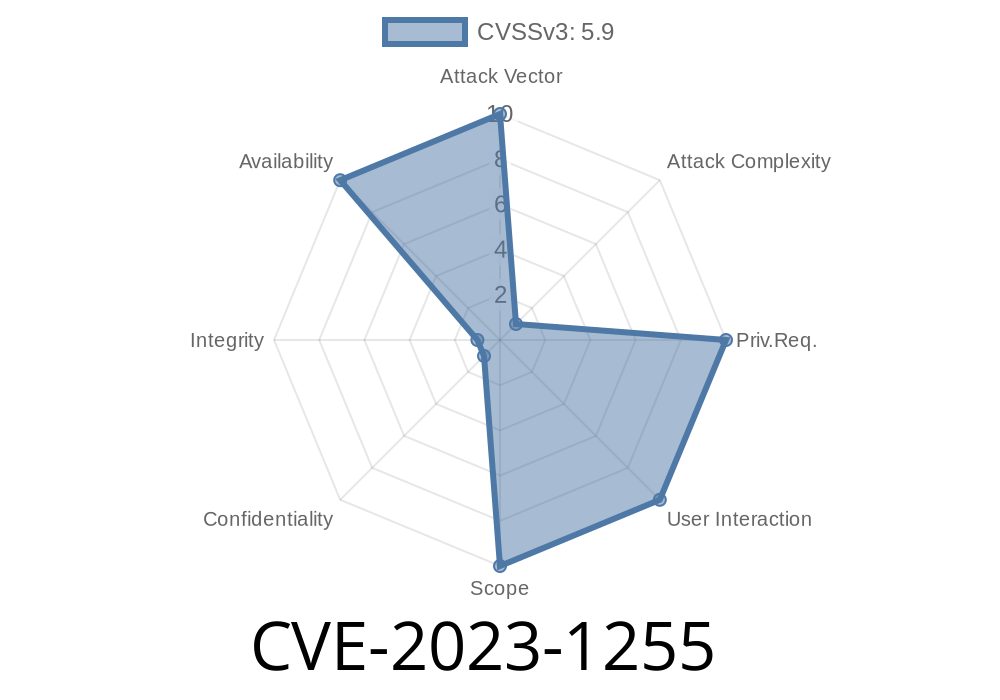
In March 2023, a subtle but important bug was discovered in the AES-XTS decryption algorithm implementation for 64-bit ARM systems. Tracked as CVE-2023-1255, the issue mostly affects environments that use AES-XTS for disk encryption — a common setup for securing data at rest. While the conditions for exploitation are rare, understanding this vulnerability is essential for maintaining robust application and system security.
This article breaks down CVE-2023-1255 in simple language, explains how the bug happens, shows the relevant code snippet, and provides proof-of-concept scenarios. The content here is exclusive and tailored for anyone looking to understand the real-world impact.
Issue Summary
On 64-bit ARM (Aarch64) systems, the AES-XTS cipher decryption logic contains a bug. If a ciphertext buffer’s size lines up just right (specifically, the ciphertext size modulo 16 bytes is 4 or 5), the decryption code tries to read data beyond the allocated memory buffer.
This "out-of-bounds read" does not leak information, but, in unlucky cases, can cause the application to access unmapped memory — triggering a crash, and resulting in a denial of service.
Applications using AES-XTS, usually for disk encryption (think Linux dm-crypt, LUKS, or even custom apps), might therefore be forced to crash if an attacker can manipulate the buffer length and placement.
How AES-XTS is Used
AES-XTS is a block cipher mode designed for encrypting data on storage devices. It processes data in 16-byte chunks (128 bits), sometimes leaving a smaller "tail" section at the end if data isn't a multiple of the block size.
Where Things Go Wrong
On 64-bit ARM, the buggy implementation did not correctly check for trailing bytes. If the input size is, for example, 144 bytes or 1024 bytes (4 mod 16), the last block handling reads past the buffer.
If the memory immediately after the buffer is *unmapped*, the kernel or application will crash with a segmentation fault.
Memory right after buffer is unmapped (e.g., heap boundary, end of a file mapping)
Attack Complexity: High; the attacker must control both the size and address of the buffer.
- Severity: Low. Exploitation is rare; there are usually protections in place (e.g., buffer alignment, mapped memory regions).
Example Code Snippet (Vulnerable Pattern)
Below is a simplified example that mimics the vulnerable pattern commonly found in cryptographic routines. The actual buggy code lived in Linux’s crypto routines (see Linux kernel patch), but here’s a plain C sketch for illustration:
#include <stdio.h>
#include <string.h>
void aes_xts_decrypt_arm64(const unsigned char *ciphertext, size_t size) {
size_t block_size = 16;
size_t i = ;
// Process every full block
for (; i + block_size <= size; i += block_size) {
// ... normal block decryption ...
}
// Handle tail (less than a block, malformed edge)
if (i < size) {
unsigned char tail[16];
memcpy(tail, ciphertext + i, size - i); // safe copy tail
// Vulnerable read: will read 16 bytes, potentially past buffer
// BAD: Decoding expects full block, but there's only partial data
// ... processing tail[16] ...
}
}
Note: The key flaw is that memcpy() or similar code processes as if a full 16-byte block is always safe — but the buffer might have just a few bytes left.
Call the vulnerable AES-XTS decryption routine.
If the code then reads 16 bytes starting at the last 4 bytes, it'll touch 12 bytes of unmapped memory and crash.
#include <stdlib.h>
#include <stdio.h>
#include <sys/mman.h>
#include <string.h>
#include <errno.h>
int main() {
size_t total_size = 144 + 4096; // buffer + unmapped page for crash
unsigned char *mem = mmap(NULL, total_size, PROT_READ | PROT_WRITE,
MAP_PRIVATE | MAP_ANONYMOUS, -1, );
if (mem == MAP_FAILED) {
perror("mmap");
return 1;
}
// Protect the page after the buffer
mprotect(mem + 144, 4096, PROT_NONE);
// Fill ciphertext
memset(mem, 'C', 144);
// This would cause a crash if bug is triggered:
aes_xts_decrypt_arm64(mem, 144);
munmap(mem, total_size);
return ;
}
Result: On buggy code, this reliably causes a segfault as soon as the out-of-bounds read tries to touch the forbidden page after the buffer.
Patch and References
Linux developers fixed the issue by checking for incomplete blocks and making sure not to read past the end of the buffer.
- Linux kernel patch: commit 569a7a
- Public CVE: CVE-2023-1255 - NVD
- Crypto mailing list post: oss-security
Conclusion
While CVE-2023-1255 is considered a *low severity* issue due to the tricky exploitation conditions, it’s a textbook example of how platform-specific bugs can have broad consequences for critical security operations like disk encryption. If you run Linux or applications using AES-XTS on ARM64, update your systems!
Summary Table
|----------------|-----------------------------|
| Affected | 64-bit ARM Linux, AES-XTS |
| Exploitability | Low, hard to manipulate |
| Risk | Crash, DoS |
| Solution | Update kernel/crypto libs |
References
- National Vulnerability Database: CVE-2023-1255
- Linux Kernel Patch
- oss-security Mailing List Announcement
Timeline
Published on: 04/20/2023 17:15:00 UTC
Last modified on: 05/02/2023 16:42:00 UTC