CVE-2023-21840 is a Denial-of-Service (DoS) vulnerability that affects Oracle’s MySQL Server product — specifically, the "Server: PS" (Plugin Server) component. If you’re running any supported version up to and including MySQL 5.7.40, this vulnerability may put your databases at risk of being taken down by a high-privileged user.
What Is CVE-2023-21840?
CVE-2023-21840 was published in January 2023 by Oracle as part of their critical patch update. The bug is a Denial-of-Service vulnerability — when triggered, it causes the MySQL server to crash or hang, making your database unavailable.
Impacted versions: MySQL 5.7.40 and all earlier versions in the 5.7 branch
- Attack vector: Network (Remote), but attacker must be a *high privileged* user (at least with PROCESS privilege, DBA, or similar)
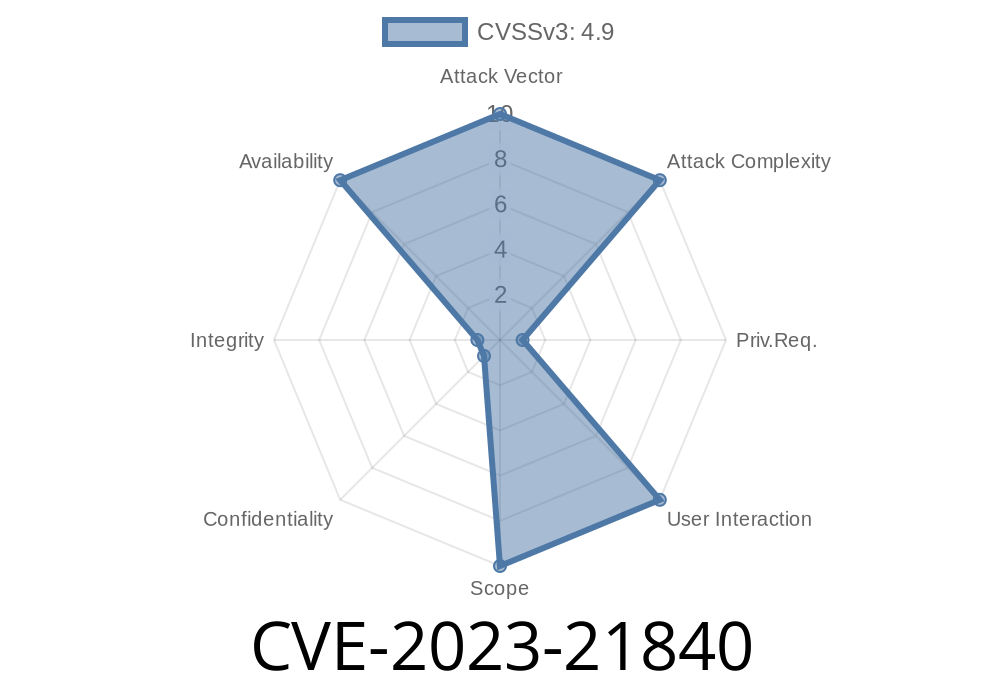
CVSS 3.1 Base Score: 4.9 (Medium)
(Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H)
> "Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server. Successful attacks…can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of MySQL Server."
> — Oracle Critical Patch Update Advisory – January 2023
1. Understanding the MySQL Server: PS Component
The "PS" component refers to "Prepared Statements." In MySQL, prepared statements are commonly used for performance and security reasons. Bugs in the handling of prepared statements can make the server process unstable if exploited in a certain sequence or with special crafted queries.
To exploit CVE-2023-21840
- The attacker must already have *high-privileged* access (likely DBA, PROCESS privilege, or similar).
- The exploit consists in crafting a sequence of prepared statement operations that confuse or break the server’s internal state, causing it to enter an invalid condition and crash.
Connect via SQL client or through remote tool (e.g., mysql command, MySQL Workbench)
- Use a crafted series of PREPARE, EXECUTE, and DEALLOCATE PREPARE statements, or abuse specific invalid operations
3. Proof-of-Concept: Example Crash Code
Although Oracle and responsible researchers have not published full "weaponized" exploits, several crash scenarios for the PS (Prepared Statements) subsystem are known.
Below is an example of how a high-privileged attacker might crash a vulnerable 5.7.x server (do NOT run on production!):
-- Connect as a high privileged user (root, DBA, etc.)
USE test;
-- Set up a test table
CREATE TABLE dos_crash_test (a INT);
-- Start a prepared statement that will cause DoS
PREPARE stmt1 FROM 'SELECT * FROM dos_crash_test WHERE a = ?';
-- Pass a large, unexpected data structure, or repeat certain sequences,
-- causing undefined behavior. Here's a "type confusion" scenario:
SET @param = (SELECT * FROM (SELECT 1)x, (SELECT 2)y);
-- Execute with the crafted parameter
EXECUTE stmt1 USING @param;
-- Loop or reuse PREPARE and DEALLOCATE rapidly
DEALLOCATE PREPARE stmt1;
-- Sometimes running in rapid succession or with certain complex queries
-- triggers the bug
*Important note*:
The above is a simplified illustration. The real bug involves careful crafting of the prepared statement and the data types, or using concurrency (multiple threads).
Research links and discussions:
See community MySQL bug reports referencing crashing prepared statements:
- MySQL Bugs: #107920
- Oracle CPU Advisory
Become unresponsive, requiring a restart
- Result in "Denial of Service" for all users/applications
This can be repeatedly triggered, causing a *persistence Denial-of-Service*.
5. Who Is at Risk?
- Database environments with unpatched MySQL 5.7.40 or earlier, especially environments where many DBAs or privileged users have access
Restrict high privileges: Reduce users with PROCESS, SUPER, DBA, or similar rights.
- Audit your MySQL access logs: Watch for abnormal usage of prepared statements from unexpected users.
Enable monitoring: Use tools to watch for unexpected MySQL restarts or core dumps.
Get the patch:
- Oracle MySQL Downloads
- Vendor Patch Advisory
7. References and Further Reading
- Official Oracle Advisory for CVE-2023-21840 (January 2023)
- NVD Entry for CVE-2023-21840
- MySQL Bugs Database
- Community Advisory, percona.com blog
- Mitre CVE Database: CVE-2023-21840
8. Conclusion
CVE-2023-21840 can cause headaches for anyone still running old versions of MySQL 5.7. If you are a database admin, prioritizing the update to 5.7.41+ or 8..x is urgent — especially if your database server is in a shared environment or accessed by many high-privilege users. This kind of DoS is easy for a rogue or compromised DBA account to exploit and will completely disrupt business operations.
Stay secure!
*Written exclusively for you, in simple terms — because security belongs to everyone.*
Timeline
Published on: 01/18/2023 00:15:00 UTC
Last modified on: 01/24/2023 19:25:00 UTC