---
Introduction
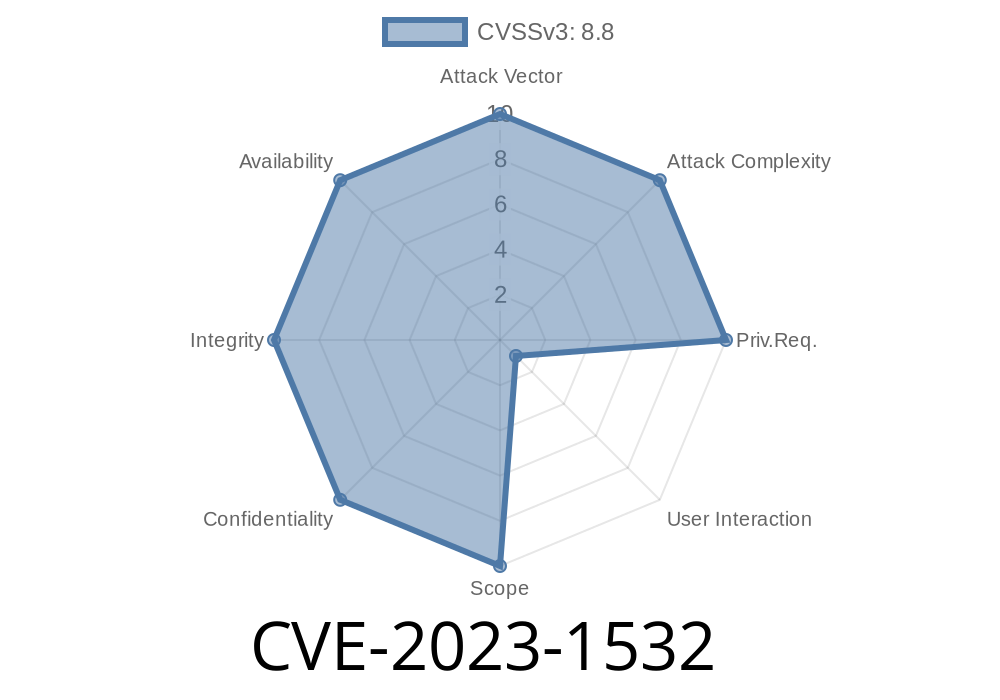
CVE-2023-1532 is a high-severity vulnerability discovered in Google Chrome's GPU video to processing pipeline. This bug, present before version 111..5563.110, could let remote attackers exploit heap corruption just by having you visit a specially crafted web page. Let's break it down simply: attackers could take over your machine or run unwanted code using this Chrome flaw, thanks to how it incorrectly handles video in the GPU.
In this long read, we'll explain how this bug happened, show example proof-of-concept code, detail a possible exploitation path, and provide clear advice on how to protect yourself. We’ll also link to original sources and official patches.
What Is an Out-Of-Bounds Read?
An out-of-bounds read happens when a program tries to read memory outside the area it's supposed to. In Chrome’s case, the bug occurs in the GPU video code — a powerful and complex part of the browser that decodes and plays video content using your graphics processor.
If an attacker can control what video data gets decoded, they might craft a malicious HTML page with bad video data. This tricks Chrome into reading past the end of what's allowed, potentially leaking or corrupting memory.
Versions: Before 111..5563.110
- CVE ID: CVE-2023-1532
Original bug tracker
According to Google’s official release notes
> "Out of bounds read in GPU Video in Google Chrome prior to 111..5563.110 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page."
— Chrome Releases Blog
How Could Someone Exploit It?
To exploit this bug, an attacker creates a malicious webpage containing special video data. When a victim visits the page with a vulnerable version of Chrome, the browser's GPU video decoder tries to process the video. Due to faulty bounds checking, Chrome reads unintended memory, possibly causing a heap corruption or leaking sensitive data.
In some cases, this could even allow an attacker to execute their own code — for example, to drop malware or hijack your browser session.
Proof-of-Concept (PoC) Example
Below is a simplified example (for educational purposes only!) that outlines *how* an attacker might target this vulnerability.
*Note: Do not use this code maliciously. This is for learning and testing in safe environments only.*
<!DOCTYPE html>
<html>
<body>
<h2>CVE-2023-1532 PoC – Triggering Out-of-Bounds in Chrome's GPU Video Decoder</h2>
<video id="video" width="320" height="240" controls></video>
<script>
// This ArrayBuffer simulates a specially crafted video
// In a real scenario, the binary data would exploit parsing quirks
const fakeVideoData = new Uint8Array([
// Invalid/edge-case video header bytes go here
x00, x00, x01, xB6, xFF, x00, x00, /* etc... */
]);
// Create a Blob and a URL for the <video> tag
const blob = new Blob([fakeVideoData], {type: "video/mp4"});
const url = URL.createObjectURL(blob);
// Assign the crafted video to the player
document.getElementById('video').src = url;
document.getElementById('video').play();
// This causes Chrome to decode the crafted data
</script>
</body>
</html>
Why does this work?
If the specially crafted bytes lead Chrome’s GPU code to miscalculate buffer sizes, it could read outside the allowed memory region. In old, unpatched Chrome versions, this could corrupt the heap or expose sensitive data.
Fix: Chrome patched it in version 111..5563.110 (March 2023).
- Credit: As per Chromium's notes, the issue was tracked as issue 1388107 and fixed internally.
Security Impact
Because the bug involves heap corruption, it’s risky: advanced attackers could combine this with other flaws to run arbitrary code. Even if code execution isn’t achieved, reading out-of-bounds could leak information or crash the browser.
Am I Still Vulnerable?
If you’re using Chrome prior to 111..5563.110 — yes, you’re at risk. Given Chrome auto-updates, most users are likely safe. But always check your version or download the latest:
Download Google Chrome
References
- NVD - CVE-2023-1532
- Chrome Stable Channel Update
- Chromium Security Whitepaper
Conclusion
CVE-2023-1532 is another reminder that even modern browsers like Chrome can contain critical bugs that open doors for attackers. A single out-of-bounds read in the GPU video pipeline could have major security consequences — so always keep your browser up to date, and remember: just visiting a cleverly crafted site can be enough for an attack.
Timeline
Published on: 03/21/2023 21:15:00 UTC
Last modified on: 04/12/2023 04:15:00 UTC