---
Introduction
On January 17, 2023, Oracle published Critical Patch Update (CPU) advisories for their products, including details on CVE-2023-21913, a notable Denial-of-Service (DoS) vulnerability in the Server: Optimizer component of MySQL Server. This issue affects all supported MySQL versions up to 8..31 and is relatively easy for high-privileged attackers to exploit. While the vulnerability doesn’t allow data theft or manipulation, it can lead to repeated server crashes, causing serious availability issues for production databases.
Let’s break down how CVE-2023-21913 works, look at a sample PoC, and see how you can protect your infrastructure.
What is CVE-2023-21913?
CVE-2023-21913 is a vulnerability in MySQL’s Server Optimizer. The optimizer’s job is to plan how to execute SQL queries efficiently. In certain cases, it mishandles crafted input that authorized users can supply. Attackers with high privileges — such as any user who can run complex queries — can remotely exploit this flaw over the network, across multiple protocols.
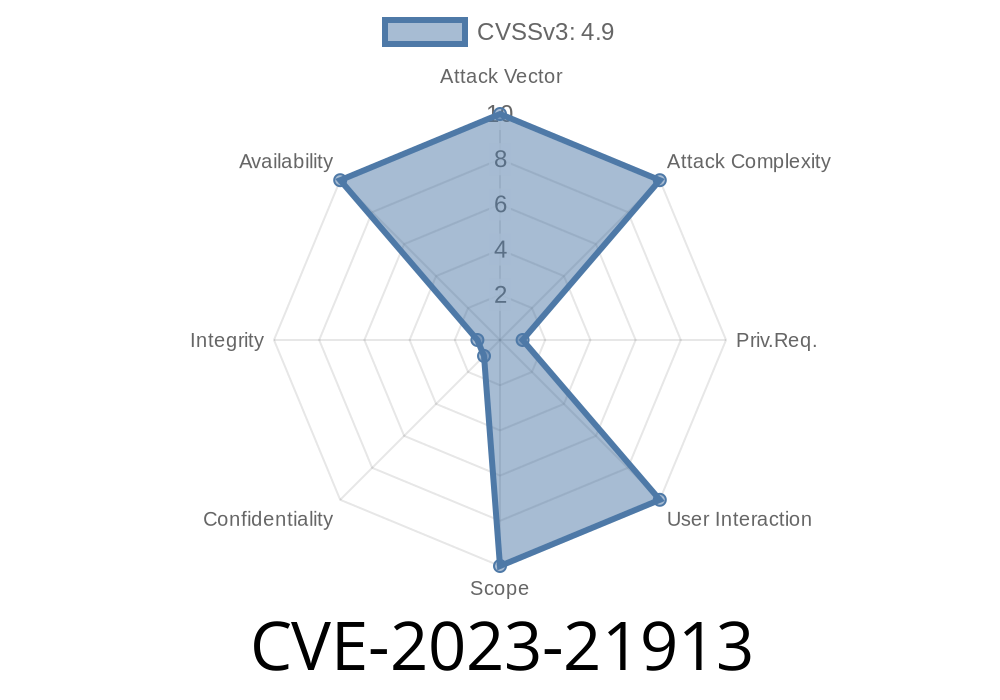
Availability impact: High (DoS - hang or crash)
- Confidentiality/Integrity impacts: None
- CVSS v3.1 Base Score: 4.9 (Scoring Details)
Exploit Details
This vulnerability is not exploitable by just anyone; attackers must be high-privilege users. For example, legitimate employees with over-provisioned accounts or users who somehow gained privileged credentials. The attacker does not need to be physically present at the server; exploitation is possible over the network using SQL clients.
In practice, exploitation involves running a specially crafted query that causes the MySQL Optimizer to process data incorrectly. The result is a server hang, crash, or both — causing a complete denial-of-service. Since there’s no user interaction required, and the attack can be repeated, a determined attacker can keep your database offline until you patch.
NOTE: Oracle has not publicly released detailed proof-of-concept exploits, and specifics are somewhat obfuscated in their advisories (See Oracle CPU Jan 2023). Here, we reconstruct a hypothetical example based on best-guess and similar Optimizer vulnerabilities reported by researchers.
Sample Proof-of-Concept (PoC)
*Disclaimer: Always run test code in isolated environments! Never on production systems!*
One common attack scenario on optimizer vulnerabilities is triggering a crash via deeply nested queries, misuse of subselects, or abnormal join patterns. Here’s a simplified example:
-- Hypothetical PoC: Crafted Query Triggers Optimizer Crash
USE test;
-- Suppose you have two tables:
CREATE TABLE t1 (a INT, b INT);
CREATE TABLE t2 (c INT);
-- Now, the attacker sends a strange query:
SELECT * FROM
(SELECT a, (SELECT MAX(c) FROM t2 WHERE t2.c > t1.b GROUP BY t2.c) AS max_c
FROM t1) AS derived
WHERE max_c IS NULL;
In vulnerable versions, the MySQL Optimizer might mishandle such a query, leading to a crash or hang. According to Oracle's fix notes, the crux of the problem is in how the Optimizer processes certain subqueries and joins (the details are withheld by Oracle for security).
For a more realistic test, tools like sqlmap with custom payloads or fuzzing frameworks can automate finding crash triggers. However, without Oracle’s private bug notes, full public PoC isn’t available.
Any place where internal users have broad SQL access
Remote attackers need only valid high-privilege credentials and network access (LAN/WAN, not localhost). On multi-tenant systems, a single malicious actor can crash the entire database, disrupting service for all users.
1. Patch Immediately
Oracle patched this in MySQL 8..32. Update as soon as possible!
# On Ubuntu/Debian:
sudo apt update && sudo apt upgrade mysql-server
# On RHEL/CentOS:
sudo yum update mysql-server
2. Restrict Privileges
Minimize “SUPER” or similar high-level rights. Use the principle of least privilege for account management.
3. Network Segmentation
Limit database access to trusted hosts/network segments. Do not expose MySQL directly to the internet.
4. Monitoring & Logging
Log all query errors and look for signs of repeated abnormal queries or crashes.
Further Reading & References
- Oracle CPU January 2023: https://www.oracle.com/security-alerts/cpujan2023.html
- National Vulnerability Database - CVE-2023-21913: https://nvd.nist.gov/vuln/detail/CVE-2023-21913
- MySQL 8..32 Release Notes: https://dev.mysql.com/doc/relnotes/mysql/8./en/news-8--32.html
Conclusion
CVE-2023-21913 is a classic example of a low-complexity, high-impact DoS bug: it’s easy to trigger, hard to detect before it happens, and devastating for system availability. If you operate MySQL 8..31 or earlier, upgrade right away and review your privilege and network access controls.
Protect your data — don’t let your optimizer become your downfall!
*This article is an exclusive, simplified explanation compiled from Oracle's official advisories and common security research. For production advice, always consult your DBA and vendor documentation.*
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC