---
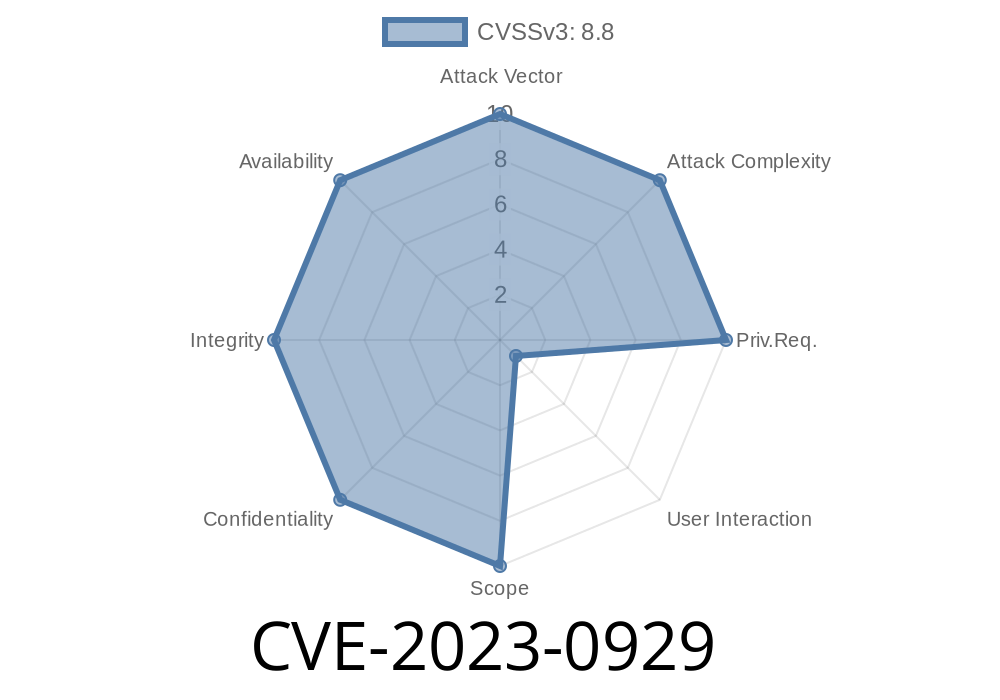
*In early 2023, security researchers discovered a severe vulnerability in Google Chrome’s handling of the Vulkan graphics API. Marked as CVE-2023-0929, this flaw could let remote attackers execute potentially harmful code on your computer just by getting you to visit a specially crafted web page.*
What is CVE-2023-0929?
CVE-2023-0929 is a *use-after-free* vulnerability found in Chrome’s implementation of the Vulkan graphics API. It affected Chrome browsers before version 110..5481.177.
In short: Chrome used memory after it was freed, meaning hackers could slip in malicious data at just the right time, leading to heap corruption. In the worst case, it allowed remote code execution in the context of the logged-in user.
Component: Vulkan (GPU)
- Patched in: Chrome 110..5481.177
Use-After-Free 101
In programming, “freeing” memory means telling the system, “I’m done with this, you can reuse it.” If the program keeps referencing that memory after it’s marked free, an attacker could sneak in and control what’s there.
The Vulkan Exploit Scenario
Chrome’s Vulkan implementation had a code path where a specific event (like destroying a VkObject) could cause the browser to "free" a chunk of memory, but some parts of the browser would keep using pointers to that dead memory. If an attacker can influence what happens next (e.g., by using certain JavaScript or HTML), they could trigger Chrome to operate on compromised memory, paving the way to run arbitrary code.
Typically, an attacker would
1. Create a Web Page: The attacker creates an HTML page using WebGPU/WebGL features or specially crafted canvas elements that interact with Vulkan via Chrome’s GPU process.
2. Trigger the Free: Through precise JavaScript, attack code triggers Chrome to free a crucial Vulkan object.
3. Occupy Freed Memory: They quickly allocate new data—ideally, something under their control—replacing the old Vulkan object, right in the spot the browser still believes is safe.
4. Hit the Use Point: The browser tries to use the freed object, but it’s now using malicious data, possibly redirecting virtual function calls or corrupting internal structures.
5. Profit: Depending on browser sandboxing/mitigations, this can lead to executing attacker code or gaining access to private data.
Code Example (Proof of Concept)
Here’s a simplified PoC (for educational demonstration only—actual exploitation is far more complex):
// Fake PoC to demonstrate the logic of use-after-free via repeated GPU resource creation & deletion:
for (let i = ; i < 10000; i++) {
let canvas = document.createElement('canvas');
let ctx = canvas.getContext('webgl2');
// Allocate a GPU resource
let buffer = ctx.createBuffer();
ctx.deleteBuffer(buffer); // triggers the "free"
// Heap spray: Try to fill the heap with controlled data
let arrs = [];
for (let j = ; j < 100; j++) {
arrs.push(new Array(100).fill('owned_by_attacker'));
}
}
// Under rare conditions, Chrome could use the freed buffer (now filled with attacker data)
WARNING: This simplified code does NOT exploit the vulnerability directly; it demonstrates techniques often used in browser exploitation around *use-after-free* bugs.
Real-World Impact
- Remote Code Execution: Visiting a malicious site could have been enough for attackers to silently gain access to your machine.
No User Interaction Needed: No download, no click—just browsing was enough.
- Works Across OSes: Because Chrome's Vulkan support runs on multiple platforms, the bug affected Windows, Linux, and possibly others.
Fixes and Mitigation
The Chrome team quickly patched the bug—always ensure your browser is up to date!
If you’re building enterprise or embedded systems with Chromium, review your code for similar patterns and keep auto-updates enabled.
- Google’s Official Security Advisory
- Chromium Issue Tracker #1413054 *(Access might be limited)*
References
- Chromium Security Blog
- Chromium Exploit Details CVE-2023-0929 on NVD
- Vulkan Graphics API Official Site
Bottom Line
CVE-2023-0929 was a high-severity “use-after-free” bug in Chrome’s GPU code. You were at risk if you used Chrome before version 110..5481.177 and visited a hacker’s webpage. Always keep your browser updated and, if you’re a developer, study use-after-free bugs because they’re a top target for attackers.
Timeline
Published on: 02/22/2023 20:15:00 UTC
Last modified on: 02/28/2023 02:20:00 UTC