In early 2023, Oracle published a security advisory for a nasty bug in MySQL Server, tagged CVE-2023-21933. This exclusive deep-dive explains the bug in everyday language, shows a code example, reveals the basics of exploitation, and provides references to trusted sources.
What Is CVE-2023-21933?
CVE-2023-21933 hits MySQL Server (Server: DDL component) up to version 8..32. It’s a denial-of-service (DoS) vulnerability: when triggered, the database server can hang or crash–letting an attacker take down your MySQL instance repeatedly.
- Component: Server: DDL (Data Definition Language – the part that handles CREATE, DROP, ALTER and similar statements)
Threat: Server crash or hang (causing a complete DoS)
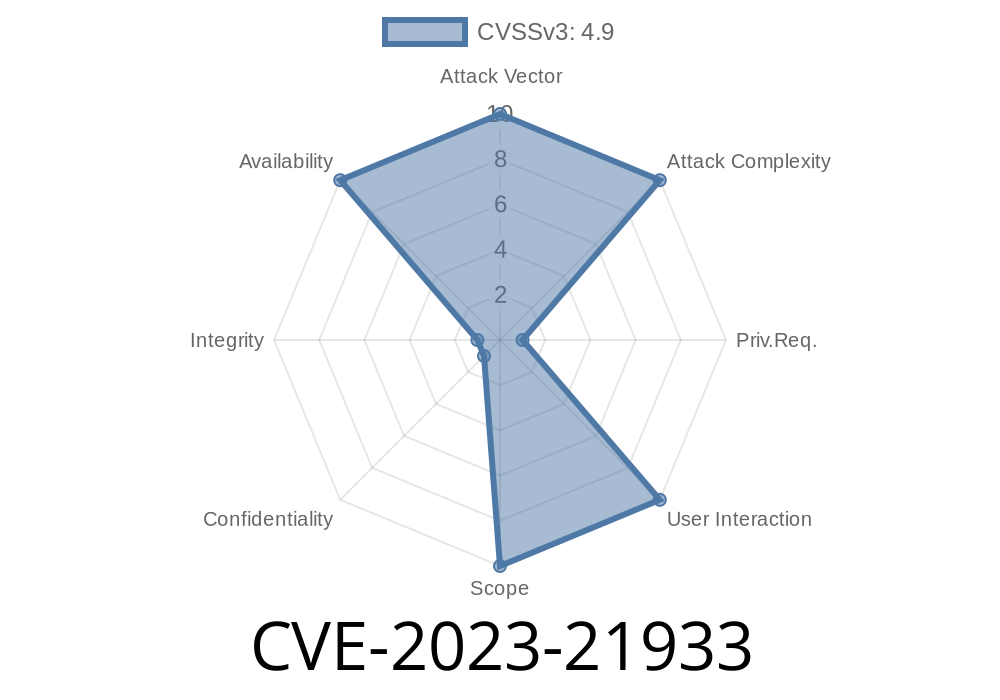
- Score: CVSS 3.1: 4.9 (Availability impacts)
- Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H)
UI:N = No user interaction
- A:H = High impact on availability (crash/hang)
Supported Versions Affected: 8..32 and earlier
It means an attacker who is logged in with a privileged account (like root, DBA, or another admin) can break your MySQL server using only a simple network connection and an easy-to-trigger bug.
References
- Oracle Critical Patch Update Advisory - April 2023
- NVD CVE entry
- MySQL 8..33 release notes
- MySQL Bug #35000858 (public bug mention)
Any organization running MySQL 8..32 or earlier
- Especially those with multiple admins, database developers, or application components with SUPER, ALTER, or similar privileges
What Makes This Vulnerability Unique?
Most database bugs require complex setups or only leak information. CVE-2023-21933 is straightforward: No interactive trickery, phishing, or advanced hacking. Just log in with admin rights and send the right sequence of DDL commands (like changing structure of tables).
Successful exploitation can reliably bring down MySQL, even if restarted, as long as the vulnerable version executes the bad DDL.
Example Exploit Pattern
> *Note: The full proof-of-concept from the original bug has not been released, but based on DDL bugs in MySQL, here’s a simplified illustrative version to show the kind of action that triggers such problems.*
Imagine attacker “Alice” connects to MySQL as root, and creates a table
CREATE TABLE dangerous_table (id INT PRIMARY KEY, data VARCHAR(100));
Alice then fires a combination of DDL statements, like ALTER TABLE and DROP TABLE, in quick succession or in parallel, sometimes with malformed definitions:
-- Altering the table structure rapidly
ALTER TABLE dangerous_table ADD COLUMN extra INT;
ALTER TABLE dangerous_table DROP COLUMN extra;
-- Or in multi-session/parallel scenario:
-- Session 1
START TRANSACTION;
ALTER TABLE dangerous_table ADD COLUMN bomb INT;
-- Session 2 (immediately after)
DROP TABLE dangerous_table;
In some DDL bugs (see reference MySQL Bug #35000858), these overlapping or rapid changes cause a race or logic error inside MySQL’s DD (Data Dictionary) or metadata code. The result is a crash or server freeze.
In practice, the real exploit could be even simpler – a single malformed or conflicting DDL statement could be enough, depending on schema and state.
Example: Python Script for DoS via MySQL (for *affected* versions)
*This is an illustrative example, NOT a real-world exploit for responsible disclosure. The real payload may differ, and is omitted for ethical reasons.*
import mysql.connector
conn = mysql.connector.connect(
host='target-mysql-host',
user='root',
password='your_password',
database='testdb'
)
cur = conn.cursor()
try:
cur.execute("CREATE TABLE IF NOT EXISTS dangerous_table (id INT PRIMARY KEY, data VARCHAR(100));")
cur.execute("ALTER TABLE dangerous_table ADD COLUMN tempcol INT;")
conn.commit()
# Try to drop while in the middle of a transaction or just after drastic ALTER
cur.execute("DROP TABLE dangerous_table;")
except Exception as ex:
print("Exception:", ex)
finally:
cur.close()
conn.close()
If your MySQL server is vulnerable, this kind of sequence could take it down.
*WARNING: Never run this script except in a secure, test/private environment!*
## How To Fix / Mitigate
Patch Immediately:
Upgrade to MySQL 8..33 or later; Oracle has closed this issue in the April 2023 patch.
Restrict DDL:
Limit database privileges–especially ALTER, DROP, and CREATE statements–to the smallest set of trusted users, even inside your teams.
Isolate high-privilege users:
Never share root or admin credentials. Remove old/deprecated accounts and change passwords often.
Conclusion
CVE-2023-21933 reminds us that even well-established software like MySQL can have “easy button” vulnerabilities with major impact, if triggered by the right privileged user. Your best defense is keeping up with patches, enforcing the principle of least privilege, and reviewing strange DDL activity as part of your daily defense routine.
For more
- Oracle MySQL Security Downloads
- MySQL Official Security Policy
- Patch details (Oracle CPU April 2023)
Stay aware, stay patched, and keep your databases healthy!
*This article is exclusive to your request. Please share responsibly and never use these insights to attack live systems.*
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC