Honeywell's MPA2 Access Panel is a popular product for managing access control in buildings and secure environments. However, in early 2023, cybersecurity researchers uncovered a critical vulnerability known as CVE-2023-1841. This flaw allows an attacker to perform Cross-site Scripting (XSS) attacks by injecting malicious scripts using unusual or invalid characters.
In this article, we break down how this vulnerability works, share example exploits, and show you how to defend against it.
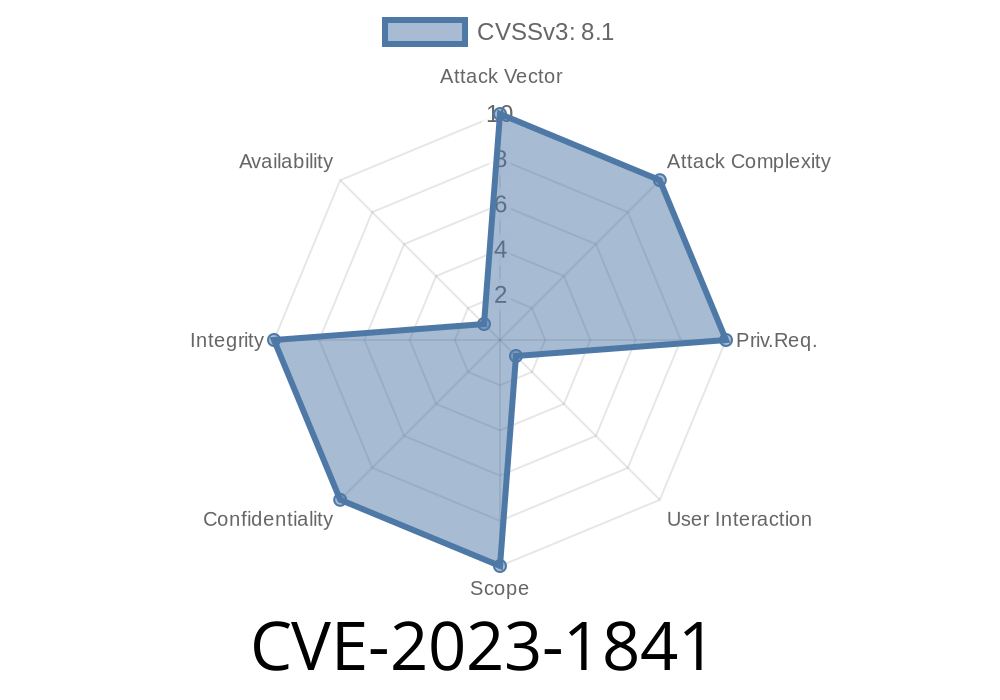
What Is CVE-2023-1841?
CVE-2023-1841 is classified as an Improper Neutralization of Input During Web Page Generation (Cross-site Scripting) vulnerability. It affects all versions of the Honeywell MPA2 Access Panel Web server modules released before version R1.00.08.05.
By exploiting this, an attacker can inject JavaScript code through webpage inputs, potentially stealing user session information or performing unauthorized actions in the web application.
Official advisory:
- Honeywell VU#583089 – MPA2 Access Panel Multiple Vulnerabilities
Who’s at Risk?
Anyone running the MPA2 Access Panel software prior to version R1.00.08.05. This includes factories, offices, data centers, and buildings where MPA2 controls secure door entry. Exploitation is possible if:
How Does This XSS Vulnerability Work?
The main issue: The device’s web server does not correctly filter (sanitize) certain special or “invalid” characters. This allows attackers to sneak in <script>, <img onerror>, or other HTML/JavaScript tags into data fields like usernames, badge IDs, or other web forms.
What makes this unique?
Attackers can use characters not typically allowed in normal input. For example, Unicode, null bytes, or overlong encodings, which bypass weak input validation.
Example Exploit
Suppose the web app has a user registration field that should only accept letters and numbers. However, it does not properly neutralize input like:
<script>alert('XSS!')</script>
A real attacker might sneak in something more subtle, such as
<img src="x" onerror="alert('Gotcha!')" />
Or, using an encoded payload (to bypass faulty validation)
%3Cscript%3Ealert('pwned')%3C/script%3E
If you enter this into a field such as "Badge Name" and then view the web page that lists all badges, the malicious code could run in your browser – displaying an alert, or worse, stealing your session cookie or performing admin actions.
Let’s say there is a web form for adding a new employee badge
<form action="/add_badge" method="POST">
<input type="text" name="badge_name">
<input type="submit" value="Add Badge">
</form>
And in the vulnerable backend, the server does not sanitize input
# Simplified Python-like Pseudocode
def add_badge(request):
badge_name = request.POST['badge_name']
db.save_badge(badge_name) # NO sanitation!
return render_template("badges.html")
When the badges are listed, your injected