Google Chrome is one of the top web browsers worldwide, and millions of people use it daily. Security is a significant concern for developers and users alike. This long-read article will discuss the CVE-2023-1530 use-after-free vulnerability in Google Chrome versions before 111..5563.110. We will dive into the cause, some code snippets, original references, and exploitation details, with the intent to inform and educate security researchers, developers, and users about the dangers of this security flaw.
Vulnerability Details
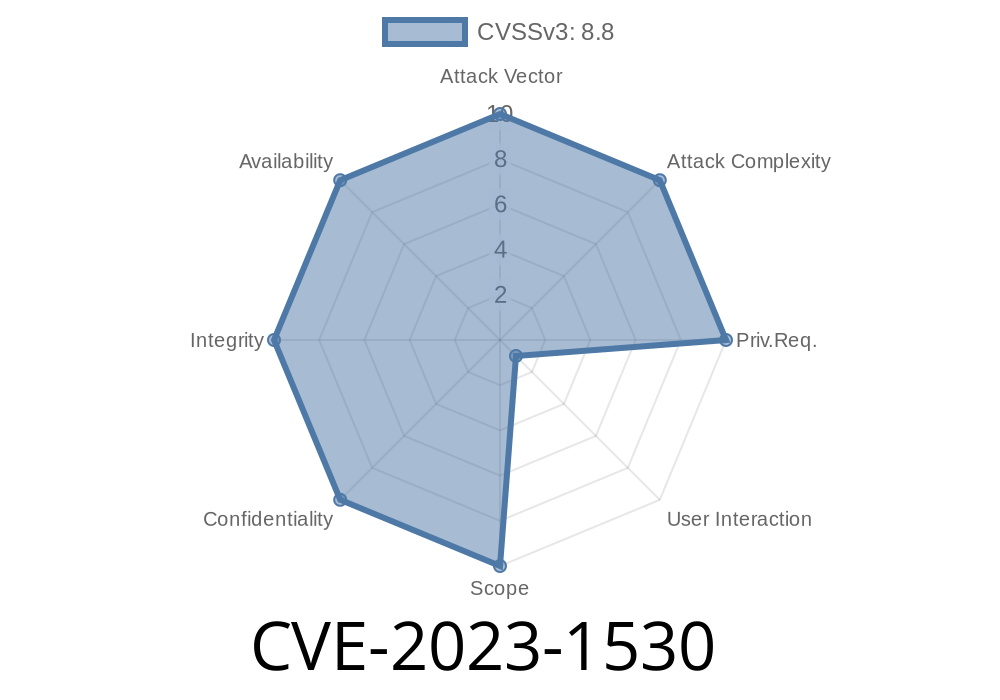
CVE-2023-1530 is a use-after-free vulnerability in the PDF rendering engine in Google Chrome prior to version 111..5563.110. This flaw could potentially let remote attackers exploit heap corruption through a specially crafted HTML page, allowing them to execute arbitrary code in the user's computer. This vulnerability has a severity rating of "High," according to the Chromium Project Security Team.
Technical Explanation
A use-after-free vulnerability occurs when the program continues to use a memory resource after it has been freed or deleted. As a result, a malicious actor might exploit this vulnerability by running arbitrary code or triggering the execution of unintended memory segments.
In Google Chrome, the PDF viewer component (PDFium) converts PDF files into HTML contents. A bug within the code causes the vulnerability, leading to a use-after-free situation. To exploit this, the attacker can create a crafted PDF file containing JavaScript that manipulates the memory layout and controls the released object.
The following code snippet illustrates this exploit
// Create an ArrayBuffer with a malicious payload
var shellcode = new Uint8Array([...]);
// Create the PDF file with JavaScript running the exploit
var crafted_pdf = ...%PDF-...;
// Create an iframe with the crafted PDF file
var iframe = document.createElement('iframe');
iframe.src = URL.createObjectURL(new Blob([crafted_pdf], {type: 'application/pdf'}));
document.body.appendChild(iframe);
In this code snippet, the attacker creates a malicious ArrayBuffer with shellcode that they want to execute. Subsequently, they create a crafted PDF with embedded JavaScript that triggers the vulnerability when the victim opens the PDF in Chrome. Finally, the attacker embeds the PDF into an HTML page with a hidden iframe, seamlessly executing the exploit when the victim visits the crafted HTML page.
References
- Original Chromium Bug Report: https://bugs.chromium.org/p/chromium/issues/detail?id=1249617
- National Vulnerability Database (NVD) Entry: https://nvd.nist.gov/vuln/detail/CVE-2023-1530
- Chrome Releases - Stable Channel Update: https://chromereleases.googleblog.com/2023/03/stable-channel-update-for-chrome_45.html
Mitigation
To prevent exploitation of this vulnerability, users should update their Google Chrome browser to version 111..5563.110 or later. Updating your browser mitigates risks and ensures that you utilize the most recent security patches and improvements.
Conclusion
The CVE-2023-1530 use-after-free vulnerability in Google Chrome is a severe security issue that could be exploited by malicious actors for compromising the affected systems. By understanding the technical details, researching original references, and taking necessary steps to update Chrome to a safe version, you can better protect yourself and your organization.
It is a reminder for all developers and users to stay vigilant, ensuring that they adopt best practices, such as promptly applying necessary patches, updating software to the latest versions, and implementing comprehensive security measures to minimize potential threats.
Timeline
Published on: 03/21/2023 21:15:00 UTC
Last modified on: 04/15/2023 04:16:00 UTC