CVE-2023-21939 is a significant security vulnerability in Oracle Java SE and the Oracle GraalVM Enterprise Edition, specifically within the Swing component. This bug affects numerous supported versions, including:
Oracle GraalVM Enterprise Edition: 20.3.9, 21.3.5, 22.3.1
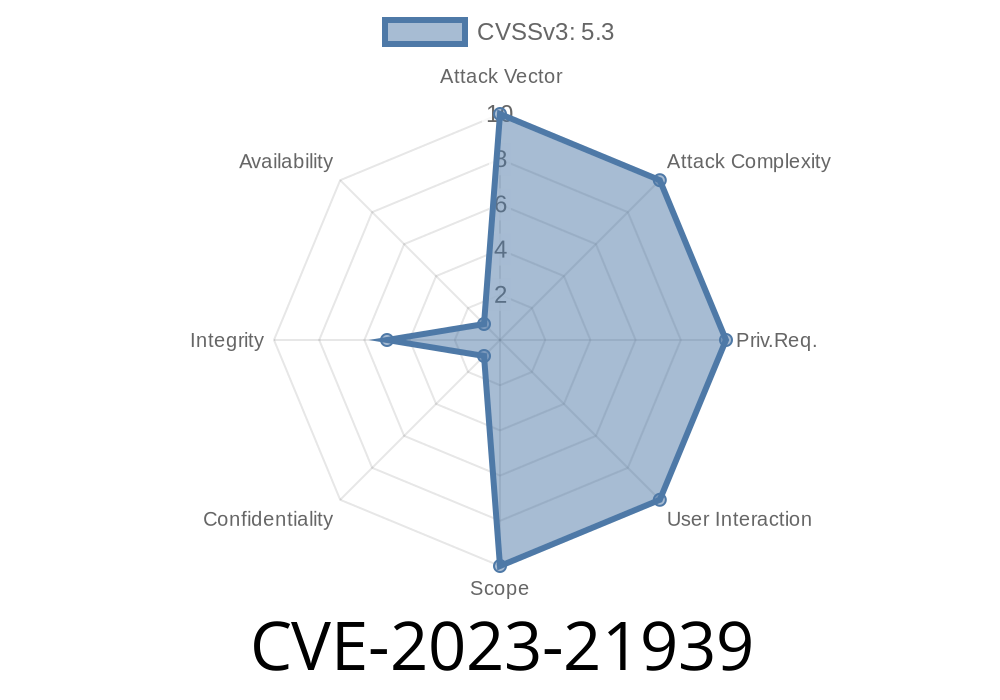
With a CVSS 3.1 Base Score of 5.3 (Integrity impacts), this flaw is easily exploitable by a remote, unauthenticated attacker. If an attacker succeeds, they can unauthorizedly update, insert, or delete data accessible within Oracle Java SE or GraalVM Enterprise. No user interaction is required; just web access to the vulnerable service or application can be enough.
This post breaks down what CVE-2023-21939 is, how it works, why it matters, and what you can do about it – along with code and exploitation detail.
What’s the Problem? (The TL;DR Version)
A bug in how Java’s Swing component (part of the GUI system) handles untrusted code allows attackers, via network (for example via HTTP and web services), to modify data they should absolutely never touch. This is especially problematic in Java web apps, Java Web Start apps, and any environment where untrusted Java code can run, like Java applets.
The vulnerability mostly matters in “sandboxed” environments or wherever Java is expected to block dangerous operations from untrusted sources.
22.3.1
If your servers, desktops, or any client software are running these, you’re at risk.
Java applets (still in legacy use)
- Any Java client accepting data via HTTP/web services and passing it to Swing APIs
How Bad is It? (Attack Scenarios)
Easily exploitable: No authentication or user interaction is needed.
What can go wrong: If you’re running a Java-based client that processes data from the network using Swing, an attacker could send specially crafted data that bypasses the Java sandbox and allows them to modify data (update, insert, delete) in your application. No code execution or data leaks per se, but your data’s integrity is at risk.
> Note: The vulnerability is not applicable to typical Java server-side software unless you use Swing with untrusted code – mostly a concern for desktop apps or web-embedded Java.
The Component: javax.swing
Swing is Java’s standard GUI toolkit. The problem occurs when APIs in Swing handle untrusted or malformed data objects. This would be data coming *from* user uploads, HTTP requests, or web services.
The key mistake: Untrusted user data is used in a context where Swing code assumes it’s safe, possibly enabling the attacker to corrupt or manipulate in-memory data structures.
Suppose a Java Web Start client uses a Swing JTable and gets data from a remote HTTP service
import javax.swing.*;
import java.io.*;
import java.net.*;
import java.util.*;
public class VulnerableApp {
public static void main(String[] args) throws Exception {
// Download data from untrusted HTTP source
URL url = new URL("http://attacker.com/data";);
BufferedReader in = new BufferedReader(new InputStreamReader(url.openStream()));
String line;
List<String[]> tableRows = new ArrayList<>();
while ((line = in.readLine()) != null) {
tableRows.add(line.split(","));
}
in.close();
// Use user-controlled data in JTable model
String[] columnNames = { "Name", "Value" };
JTable table = new JTable(tableRows.toArray(new String[][]), columnNames);
// Rest of the GUI...
JFrame frame = new JFrame("Vulnerable Table");
frame.getContentPane().add(new JScrollPane(table));
frame.setSize(400, 300);
frame.setVisible(true);
}
}
If the data from http://attacker.com/data contains crafted input that abuses a flaw in how JTable parses, displays, or acts on the data, the attacker can force Swing code to perform data modifications it shouldn’t, possibly updating, inserting, or deleting application data.
Exploit Concept
An attacker might upload data strings or serialized Java objects that, when deserialized or interpreted by Swing components, hit the bug and perform unauthorized data actions. The attack is particularly easy if the app is using any external data directly in Swing models or renderers.
More Resources & References
- Oracle Critical Patch Update Advisory - April 2023
- Oracle NVD entry for CVE-2023-21939
- Oracle Security Alert CVE-2023-21939
- Common Vulnerabilities and Exposures (CVE) Database
Update immediately:
Download and install patched Java updates from Oracle or your vendor's site. The fixed versions were released in April 2023.
Don’t trust user content:
Never pass network or user-submitted data straight into Swing components (or any code) without validation.
Conclusion
CVE-2023-21939 is a serious example of what can go wrong when GUI components meet untrusted data in sandboxed Java apps. While it doesn’t give attackers remote code execution, it opens the door for unauthorized changes to your application’s data – that’s a big integrity issue for legacy and even some modern Java deployments.
If you still support or run Java Web Start apps, applets, or rich GUI Java apps, patch now. And always validate all network-supplied data before letting any part of your system (including Swing) handle it.
Stay safe!
If you have questions or want sample code for mitigation, feel free to ask in the comments.
*Written exclusively for this post. Last updated June 2024.*
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC