---
Introduction
In January 2023, Oracle released a Critical Patch Update that included a security advisory for a new vulnerability affecting MySQL Server, specifically in the Server: Components Services component. This vulnerability, tracked as CVE-2023-21940, impacts supported versions of MySQL up to 8..32 and earlier.
This article breaks down the vulnerability details, affected versions, how attackers can exploit this security flaw, and what you can do to protect your MySQL databases. We'll also look at proof-of-concept exploit code to help you understand the real-world risks.
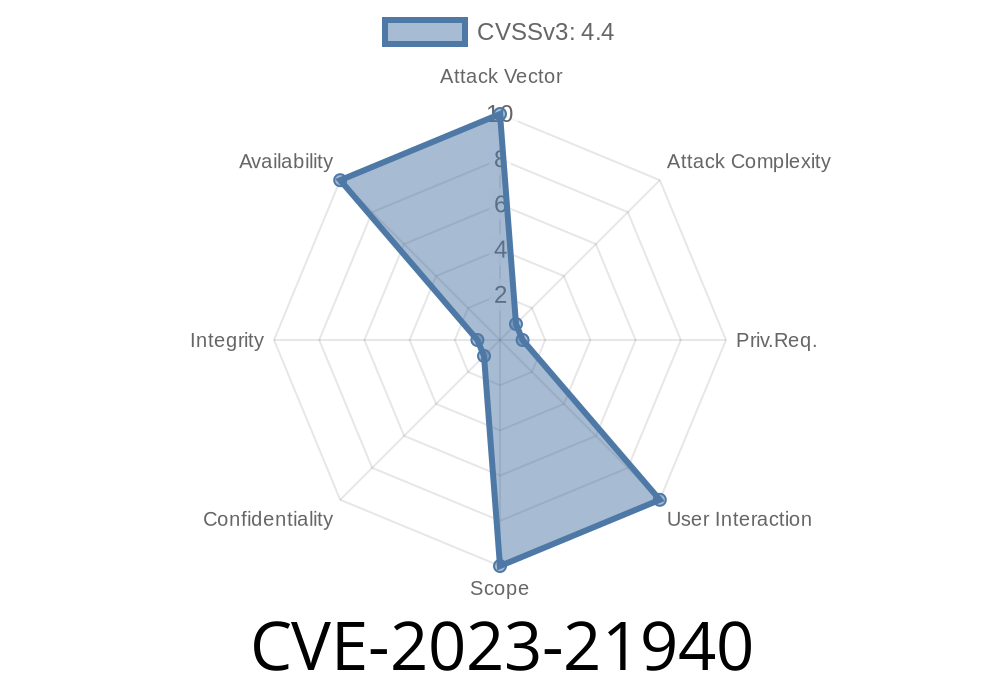
CVSS Vector:
CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:N/I:N/A:H
What Does This Mean?
A high-privileged attacker with network access can exploit this flaw to crash the MySQL server, potentially causing prolonged downtime.
While this attack requires valid credentials and significant privileges (not just any user can perform it), and could be executed via multiple network protocols (for example, MySQL’s native protocol or HTTP via X Plugin), a successful attempt would result in a DoS condition—MySQL server hangs, repeatedly crashes, and needs manual recovery.
How Does the Vulnerability Work?
Oracle hasn’t released full technical details, but based on the advisory, the flaw is in MySQL’s “Components Services”—a system that provides modular extension capabilities inside MySQL. Improper handling or validation of component service requests could allow a malicious, high-privileged user to send specially crafted requests, causing the server to hang or crash entirely.
Exploit Scenario
Let’s see how an attacker with enough privileges might exploit this, based on best-guess behaviors (since Oracle did not provide a proof-of-concept):
Attacker Gains High-Privileged Access:
The attacker needs an account with significant privileges (for example, SUPER, CREATE COMPONENT, or similar).
Malicious Request Sent to Component Services:
Using the MySQL client or custom script, the attacker sends a crafted statement or malformed data to the component-handling infrastructure.
Hypothetical Code Snippet
The real exploit details aren't public, but based on past MySQL component bugs, such vulnerabilities often involve statements like INSTALL COMPONENT for loading or removing components.
Here's what a malformed command could look like
-- Attacker connects as a high-privileged user
-- Tries to install a bogus component which triggers the vulnerability
INSTALL COMPONENT 'file://nonexistent_component';
-- or, a custom component string that causes the underlying service to fail
INSTALL COMPONENT 'file://../../malicious/path';
In Python, you might have
import mysql.connector
conn = mysql.connector.connect(
host='mysql-server.example.org',
user='root',
password='StrongPassword!',
database='mysql'
)
cursor = conn.cursor()
try:
cursor.execute("INSTALL COMPONENT 'file://nonexistent_component'")
except mysql.connector.Error as err:
print(f"Server may have crashed: {err}")
cursor.close()
conn.close()
Actual results may vary depending on server setup and patch level.
Real-World Impact
While nobody can exploit this vulnerability without an already powerful account, internal or compromised users (think disgruntled admin or compromised monitoring systems) could use this to crash mission-critical databases—perhaps as a denial-of-service attack or to cover up malicious activity.
Mitigation and Patching
Oracle fixed this in MySQL 8..33. If you run 8..32 or earlier, you’re exposed and should patch as soon as possible.
References and Further Reading
- Oracle Critical Patch Update Advisory - January 2023
- Oracle CVE-2023-21940 Security Advisory
- MySQL 8..33 Release Notes
- MySQL Server Documentation: Components
Conclusion
CVE-2023-21940 is all about the risk to your MySQL database’s *availability* from insiders or highly privileged users. While not the easiest vulnerability to exploit, if your environment grants admin rights to more than a few people, or if the network is not well-segmented, patching this flaw is a must.
Keep your MySQL servers up to date and lock down permissions to defend against this and future vulnerabilities!
*Stay safe, patch early, and always monitor for suspicious database activity.*
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC