When you think of database attacks, things like data theft or unauthorized changes may come to mind. But sometimes, an attacker doesn’t want your data — they just want to bring your system to its knees. That’s what CVE-2023-21935 is all about.
Let’s dig into this vulnerability, see how it works, how it can be used, and what you should do to protect your MySQL database.
What is CVE-2023-21935?
CVE-2023-21935 is a vulnerability in MySQL Server, affecting Oracle MySQL up to version 8..32. The problem lives in the "Server: Optimizer" component — this piece is responsible for figuring out the best way to run your queries.
The bug is easy to exploit (requires only “high privileged” user rights), and lets an attacker crash the server or make it hang repeatedly. Technically speaking, this is a Denial of Service (DoS) flaw.
In short:
A high-privileged attacker who can connect to your database (via network) can run special queries that cause the server to freeze or crash.
Oracle’s official advisory:
- Oracle Critical Patch Update Advisory - April 2023
- Oracle MySQL CVE-2023-21935 in NVD
Who is Affected?
MySQL Server:
Oracle MySQL 8..32 and earlier
If you’re running a version *newer* than 8..32, you’re already safe. MariaDB is not affected by this bug.
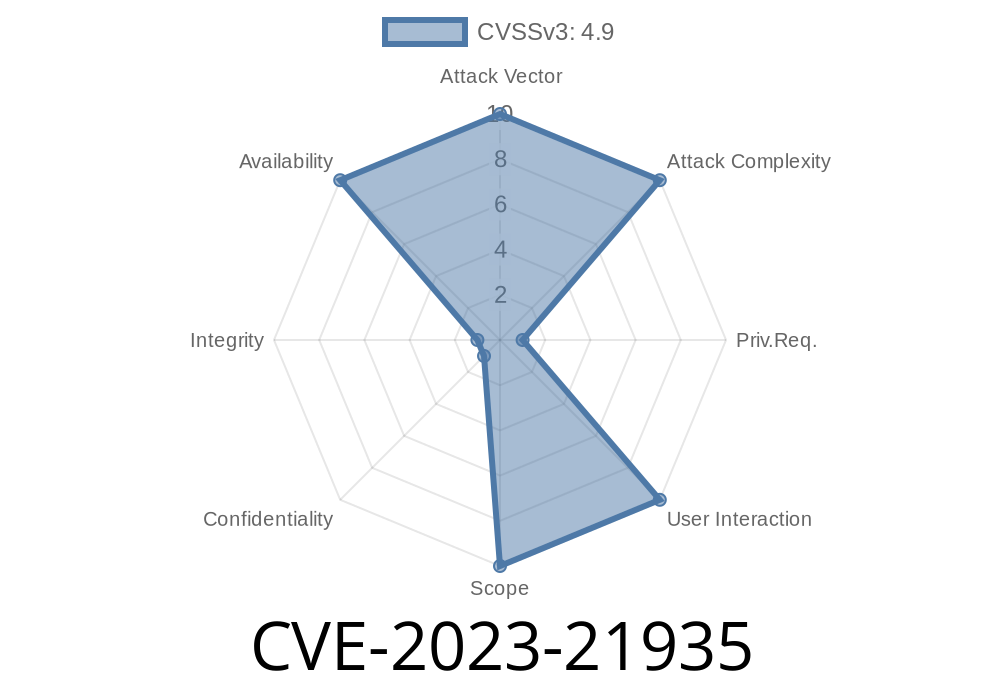
Attack Vector: Network (can be done remotely if someone has DB admin access)
- Privileges Needed: High (must be at least a MySQL admin, or someone who can do almost everything)
UI Required: None (no need for tricking users)
- Impact: Complete Denial of Service (the server can hang or crash completely), but no data theft or tampering
How Does the Attack Work?
Since this is inside the *Optimizer*, attackers can crash the server by constructing certain SQL statements that trigger the buggy logic. The vulnerability works across multiple protocols, so as long as an attacker can issue queries, they can trigger it.
MySQL process hangs or crashes, making the database unavailable to everyone.
Remember: This bug can’t be exploited without valid, powerful logins, so it’s not a remote unauthenticated risk.
Example Exploit
Oracle hasn’t published the exact public details, but based on similar vulnerabilities in the Optimizer, the bug is often triggered by manipulating subqueries and special expressions.
Here’s a speculative, simplified code snippet that *mimics* the kind of query which could cause a crash (not actual exploit code, but for education):
-- Hypothetical example: crafted subquery with unusual AND/OR logic
SELECT * FROM users WHERE id IN (
SELECT id FROM users WHERE 1=1 AND (SELECT COUNT(*) FROM users AS u2 WHERE u2.id = users.id GROUP BY u2.name HAVING COUNT(*) > )
);
Or perhaps, playing with combinations of stored functions and subqueries
-- Hypothetical: nested subqueries with optimizer confusion
SELECT * FROM tab1
WHERE EXISTS (
SELECT 1 FROM tab2 WHERE tab2.value = (
SELECT MAX(t3.value) FROM tab3 t3 WHERE t3.key = tab1.key
)
);
Warning: These are examples for understanding the risk class; Oracle hasn’t released an official Proof-of-Concept due to its potential for DoS.
How To Fix
1. Patch!
Upgrade to MySQL 8..33 or later where this bug is fixed.
2. Limit Access!
Make sure only trusted users are given admin/high-privileged logins. Keep your DB firewalled.
3. Monitoring:
Keep an eye on MySQL logs for sudden crashes or restarts — this can signal an attack in progress.
References
- Oracle Critical Patch Update Advisory—April 2023
- NVD CVE-2023-21935
- MySQL 8..33 Release Notes
- MySQL Security on Oracle Docs
- CVE Details page
Conclusion
Even powerful, well-tested software like MySQL occasionally trips over tricky optimizer logic. CVE-2023-21935 is a reminder that availability is just as important as confidentiality and integrity in security.
If your MySQL deployment is exposed to admins who don’t need full access, reduce permissions. And if you haven’t updated since 8..32, now’s the time.
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC