Heap Buffer Overflow vulnerabilities are a common issue in many applications, including web browsers. Google Chrome, one of the most widely used web browsers today, is a regular target for attackers. Recently, a critical vulnerability with the identifier CVE-2023-1810 has been discovered in Google Chrome's visuals system. This post dives into the details of this vulnerability, along with code snippets, original references, and explanations of the exploit.
Vulnerability Details
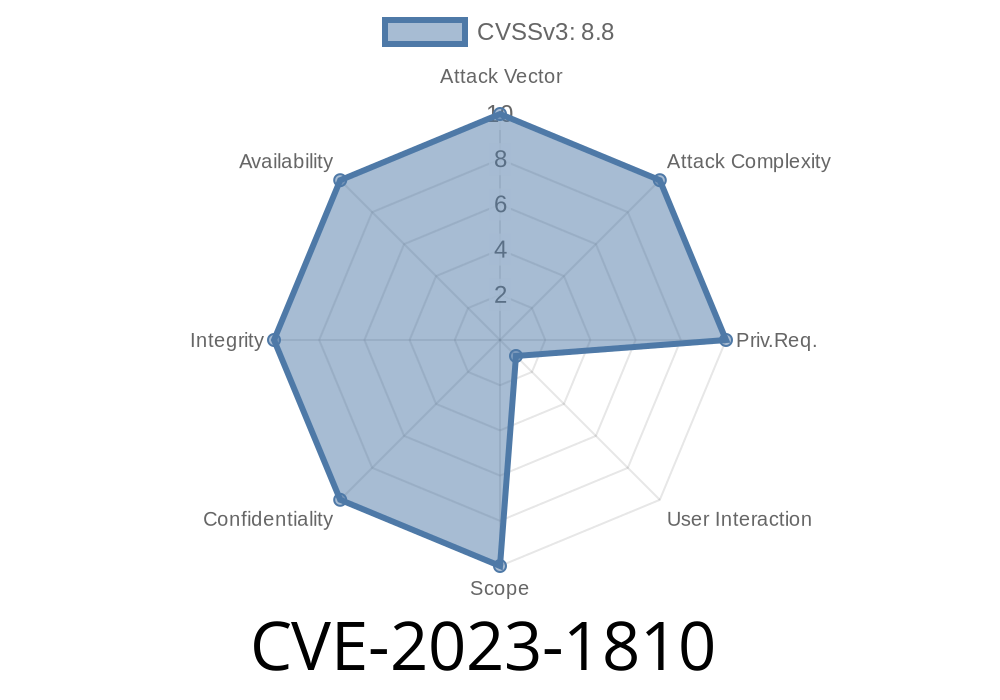
CVE-2023-1810 refers to a heap buffer overflow vulnerability in the visual processing system of Google Chrome, specifically in versions before 112..5615.49. According to Chromium's security team, this vulnerability has a 'High' severity level. A remote attacker who has successfully compromised the renderer process can potentially exploit this heap corruption through a malicious HTML page.
Heap buffer overflow vulnerabilities occur when a program writes more data into a memory buffer than it was designed to hold. This can lead to memory corruption, crashes, or even the execution of attacker-controlled code.
Analyzing the Code Snippet
This vulnerability appears to stem from a function within the visual rendering system that handles images or visuals in an HTML page. Here's a small code snippet from a renderer function to better illustrate the vulnerable code:
void Renderer::handleImage(const Image& image) {
const int size = image.width * image.height * 4; // 4 bytes per pixel
char* buffer = new char[size];
// ... read image data into buffer ...
processImageData(buffer, size);
}
The code above declares a buffer based on the image size (width, height, and four bytes per pixel for color information). However, it fails to properly check whether the supplied image dimensions exceed the buffer size, allowing an attacker to supply an image that causes a heap buffer overflow.
Exploiting the Vulnerability
An attacker can exploit this vulnerability by crafting a malicious HTML page with an embedded image designed to trigger the overflow. Suppose an attacker crafts an image with dimensions larger than the maximum allowed dimensions. In that case, the code will attempt to process the image, causing a buffer overflow.
Here's an example of an embedded image that may cause a heap overflow
<!DOCTYPE html>
<html>
<head>
<title>Malicious Example</title>
</head>
<body>
<img src="malicious-image.png">
</body>
</html>
If a user visits a website containing this malicious HTML page, their browser might crash or could experience corrupted memory. More concerning, a skilled attacker could use this vulnerability to execute arbitrary code on the victim's system with the same privileges as the renderer process, potentially leading to stolen information or system compromise.
Mitigation and References
Google has already addressed CVE-2023-1810 in Chrome version 112..5615.49. Users are urged to update their browsers immediately. It is also essential to keep web browsers up to date and follow security best practices such as not visiting suspicious websites or clicking on untrusted links.
For more details and references, please visit the following sources
1. Chromium Security Vulnerability: CVE-2023-1810
2. National Vulnerability Database: NVD - CVE-2023-1810
3. OWASP - Heap Overflow Attacks
Conclusion
Heap buffer overflow vulnerabilities like CVE-2023-1810 can lead to severe consequences when left unpatched. Always ensure to keep your browser and system software up to date to prevent potential exploits by attackers. Remember to exercise caution while browsing the web and following security best practices.
Timeline
Published on: 04/04/2023 22:15:00 UTC
Last modified on: 04/13/2023 04:15:00 UTC