---
Introduction
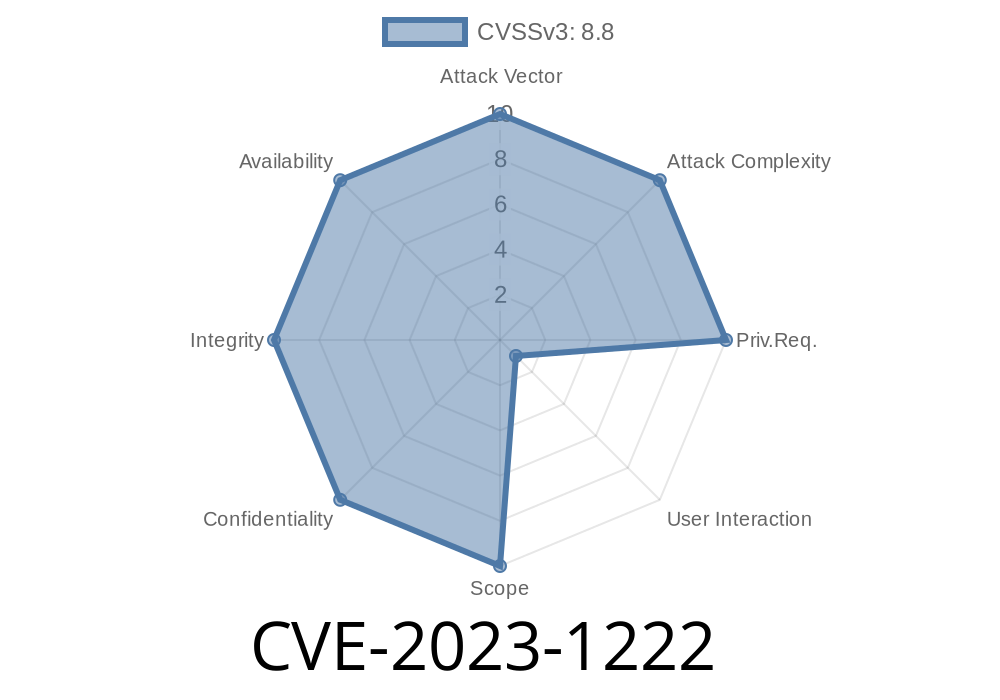
In early 2023, Google patched a significant security vulnerability in Chrome’s famous Web Audio API. Known as CVE-2023-1222, this flaw allowed remote attackers to potentially exploit heap buffer overflow through a crafted HTML page. In this post, we’ll walk through what this vulnerability means, how it can be exploited, and provide easy-to-read code snippets and relevant references.
What Is CVE-2023-1222?
At its core, CVE-2023-1222 is a heap buffer overflow bug in the Web Audio API implementation of Chromium browsers, including Google Chrome. This affected versions of Chrome prior to 111..5563.64.
- Impact: Remote attacker could cause heap corruption, which could lead to arbitrary code execution in the context of the browser (user’s privileges).
Reference links
- Chrome Release Notes (v111 Security Fixes)
- Chromium Security Advisory
1. The Web Audio API
The Web Audio API lets web developers run complex audio operations in browsers. It uses audio buffers, which are basically large blocks of memory allocated for audio data processing.
2. The Vulnerability
The bug exists in how Chrome handles AudioBuffer objects and their underlying memory. When certain crafted values are passed, Chrome would fail to properly verify the buffer size or out-of-bounds access, leading to a write or read outside the allocated memory.
If exploited, an attacker could corrupt heap memory—disrupting the browser’s control flow, potentially leading to execution of malicious code.
Proof of Concept (PoC) Code Snippet
Here is a simple, illustrative version of HTML/JavaScript code that manipulates the Web Audio API. Please note that this snippet is for EDUCATIONAL PURPOSES only. It demonstrates dangerous APIs where such vulnerabilities could arise:
<!DOCTYPE html>
<html>
<body>
<script>
// Allocate a large AudioBuffer by manipulating sampleRate and length
var audioCtx = new (window.AudioContext || window.webkitAudioContext)();
// Dangerous: Large number could trigger overflow in vulnerable Chrome builds!
var length = 2**30; // Huge buffer length
var channels = 2;
try {
// Before patch: This could trigger the heap overflow
var myArrayBuffer = audioCtx.createBuffer(channels, length, audioCtx.sampleRate);
// Fill buffer with data (potentially triggering out-of-bounds write)
for (var channel = ; channel < channels; channel++) {
var nowBuffering = myArrayBuffer.getChannelData(channel);
for (var i = ; i < length; i++) {
nowBuffering[i] = Math.random() * 2 - 1; // Random audio data
}
}
alert("Audio buffer created and filled (didn't crash!)");
} catch (e) {
alert('Error: ' + e);
}
</script>
</body>
</html>
Note: In Chrome prior to 111..5563.64, this code could crash the browser, cause unexpected behavior, or (if properly weaponized) perform heap corruption.
Exploit Breakdown
1. Craft a Malicious HTML Page: The attacker lures the victim to a website using code similar to the above PoC, but engineered more precisely for memory layout.
2. Trigger Heap Overflow: By passing large or malformed values to AudioContext.createBuffer(), the code causes the underlying C++ code to allocate insufficient memory for the buffer, then wildly overfills it.
3. Heap Corruption: Heap buffer overflow allows the attacker to overwrite adjacent heap memory—sometimes including function pointers or object metadata.
4. Possible Code Execution: With luck and skill (and/or another info leak), the attacker could execute arbitrary code, steal browser data, or further escalate privileges.
Real-World Exploitability
- Practical exploit: A straightforward crash (denial of service) is possible. Full code execution may require chaining with other vulnerabilities, like info leaks, and is harder due to modern browser mitigations.
- Scope: Only affects Chrome versions before 111..5563.64 (March 2023). Users running newer versions are safe.
Responsible Disclosure & Patching
Google credited Sebastian Aigner of JetBrains for reporting the bug. The patch improved buffer size validation and out-of-bounds checks.
UPGRADE NOW: If you haven’t yet, update your Chrome browser!
Learn More
- Official Chrome Release Blog
- Chromium Bug Report 1411185 (may be partially restricted)
- OWASP: Buffer Overflow
Summary
CVE-2023-1222 reminds us that even widely used APIs like Web Audio can become attack surfaces if not properly validated. Always keep your software updated and be wary of unexpected behaviors on sketchy websites.
Timeline
Published on: 03/07/2023 22:15:00 UTC
Last modified on: 03/11/2023 02:38:00 UTC