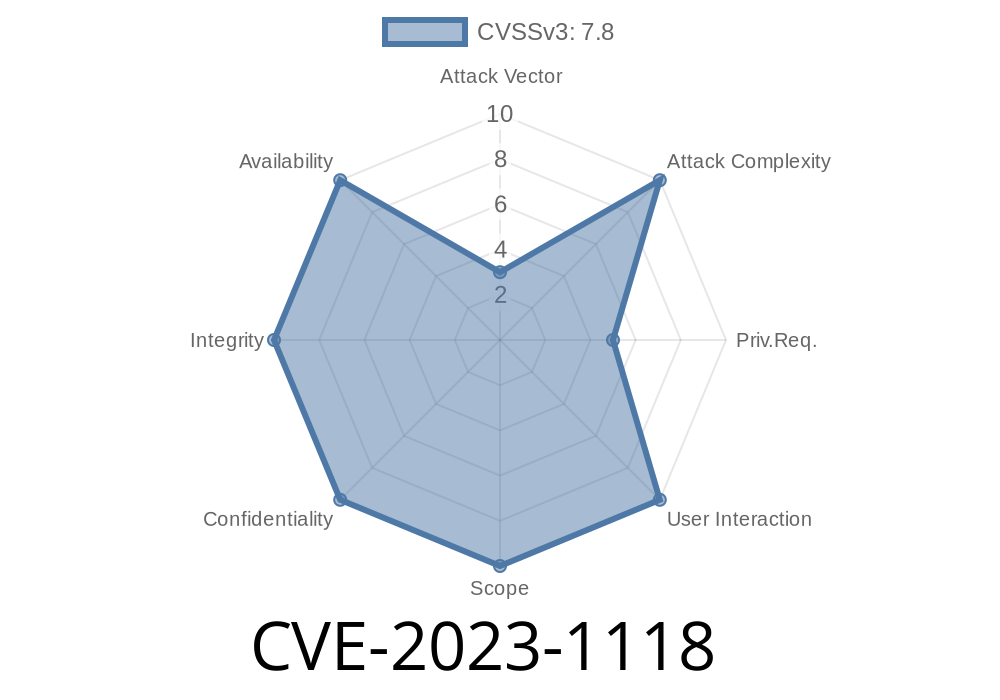
In early 2023, a significant vulnerability, CVE-2023-1118, was discovered in the Linux kernel. This flaw affects the integrated infrared receiver/transceiver (IR) driver—also known as the remote control (RC) subsystem. A use-after-free issue allows local users to crash the system or, in some cases, elevate privileges. In this article, we’ll break down the bug in simple terms, look at code samples, analyze potential exploit scenarios, and share resources for further reading.
What is a Use-After-Free Vulnerability?
A use-after-free occurs when a program continues to use a pointer after the underlying memory has been released (“freed”). This can allow attackers to mess with the program’s execution by injecting malicious data or code into that memory region.
Picture this:
But later, you try to write on that same notepad (use it).
- Someone else (the attacker) might have fished it from the trash and scribbled something nasty on it...
Details of CVE-2023-1118
The flaw sits in the way the Linux kernel handles the detachment of IR receiver/transceiver devices (RC devices). If a local user detaches an RC device at the wrong time, certain kernel structures get freed while they’re still accessible. This window can be leveraged to either crash the kernel (Denial of Service) or possibly run code with higher privileges.
Let’s look at a simplified version of the problematic driver code
struct rc_dev {
// ... device data ...
};
void rc_unregister_device(struct rc_dev *dev) {
// Some cleanup code
mutex_lock(&rc_dev_list_lock);
list_del(&dev->list);
mutex_unlock(&rc_dev_list_lock);
// Calls to input_unregister_device() can trigger
// callbacks that still use 'dev'
input_unregister_device(dev->input_dev);
// At this moment, 'dev' could already be freed,
// but something might still try to access it!
kfree(dev);
}
When input_unregister_device() is called, callbacks in other parts of the kernel may still refer to dev, even though it is about to be freed.
Real Patch Reference
Check out the real fix in the official Linux kernel commit:
👉 Commit: rc-core: avoid use-after-free on IR raw event
Exploit the freed memory by placing controlled data (heap grooming)
4. Cause the kernel to follow a pointer from freed memory, potentially executing malicious code or causing a crash
Example Exploit Outline
Here’s a high-level pseudocode sequence (not a real exploit, for educational purposes)
import os
import time
def detach_device():
# Simulate detaching an RC device
os.system("echo 1 > /sys/class/rc/rc/device/remove")
def spam_rc_events():
# Simulate sending RC events rapidly
for i in range(10000):
os.system("ir-ctl -S 'KEY_POWER' -d /dev/rc")
time.sleep(.01)
# Simulate race between detaching and events
from threading import Thread
Thread(target=detach_device).start()
Thread(target=spam_rc_events).start()
*NOTE*: This is a sketch! A real exploit is more complex, involves precise timings, and may depend on kernel version.
How It Was Fixed
Developers changed the teardown sequence so the kernel does not free the rc device until all users and callbacks are fully done with it. Memory is now freed only after everyone is done.
Original Red Hat Security Advisory:
https://access.redhat.com/security/cve/CVE-2023-1118
NVD Entry (National Vulnerability Database):
https://nvd.nist.gov/vuln/detail/CVE-2023-1118
Upstream Linux Kernel Patch:
https://github.com/torvalds/linux/commit/bbe3c4161b1e67c4f7b1db9ef6d03fa117efa51
Kernel Bug Tracker:
https://bugzilla.kernel.org/show_bug.cgi?id=217045
Conclusion
CVE-2023-1118 is a classic example of how subtle bugs in device driver code can lead to serious kernel-level vulnerabilities. If you manage a Linux system or distribution, check your kernel version and update if you might be affected. As always, keep local access locked down and stay alert for patches to keep your systems safe!
Timeline
Published on: 03/02/2023 18:15:00 UTC
Last modified on: 05/03/2023 14:15:00 UTC