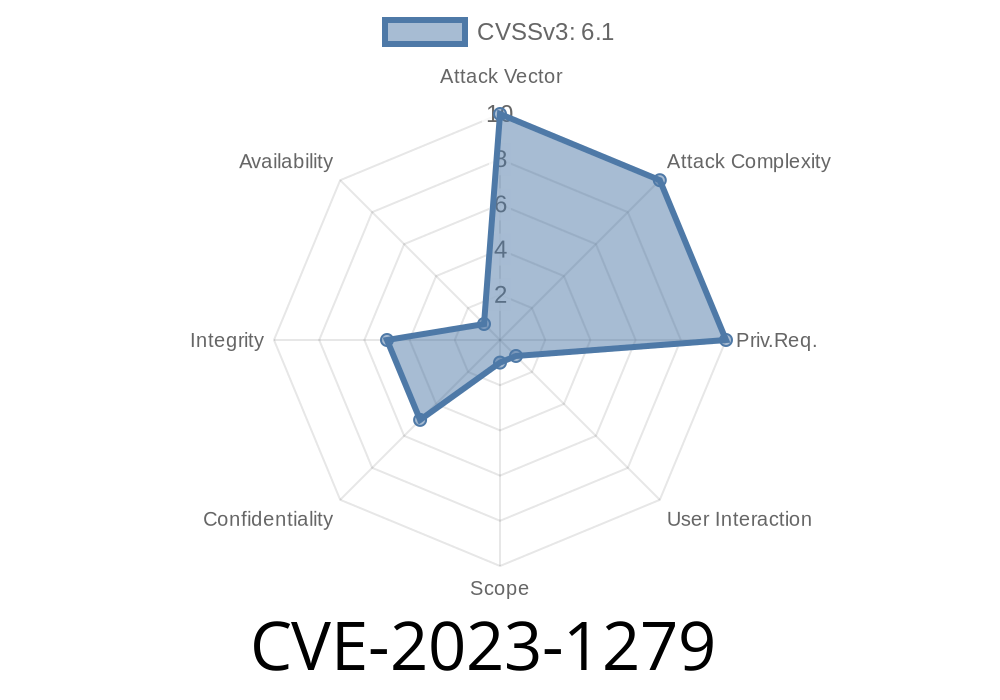
In March 2023, a security issue labeled CVE-2023-1279 was discovered in GitLab. This bug exposed a large number of GitLab instances to a "URL Redirection" risk, meaning attackers could trick users into going to malicious sites disguised as legit project URLs. Let’s break down what happened, look at the code, and walk you through the details of the exploit—using simple language.
What is CVE-2023-1279?
CVE-2023-1279 is an Open Redirect vulnerability in GitLab, a popular DevOps platform. This flaw exists in all GitLab versions starting from 4.1 up to 16.1.5, 16.2 up to 16.2.5, and 16.3 up to 16.3.1 (before patching!). The vulnerability allows an attacker to craft a special URL that appears to link to one GitLab project, but secretly redirects the user to a different, potentially harmful destination.
Why is Open Redirect Dangerous?
Open redirect bugs can seem harmless but actually help cybercriminals in phishing attacks. Imagine you click on a link that looks like:
https://gitlab.company.com/project/safe-project
But, thanks to the bug, the link silently sends you to
https://phishing.example.com/steal-your-password
Users trust the real site, so they're more likely to enter login information or other sensitive data.
GitLab Advisory:
https://about.gitlab.com/releases/2023/09/07/security-release-gitlab-16-3-1-released/
CVE Database:
https://nvd.nist.gov/vuln/detail/CVE-2023-1279
Digging Deeper – How the Exploit Works
When you visit certain pages in GitLab, if a *return_to* or *redirect_to* parameter is mishandled, you might be sent to an external or entirely different project.
Example Exploit URL
https://evil.com" rel="nofollow">https://gitlab.example.com/projects/legit-project?redirect_to=https://evil.com
If the "redirect_to" parameter isn't rigorously checked, GitLab forwards you straight to "https://evil.com" after you interact with the page—like logging in or clicking a provided link.
A simplified, NodeJS-like pseudocode to show you how open redirect bugs arise
app.get('/project/:name', function(req, res) {
// Vulnerable way
let redirectUrl = req.query.redirect_to;
if (redirectUrl) {
// BAD: Sends user to any URL provided
return res.redirect(redirectUrl);
}
// Normal project processing...
res.send('Welcome to Project: ' + req.params.name);
});
What’s wrong?
This code forwards the user to any URL given as redirect_to parameter, even if it's a dangerous site.
Proper code should validate the destination URL, making sure it's *inside* the GitLab domain
app.get('/project/:name', function(req, res) {
let redirectUrl = req.query.redirect_to;
if (redirectUrl) {
// Allow only local redirects
if (redirectUrl.startsWith('/')) {
return res.redirect(redirectUrl);
}
// Optionally, ignore or show error for external URLs
}
res.send('Welcome to Project: ' + req.params.name);
});
Phishing: Sends a link like
https://gitlab.com/project/real?redirect_to=https://bad.com
(users think it's safe because it's from a real organization's GitLab).
2. Steal Login Info: Users login as normal and get redirected to a fake site that asks for credentials again.
Double-Check Links: Before clicking, hover and see where a link actually leads.
- Educate Your Team: Let them know about this risk and teach best practices for clicking links in emails and chats.
Summary Table
| GitLab Version Range | Affected by CVE-2023-1279? |
|--------------------------|:--------------------------------:|
| 4.1 - 16.1.4 | Yes |
| 16.2 - 16.2.4 | Yes |
| 16.3 - 16.3. | Yes |
| 16.1.5, 16.2.5, 16.3.1+ | Not Vulnerable |
Closing Thoughts
CVE-2023-1279 is a classic example of why strict input validation matters in web development. If you run GitLab, update ASAP to avoid giving attackers an easy way into your workflows.
For full technical details and fixes, see the official GitLab advisory.
Stay aware, stay patched, and keep an eye on your URLs!
Further Reading
- GitLab Security Releases
- OWASP: Open Redirect
- NVD - CVE-2023-1279
Have questions about GitLab vulnerabilities? Drop them below, and let’s keep our software safe together!
Timeline
Published on: 09/01/2023 11:15:00 UTC
Last modified on: 09/07/2023 17:15:00 UTC