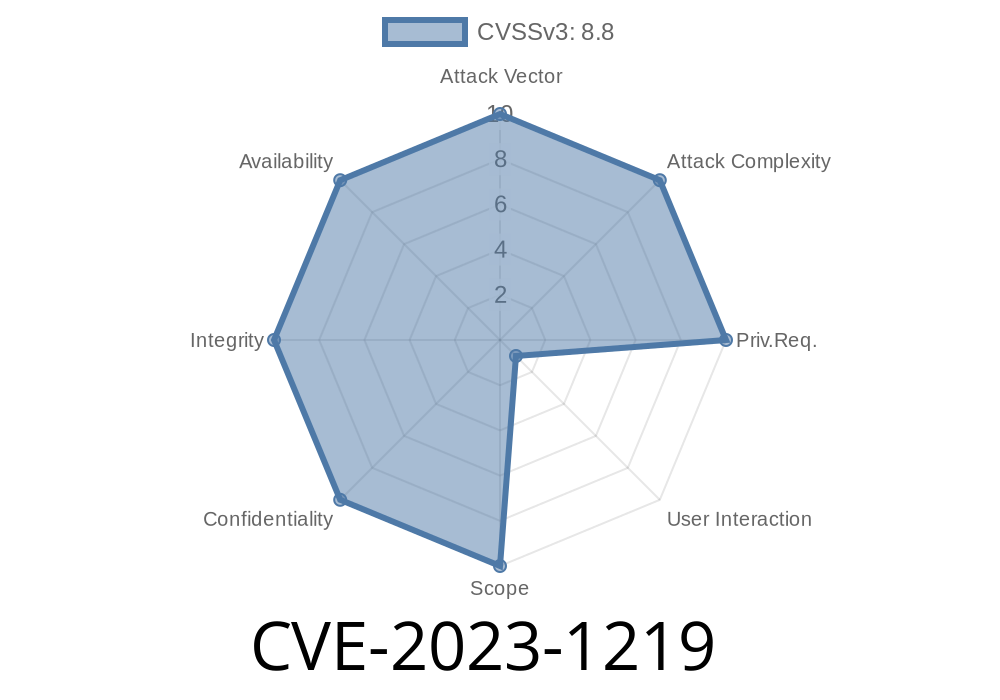
In early 2023, a significant security vulnerability surfaced in Google Chrome’s rendering engine, Chromium. Identified as CVE-2023-1219, this bug falls into the “heap buffer overflow” category and affects Chrome versions before 111..5563.64.
This post explains what happened, how attackers could exploit it, and includes demonstration code. The focus is on simple, clear explanations for both beginners and pros.
What is a Heap Buffer Overflow?
Heap buffer overflow occurs when a program writes more data to a heap-allocated buffer than it can hold. Memory corruption follows, potentially letting attackers inject code, read confidential data, or crash the program.
Versions affected: Chrome < 111..5563.64
- Exploit Range: Requires compromise of the renderer process (e.g., via malicious HTML/JS)
Outcome: Heap corruption — may lead to arbitrary code execution
Original advisory:
- Google Chrome Releases: Stable Channel Update for Desktop (March 7, 2023)
- Chromium issue #1413647
Vulnerability Details
The bug lies in how Chrome collects and processes internal metrics—statistics and telemetry involving browser performance. Improper handling of buffer sizes allows a compromised renderer to trigger a buffer overflow in memory allocated on the heap.
Why is That Bad?
If a malicious web page compromises the renderer (for instance, via an earlier renderer bug), this overflow could corrupt memory structures, giving the attacker additional capabilities, such as escaping the renderer sandbox (a key security boundary).
Exploitation Path
This bug is post-renderer-compromise, meaning the attacker must already have code execution in the renderer process. Attackers chain this with a renderer exploit:
1. Send malicious HTML/JavaScript to trigger a renderer bug.
Example Exploit Snippet
*Note: This is a demonstration to explain the method, not a working exploit.*
Suppose the vulnerable Chromium code looks like this
// Pseudo-code for vulnerable Chrome Metrics function
void ProcessMetricData(char* data, size_t size) {
char* buffer = (char*)malloc(100); // 100 bytes allocated
memcpy(buffer, data, size); // size not checked!
// ...
}
A compromised renderer could send a data buffer larger than 100 bytes, causing memcpy to overwrite beyond buffer and corrupt adjacent heap memory.
Exploit Example (Pseudocode)
// Malicious renderer code sends oversized metric packet
let oversizedData = new ArrayBuffer(1024); // >100 bytes
// Fill with controlled content, possibly ROP payload or object overwrite
let u8 = new Uint8Array(oversizedData);
for (let i = ; i < u8.length; i++) {
u8[i] = x41; // Arbitrary data or crafted pointers
}
// Send to browser process via the metrics interface
chrome.metrics.sendData(oversizedData);
The attacker’s data will overflow the heap buffer in the browser process, with the contents packed to suit a secondary attack, such as control-flow hijack, data leakage, or privilege escalation.
## Patch/Resolution
Regression tests to catch future occurrences.
Patch diff:
Chromium Gerrit - Patch for bug 1413647
Update Chrome regularly. Most users will be updated automatically, but it never hurts to check.
2. Avoid suspicious sites. Don’t visit links from untrusted sources or install odd browser extensions.
3. Learn about renderer process security. Chrome’s multi-process model is your friend but isn’t bulletproof!
Useful References
- CVE-2023-1219 (NVD)
- Chromium Issue Tracker: Bug 1413647
- Chrome Security Architecture
- Google Chrome Release Notes
Summary
CVE-2023-1219 is a classic heap buffer overflow, made more serious by its role in potential sandbox escapes. While chaining such bugs demands skill, the consequences highlight why browser vulnerabilities draw heavy interest from attackers.
Keep your browser up to date, and remember: even with sandboxing, no single layer of defense is ever enough.
*For any questions or a deeper dive, feel free to comment below!*
Timeline
Published on: 03/07/2023 22:15:00 UTC
Last modified on: 04/10/2023 20:15:00 UTC