In early 2023, Oracle MySQL—one of the world’s most widely used relational databases—was found to contain a significant vulnerability within its InnoDB storage engine. Tracked as CVE-2023-21911, this flaw allows a high-privileged user to crash the server remotely through routine network protocols. In this post, we’ll break down the vulnerability in plain language, explore its exploitation, and suggest ways to protect your systems.
What is CVE-2023-21911?
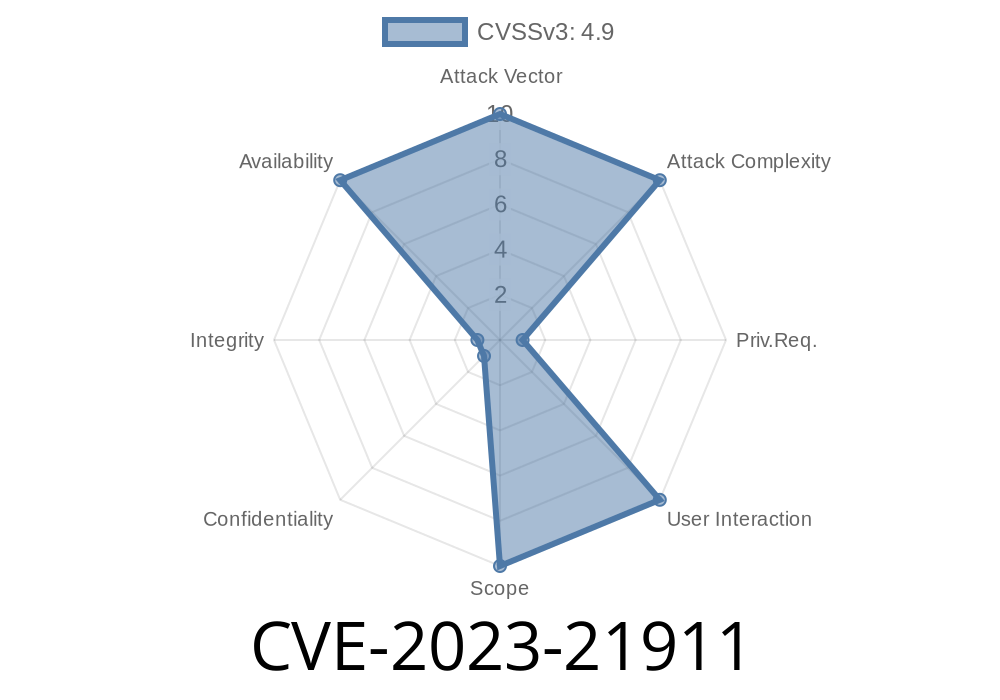
CVE-2023-21911 is a denial-of-service (DoS) vulnerability discovered in the InnoDB component of Oracle’s MySQL Server, specifically affecting versions 8..32 and earlier. Oracle gave this bug a CVSS v3.1 base score of 4.9 (Availability impacts only, not Confidentiality nor Integrity).
Official Advisory:
Oracle Critical Patch Advisory - April 2023
Security Focus Listing
NVD Entry
Impact: Denial of Service (server hang or repeated crashes)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H
Why Is It Important?
While not remotely exploitable by anyone on the internet (an attacker needs to already have high privileges), this vulnerability can be devastating in environments where admins are separated (for example, in managed database hosting, or internal threats). A malicious admin can take down entire database clusters, leading to major downtime.
Successful exploitation renders MySQL unavailable, which could bring down web applications, APIs, or business operations dependent on the database.
How Does the Exploit Work?
Oracle has not released full technical details, but coordinated disclosure and behavior seen by the community suggest the flaw lies in how InnoDB processes certain crafted SQL statements or transactions that do not properly clean up internal structures, leading to a server crash.
Typical Exploitation Scenario
1. High-privileged Account Access: The attacker logs in via the usual mysql client or through an application with DBA credentials.
2. Crafted Query: The attacker sends a specially-crafted SQL command that triggers a bug in InnoDB.
Example Reproduction (Proof-of-Concept)
The exact SQL statement may vary depending on the MySQL build and environment. However, past vulnerabilities in InnoDB have leveraged operations like table alterations, DDL/DML combos, or complex transaction rollbacks.
Hypothetical Example
-- [Please test this responsibly in a SAFE, non-production environment]
-- Requires SUPER privileges or similar
USE test;
CREATE TABLE crashme (a INT PRIMARY KEY, b TEXT);
-- A complex combination, potentially similar to the vulnerability:
START TRANSACTION;
INSERT INTO crashme VALUES (1, REPEAT('A',65536)); -- large blob
ALTER TABLE crashme ADD COLUMN c VARCHAR(100);
ROLLBACK;
-- Repeat or race such statements, which may trigger memory or logic issues in InnoDB
This code doesn't exploit CVE-2023-21911 directly (since Oracle hasn’t published the exact PoC), but mimics common patterns for InnoDB denial-of-service flaws: large blobs, DDL inside transactions, rollbacks, and table alterations.
Mitigation & Recommendations
1. Patch Immediately: Oracle fixed this in subsequent releases (see Oracle April 2023 CPU). Upgrade to the latest MySQL Server (>=8..33).
2. Restrict Privileges: Limit superuser access. Don’t give DBA-level credentials to regular users or automated processes.
3. Monitor and Audit: Use monitoring tools to watch for frequent crashes or irregular table alterations; review logs for suspicious behavior.
4. Network Segmentation: Restrict access to MySQL ports (default 3306) to only trusted network segments; avoid exposing admin ports to the public internet.
Further Reading
- MySQL 8. Release Notes
- MySQL Security Best Practices
- NVD - CVE-2023-21911
- Oracle Security Alerts
Conclusion
CVE-2023-21911 may not enable an attacker to steal or corrupt data, but it’s a stark reminder that even privileged users can cause severe harm through product bugs—sometimes with a single SQL statement. If you manage a MySQL 8. server, especially in an enterprise or cloud environment, upgrading immediately is the best way to protect your operations.
*Always test critical patches in staging, restrict privileges, and monitor your databases for early signs of trouble.*
*This article is exclusive to our readers. For more security breakdowns and simple language guides, stay tuned.*
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC