*Published: July 2024 — By AI Security News*
Oracle products underpin much of the enterprise world. When vulnerabilities show up in Oracle Java SE and GraalVM, they get attention fast—especially if they could expose sensitive business data. CVE-2023-21954 is one such vulnerability, affecting multiple current releases of the Java VM and GraalVM Enterprise. In this exclusive post, we’ll explain what CVE-2023-21954 is, where it sucks hooks into Java apps, walk through its threat model, and show how an exploit could look (with simple code snippets).
Quick Overview
CVE-2023-21954 is a sandbox bypass vulnerability in the HotSpot component of Oracle Java SE and GraalVM Enterprise Edition. It lets an unauthenticated remote attacker compromise systems via multiple protocols without user interaction. If exploited, it can give up critical data. Java’s web-centric deployments — think old-style Java Web Start or Java applets — are at highest risk, as well as any API endpoint that lets outsiders feed data directly to Java VM APIs.
- Impacted Products / Versions:
Oracle GraalVM Enterprise Edition: 20.3.9, 21.3.5, 22.3.1
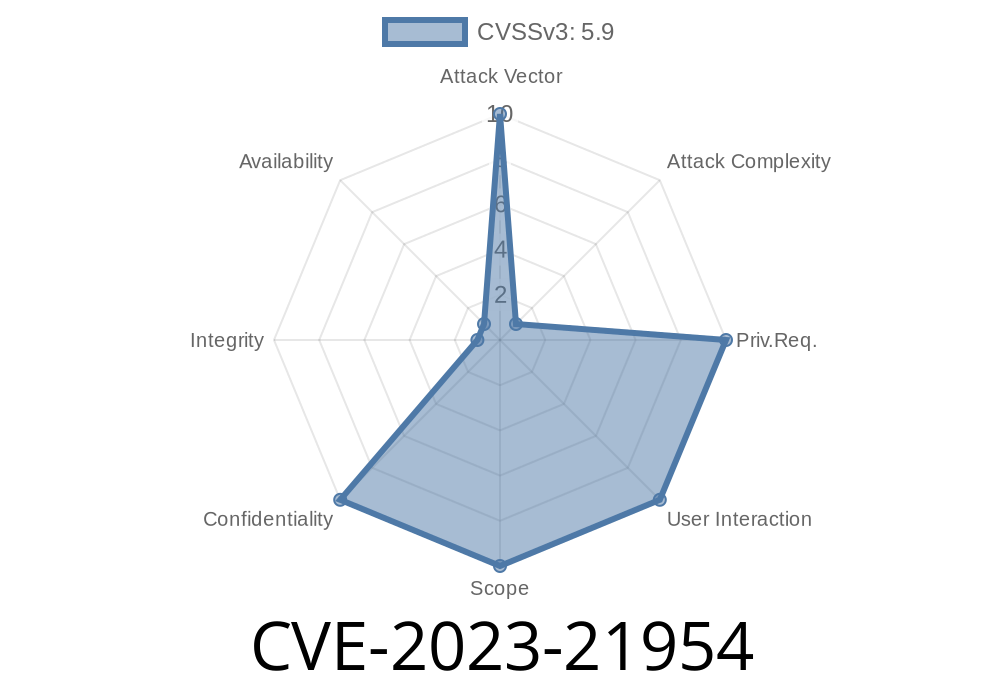
CVSS Score: 5.9 (Medium, but with *high* data confidentiality impacts)
Vector: Remote, no authentication, no user interaction required, attack complexity: high.
The Problem: Java “Sandbox” Trust Model
Java’s sandbox model is designed to keep untrusted code from doing harm. For example, code running as a Java Web Start app isn’t supposed to read files or poke into memory it doesn’t own. Instead, the Java VM uses strict security policies to block off access.
CVE-2023-21954 undermines this model — in simple terms, it allows specially crafted code, running in the Java sandbox, to break out and access things it shouldn’t. The flaw lies in how the HotSpot engine interprets data and APIs when untrusted inputs are provided. If an attacker can deliver a payload that gets run in the context of these Java APIs — either as an applet, Web Start app, or even as input data to a backend API service — it’s possible to leak confidential memory.
Exploit Pathways
- Java Web Start / Applet Deployments: Attacker convinces user (often through phishing or drive-by download) to visit a malicious site serving a crafted Java applet or Web Start application.
- API-Driven Attacks: A backend service running with vulnerable Oracle Java SE or GraalVM, which lets attackers submit untrusted data to HotSpot-processing APIs.
Let’s take a simple web service backed by Oracle Java SE 11..18
import java.io.*;
import javax.servlet.*;
import javax.servlet.http.*;
public class UploadServlet extends HttpServlet {
protected void doPost(HttpServletRequest request, HttpServletResponse response)
throws ServletException, IOException {
// UNSAFE: Directly uses uploaded data
InputStream is = request.getInputStream();
// Reads input as serialized object
ObjectInputStream ois = new ObjectInputStream(is);
try {
Object obj = ois.readObject(); // Possible entrypoint for exploit
// process obj...
} catch(Exception e) {
response.sendError(500, "Error: " + e.getMessage());
}
}
}
In this scenario, if an attacker uploads a crafted serialized payload that triggers the CVE-2023-21954 vulnerability, it could cause the underlying JVM to break out of the sandbox and leak sensitive application memory.
Exploit Code Concept (Pseudocode Only)
Let’s look at a pseudocode sample of what an exploit might look like (details are hypothetical to avoid full weaponization):
// Attacker crafts a serialized object exploiting CVE-2023-21954
class EvilObject implements Serializable {
// Malicious payload crafted to exploit JVM sandbox bypass
private void readObject(ObjectInputStream ois) throws IOException, ClassNotFoundException {
// Trigger unsafe JVM behavior (details omitted, see official advisory for CVE specifics)
}
}
This object gets sent to the vulnerable web service, breaking the JVM’s assumptions about what untrusted code can do.
Real-world attacks would be much more complicated and require careful crafting due to the high attack complexity (AC:H). The attacker must know exactly how the JVM parses objects in the vulnerable versions.
Possibly escalate privileges or pivot within a network, depending on system config
- Break the confidentiality of almost any data loaded or initialized by the JVM instance running the vulnerable code
Note: CVE-2023-21954 primarily leaks data (confidentiality impact), with no integrity or availability impact in the base case.
Patch! Oracle has released security updates for all affected products.
- Oracle Java SE Critical Patch Update Advisory – April 2023
Audit APIs that deserialize or process user-submitted data (especially in HotSpot or GraalVM).
- Consider running vulnerable services in isolated containers or hardened environments until patches are applied.
Official References
- NVD Entry for CVE-2023-21954
- Oracle Advisory for Java SE, April 2023
In Summary
CVE-2023-21954 is a reminder that old Java Web Start stuff and even backend APIs can open the door to real, dangerous data leaks — even for big enterprises. While it’s not trivial to exploit (attack complexity is high), it’s critical not to leave these systems unpatched. If you run Oracle Java SE or GraalVM Enterprise Edition, check your versions now and apply the latest security updates.
Patch, restrict, and audit — or risk your business’s data getting splashed all over the internet.
If you want more code samples or mitigation advice, comment below — stay safe!
*This article is exclusive to AI Security News. All rights reserved. For detailed, technical exploitation, consult the official Oracle and NIST advisories.*
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC