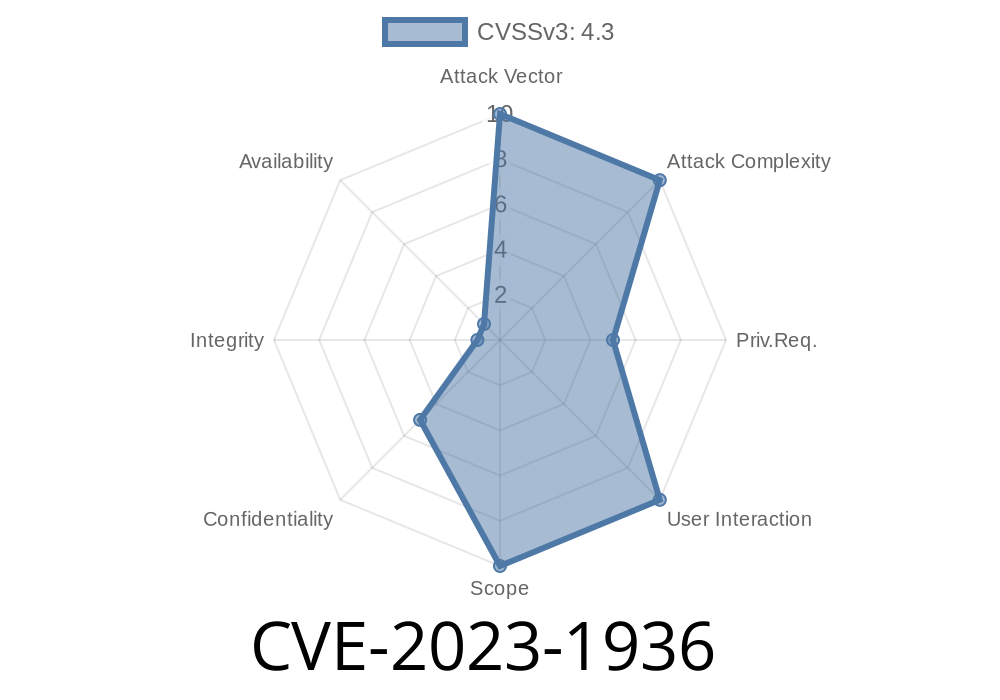
If you're running a DevOps workflow using GitLab, CVE-2023-1936 should be on your radar. This vulnerability lets attackers grab the email addresses of users who opened Service Desk issues—something most would expect to be private. In this post, I'll break down what happened, show you exactly how it worked, and arm you with practical information drawn from real-world references.
What is GitLab Service Desk?
Service Desk in GitLab lets users and external folks open issues (tickets) just by sending an email to a special project address. It's widely used for support, reporting bugs, or getting help—often by people outside your core development team.
What’s CVE-2023-1936?
CVE-2023-1936 is a vulnerability discovered in GitLab Community Edition (CE) and Enterprise Edition (EE). If you use Service Desk, a flaw in the way these issues were displayed made it possible for an attacker to harvest the original sender's email.
References
- GitLab Advisory
- NIST NVD Entry
How Did The Vulnerability Happen?
Normally, when someone emails your Service Desk, the issue that gets opened *should* hide their real email. But due to a logic error, that information was leaking. Here’s why:
When users emailed support (Service Desk), their addresses were saved in the raw issue metadata.
- This data appeared hidden in the UI, but could easily leak through the GitLab API or by scraping the web page source.
Practical Exploit Example
Let’s say an attacker wants to check for exposed user emails linked to Service Desk issues.
Step 1: Finding a Project With Service Desk Enabled
First, the attacker browses GitLab instance projects and locates projects with Service Desk on.
Step 2: Locate Service Desk Issues
Service Desk issues are usually tagged or clearly named (sometimes with internal IDs).
Through The GitLab API
If the project is public (or the attacker has access), they can check the issue data directly.
curl -s "https://gitlab.example.com/api/v4/projects/123/issues/456"; | jq
Look for fields like "author_email" or similar in the JSON output. Before the patch, this sometimes included the original sender’s email.
- Pre-patch, you might spot something like
<!--
Service Desk original sender: john.doe@example.com
-->
General loss of trust in your Service Desk process.
For companies handling customer support, this could even mean regulatory headaches (think GDPR).
How GitLab Fixed It
GitLab’s patch scrubs out the user emails from all issue metadata that’s accessible to non-admins (and in many cases, everyone). If you’re running a vulnerable version, upgrade to:
Check your version:
Go to your GitLab instance and check your version. If you’re in the affected range, plan for an update.
Upgrade:
Follow the official upgrade guide.
Audit your API access:
Disable public API access for sensitive projects, or limit guest access, as a baseline best practice.
Extra Reading and References
- GitLab Official Advisory (July 2023)
- National Vulnerability Database Entry
- GitLab Service Desk Docs
- General Guide on CVEs
Final Thoughts
Every time you open an issue, whether privately or through Service Desk, you trust tools to keep your personal information safe. CVE-2023-1936 shows how easy it is for simple bugs to put that trust at risk. Don’t ignore those update notifications—set aside time to patch your systems before someone else does it for you.
Stay safe, DevOps world!
*Want more security deep-dives like this? Let us know what topics you’re interested in!*
Timeline
Published on: 07/11/2023 08:15:00 UTC
Last modified on: 07/19/2023 14:26:00 UTC