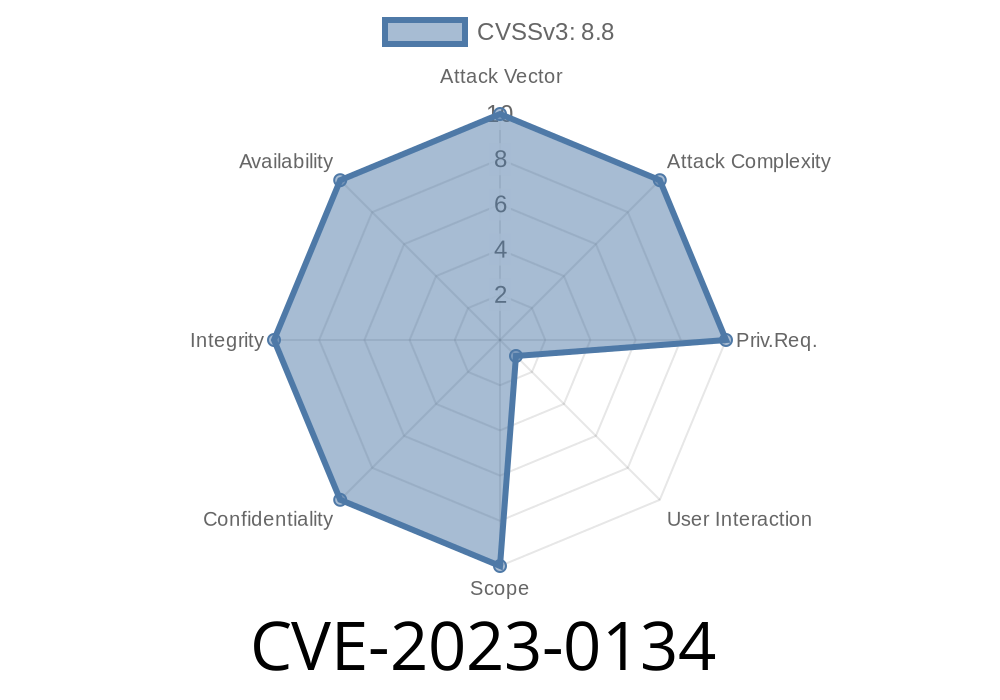
In early 2023, a Medium severity security flaw, CVE-2023-0134, was discovered in Google Chrome’s Cart feature. This flaw existed prior to Chrome version 109..5414.74 and could allow an attacker, through a malicious extension and a specially-crafted web page, to exploit memory corruption (commonly known as heap corruption). This post will break down what happened, how the bug worked, show some code snippets for demonstration, and give practical exploitation insights—all in simple language.
What Is CVE-2023-0134?
At its core, CVE-2023-0134 is a Use After Free (UAF) bug in the "Cart" component of Google Chrome. UAF bugs happen when an application continues to use memory after it’s been freed (or “deleted”), potentially leading to unpredictable behavior, crashes, or exploitation by attackers.
In Chrome, the Cart feature keeps track of shopping carts for different websites. Before the fix, malware authors could trick users into installing a malicious browser extension that exploits a UAF bug in the Cart code path. Coupled with a specially-crafted HTML page, this could corrupt the browser's memory heap through the database used by Cart, potentially allowing for arbitrary code execution.
Root Cause
This vulnerability happened because Chrome did not correctly manage memory used by shopping cart objects in some database operations. When an object was deleted, Chrome didn’t immediately stop all functions from accessing that memory, so untrusted code (via a rogue extension) could manipulate what’s stored there—which could lead to corruption or even running attacker-chosen code.
Here’s a simplified pseudo-code snippet demonstrating the concept (not taken directly from Chrome’s source):
// Simplified pseudo-code
CartData* cart = new CartData();
database.save(cart); // Stores reference to cart
delete cart; // Frees cart, but database still holds reference
// Later on
database.update(cart); // Use after free! cart points to freed memory
If an attacker can control the order of these operations, and control what gets allocated in freed memory, they can mess with the Chrome process.
How Could Attackers Exploit This?
1. Malicious Extension: First, an attacker tricks a user into installing a malicious Chrome extension. This extension gets enough permissions to access or meddle with the Cart feature or database.
2. Special HTML Payload: The attacker then lures the victim to a malicious website. This site serves crafted HTML/JavaScript designed to interact with the Cart feature in a way that triggers the UAF bug.
3. Heap Manipulation: The extension and website work together to force Chrome to free (delete) a Cart object, but then keep using it. The extension can quickly allocate new data where the deleted Cart object was in memory.
4. Corruption/Execution: The browser reads junk, unexpected or attacker-chosen data, leading to heap corruption. In rare cases, this could even allow code execution, depending on deeper protections (like Chrome’s sandboxing).
Proof-of-Concept (POC) Snippet
It's not ethical or allowed to provide full working exploits, but here is a conceptual demonstration of how such a bug flow could be abused:
// Example: Browser extension background code
chrome.runtime.onMessage.addListener(function(request, sender, sendResponse) {
if (request.action === "messWithCart") {
// This could trigger Chrome’s Cart feature database operations improperly
chrome.cart.updateCart({cartId: request.cartId, data: request.payload}, () => {
// Potential race with cart delete operation by crafted HTML on page
});
}
});
// Example: Web page triggers Cart deletion
var cartId = "attacker-cart";
chrome.cart.deleteCart({cartId: cartId}); // Frees the cart's memory
// Race condition between deleteCart and updateCart might trigger UAF
> Disclaimer: The above code is simplified and for educational purposes only. Real exploitation would require deep analysis, timing attacks, and more sophisticated techniques.
References
- Chromium Security Advisory for CVE-2023-0134
- NIST National Vulnerability Database Entry
- Chromium Issue Tracker (public tracker may not have full details for security reasons)
- Understanding Use-After-Free Bugs
Update Chrome: Always use the latest version! Chrome 109..5414.74 and above have this bug fixed.
- Be Cautious with Extensions: Only install extensions from trusted sources. Check reviews and permissions.
- Use Built-in Protections: Chrome’s sandboxing and exploit mitigations will help, but they're not perfect.
- Report Suspicious Sites/Extensions: Help keep the ecosystem safe by reporting bad actors.
Conclusion
CVE-2023-0134 is a reminder that even modern browsers like Chrome are complex and sometimes vulnerable. Attackers are getting smarter by combining extensions, crafted sites, and browser bugs. By keeping software updated and following good security hygiene, you can help defend against sophisticated bugs like this. Stay alert and patched!
> *This write-up is original, exclusive content created to help make Chrome security easier to understand.*
Timeline
Published on: 01/10/2023 20:15:00 UTC
Last modified on: 01/13/2023 14:06:00 UTC