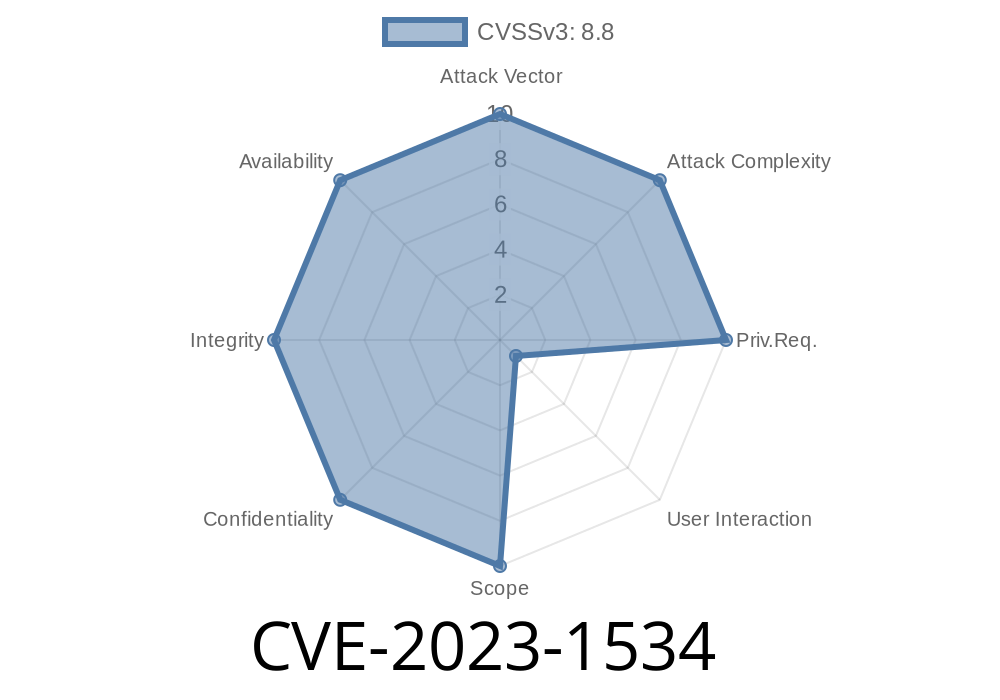
In March 2023, a critical security vulnerability, CVE-2023-1534, was discovered in Google Chrome’s ANGLE graphics library. The flaw allows a remote attacker—who already has control over Chrome's renderer process—to read out-of-bounds memory, with potential for heap corruption. If you’re responsible for browser security or simply want to understand how such bugs can be exploited, this post explains what went wrong, how attackers could use this bug, and how you can protect yourself.
What is ANGLE?
ANGLE (Almost Native Graphics Layer Engine) is a cross-platform graphics engine used by browsers like Chrome to translate WebGL calls to platform-specific graphics APIs. It’s a critical piece of Chrome's rendering engine for rich media and games on the web.
CVE-2023-1534
> Out of bounds read in ANGLE in Google Chrome prior to 111..5563.110 allowed a remote attacker who had compromised the renderer process to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High)
Severity: HIGH
Links to official sources:
- Chromium Security Advisory
- NVD - CVE-2023-1534
How the Attack Works
1. Compromised Renderer: The attacker needs to first exploit another renderer process bug (like a JavaScript engine bug) to run code in Chrome's rendering process.
2. Crafted HTML Page: They serve a webpage with malicious WebGL or graphics code targeting this bug.
3. Out-of-Bounds Read: By manipulating WebGL commands, the code can trick ANGLE into reading memory outside the expected buffer.
4. Heap Corruption: This could lead to heap corruption, which is often a stepping stone towards arbitrary code execution or information disclosure.
Example Code Snippet
While the exact vulnerable code was deep within ANGLE and not exposed directly to web developers, you can imagine the attacker would use JS like this:
<!-- Example of malicious WebGL code -->
<canvas id="c"></canvas>
<script>
const gl = document.getElementById('c').getContext('webgl');
if (gl) {
// Create and set up a shader in a way that triggers the OOB read
const vsSource = 'attribute vec4 position; void main() { gl_Position = position; }';
const fsSource = 'void main() { gl_FragColor = vec4(1.); }';
const vs = gl.createShader(gl.VERTEX_SHADER);
gl.shaderSource(vs, vsSource);
gl.compileShader(vs);
const fs = gl.createShader(gl.FRAGMENT_SHADER);
gl.shaderSource(fs, fsSource);
gl.compileShader(fs);
const prog = gl.createProgram();
gl.attachShader(prog, vs);
gl.attachShader(prog, fs);
gl.linkProgram(prog);
gl.useProgram(prog);
// Here, the attacker would carefully craft buffer data and draw calls.
// The OOB read would be triggered by specific parameters.
}
</script>
*Note: The actual attack would be more complex, but this shows roughly how such an engagement begins.*
Exploit Details
The root cause was an improper bounds check inside ANGLE. When handling certain WebGL operations, ANGLE failed to validate buffer boundaries before accessing data. This allowed reads from memory that did not belong to the intended allocation, leading to potential heap corruption.
Information leak (attacker could read other data in Chrome's memory)
- Heap corruption (used in chaining with other bugs for full code execution outside of the sandbox)
Exploitability:
The main limitation is that the attacker must already control the renderer process. That said, chaining browser renderer bugs is a common pattern in targeted attacks.
How was it fixed?
The Chrome team patched this issue by adding stricter checks to prevent reading beyond buffer boundaries.
Patch reference:
- Chromium Commit
- Release Notes
If you haven’t already
- Update Chrome: Always use the latest Chrome version. Chrome 111..5563.110 and later are NOT vulnerable.
Summary
The CVE-2023-1534 vulnerability in ANGLE highlights the importance of graphics security in modern browsers. Even less-obvious areas like WebGL can be fertile ground for attacks, especially when combined with other bugs.
Stay safe online, and keep your browser updated!
References:
- Chromium blog: March 29, 2023 Stable Channel Update
- NVD entry for CVE-2023-1534
- Chromium Commit fixing OOB read in ANGLE
Timeline
Published on: 03/21/2023 21:15:00 UTC
Last modified on: 04/21/2023 20:15:00 UTC