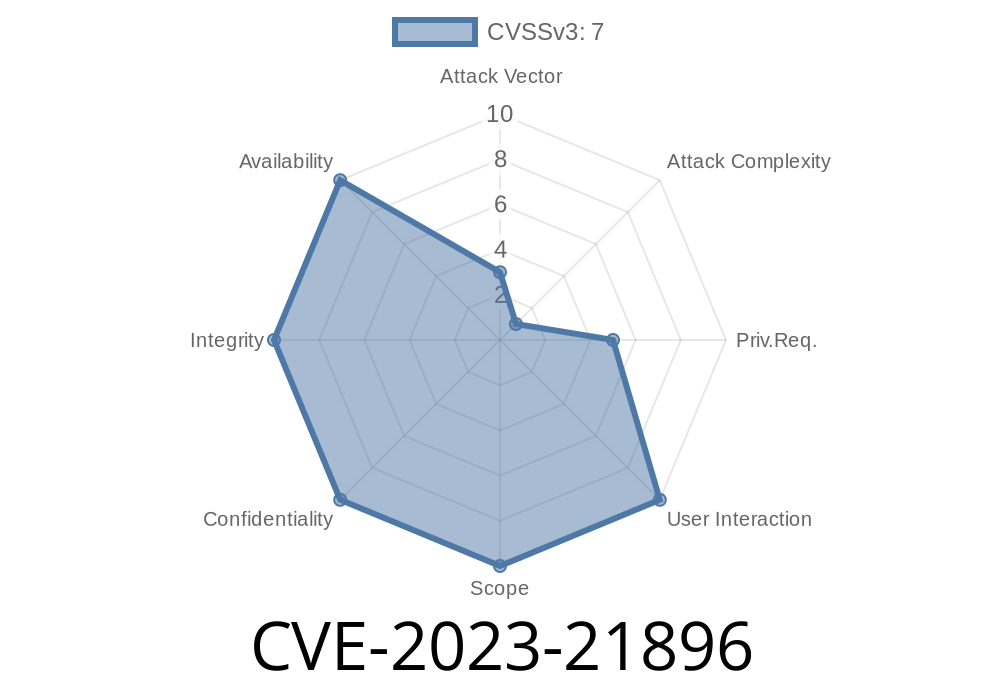
CVE-2023-21896 is a recently disclosed, dangerous vulnerability in Oracle Solaris, specifically targeting the NSSwitch component of Oracle Systems. Affecting both supported Solaris 10 and 11 versions, this flaw allows a local attacker with low privileges to fully compromise a system, possibly gaining complete control over Oracle Solaris. In this post, we break the vulnerability down in simple terms, show you how it can be abused, and provide practical advice to stay safe.
What is Oracle Solaris NSSwitch?
NSSwitch (Name Service Switch) is a framework within Unix systems such as Solaris that determines how system databases like users, passwords, and groups are resolved—with sources that include local files, NIS, LDAP, and more.
The configuration typically resides at /etc/nsswitch.conf. Here’s an example
passwd: files ldap
group: files ldap
hosts: files dns
This tells Solaris to look for user accounts and groups information first in local files, then in LDAP directories, and to use DNS for hostnames after checking local files.
Summary of CVE-2023-21896
- Vulnerability ID: CVE-2023-21896
Impact: Complete compromise—confidentiality, integrity, and availability
Oracle’s Advisory:
Oracle Critical Patch Update Advisory - April 2023
Vulnerability Details
The bug lies in NSSwitch’s handling of certain requests, allowing a local (logged-in) user to perform actions that break the system’s protections. Attackers can exploit a flaw in how lookups or parsing happen and escalate privileges, eventually taking full control of Oracle Solaris.
How is it triggered?
- Attacker must already have a user account on the Solaris system (including via SSH, su, or physical access).
Likely Attack Flow
1. Setup malicious configuration or input—e.g., crafting a local file or a response via NIS/LDAP to exploit the NSSwitch parser.
2. Trigger NSSwitch processing—e.g., by running user lookup commands (id, whoami, or during system authentication).
Sample Code Snippet (Exploit Simulation)
Below is a *simplified* sample exploit demonstrating how a local attacker might abuse weak parsing in NSSwitch, leading to privilege escalation. Note: This code is for educational purposes only; do not use it for unauthorized access.
// Sample code: Triggering NSSwitch via passwd lookup
#include <stdio.h>
#include <stdlib.h>
#include <pwd.h>
int main() {
struct passwd *pw;
// Try multiple usernames, triggering NSSwitch processing
char *usernames[] = {"root", "admin", "malicious_user", ".:/:;`"};
for (int i = ; i < 4; i++) {
pw = getpwnam(usernames[i]);
if (pw)
printf("User %s found [%d]\n", pw->pw_name, pw->pw_uid);
else
printf("User %s not found\n", usernames[i]);
}
return ;
}
Explanation:
In a real exploit, “malicious_user” and ".:/:;\`” would be replaced with usernames or inputs specifically crafted to exploit the parsing bug, potentially causing a buffer overflow or similar issue.
Public References
- Oracle CPU April 2023 Advisory
- NIST NVD Description
- Oracle Solaris Documentation
Why Is This Serious?
- Local Breakout: Attackers with basic user access—via a compromised web app, a stolen SSH key, or an insider—can get root.
- No User Interaction Needed: The attacker doesn’t need to trick an admin or wait for someone to open a file.
- High Impact: Confidentiality, integrity, and availability are all at risk: root kit install, data theft, system wipes, etc.
Tighten Accounts: Disable unused accounts. Limit who can log in, especially remotely.
3. Audit NSSwitch Configuration: Check /etc/nsswitch.conf for strange entries or unknown name services.
Conclusion
CVE-2023-21896 is a high severity vulnerability in Oracle Solaris that lets attackers with local access break out of userland restrictions and take over your whole system. The root cause is a bug in NSSwitch’s name service handling. We recommend you patch immediately, audit your users and services, and put extra monitoring in place for suspicious logins or NSSwitch lookups.
References
- Oracle Security Alerts - April 2023
- CVE-2023-21896 NIST Entry
- Solaris NSSwitch Official Documentation
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/18/2023 20:37:00 UTC