---
Introduction
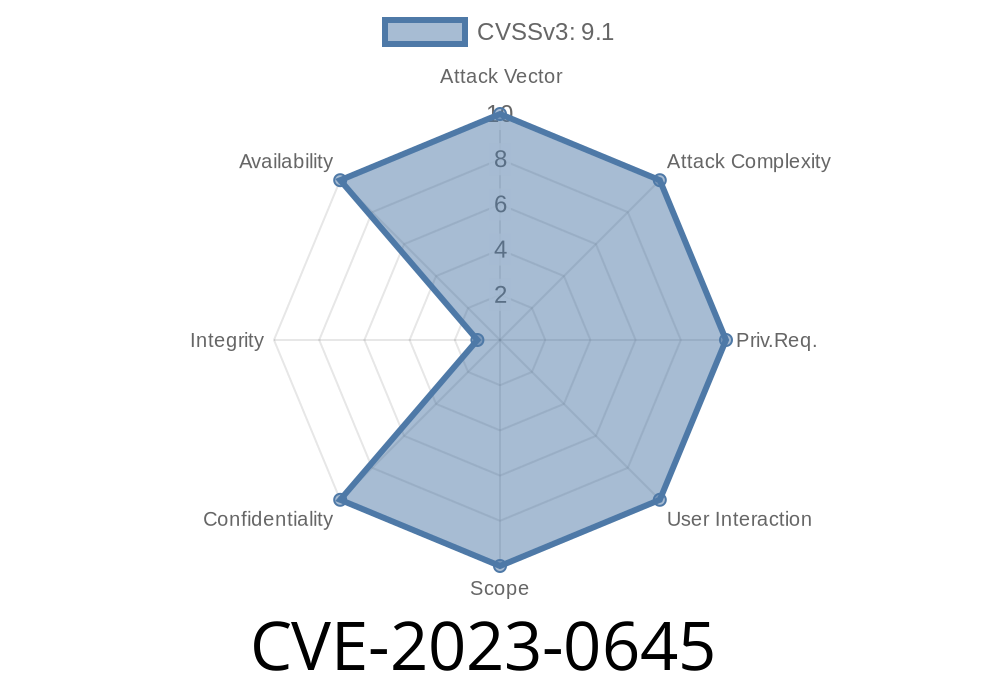
CVE-2023-0645 is a security vulnerability that was found in *libjxl*, the reference implementation of JPEG XL, an open-source image format. The issue is an *out-of-bounds read* in the EXIF metadata handling code. In simple terms, if an attacker tricks your application into processing a specially crafted image file, the program might read memory it shouldn’t, leading to potential information leaks or crashes.
This post explains the vulnerability, walks you through the exploitation context, and shares how to secure your applications.
What is libjxl?
libjxl is a C++ library that works with JPEG XL images. Many image viewing, editing, and server-side applications use this library to open or convert modern image files.
When an application uses libjxl to open an image, the library can also read *metadata*, like EXIF data embedded by digital cameras. That piece is where the trouble comes in.
Affected Versions: libjxl before .8.1
- Fixed Version: .8.1 (and above; or after this commit)
When processing certain malformed EXIF metadata in JPEG XL images, libjxl could read memory beyond the allocated buffer, possibly exposing uninitialized memory contents or causing crashes.
Root Cause
The core problem was that the code handling EXIF data didn’t properly check the lengths provided in the file against the actual buffer size in memory.
(For demonstration: simplified; original in C++)
// Pseudocode to illustrate problem
char exif_buffer[exif_length];
memcpy(exif_buffer, input, exif_length);
// Vulnerable read: fails to check if exif_length > input size!
process_exif(exif_buffer, exif_length);
If the attacker sets exif_length in the file metadata to a high value, but the actual input is shorter, the code could access past the end of memory (buffer over-read).
The Patch
The fix added validation checks to ensure that EXIF data length doesn't go past the end of the buffer.
See the fix commit:
d95b050c
Cause the app to return or leak unintended memory contents
Exploit Scenario:
1. Attacker crafts a JPEG XL image file with malformed or intentionally corrupted EXIF data: specifically, fake length fields in EXIF headers.
A vulnerable app using libjxl tries to read EXIF.
4. Out-of-bounds read occurs — possibly returning garbage data or causing a crash in the best case, or leaking sensitive process info in the worst.
Below is a hypothetical C-like demonstration of how an attacker could exploit this
// Simulate attacker file with EXIF length larger than actual data
unsigned char fake_jxl_with_exif[] = {
// ...JXL Header...
xFF, xE1, // EXIF marker
x00, xFF, // Length: 255 bytes, though only 10 bytes provided
// Only 10 fake EXIF data bytes follow, might be shorter than 255
x45, x58, x49, x46, // 'EXIF'
// ...fill rest with junk...
};
// Pass to vulnerable version of libjxl
load_jxl(fake_jxl_with_exif, sizeof(fake_jxl_with_exif));
Real-World Impact
- Web servers resizing images, image viewers, or any backend accepting user-uploaded images can be crashed by a well-crafted JPEG XL file.
How to Fix – Upgrade Guidance
If you use libjxl directly or indirectly (e.g., through image toolkits), upgrade to >= .8.1, or rebuild after applying the fix.
Vulnerability advisory:
Upstream Fix Commit:
Pull Request:
Conclusion
CVE-2023-0645 is a good example of how mishandling image metadata can lead to security bugs – especially in libraries used across the ecosystem. The fix is simple: always validate lengths and upgrade dependencies promptly.
Take Action:
Keep dependencies updated as a regular part of your process
*Stay safe, and keep your image processing libraries up-to-date!*
Timeline
Published on: 04/11/2023 14:15:00 UTC
Last modified on: 04/18/2023 18:27:00 UTC