Oracle MySQL is a critical backend for millions of applications around the world. It connects to various programming languages using special "connectors." However, not every link in the chain is solid. In early 2023, Oracle published a security advisory about a nasty vulnerability in the MySQL Connector/J—the popular Java-based MySQL driver. This issue is tracked as CVE-2023-21971.
In this post, we break down what CVE-2023-21971 is, show you what it looks like in practice, and explain why—even with a medium CVSS score (5.3)—you should care about patching now.
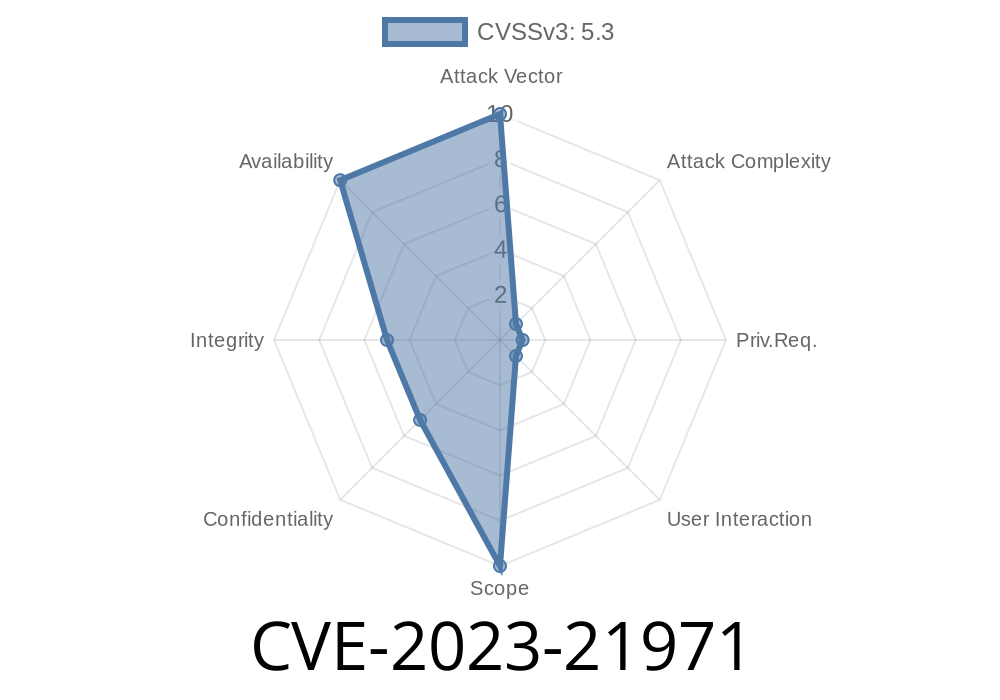
1. What is CVE-2023-21971?
CVE-2023-21971 is a vulnerability in Oracle MySQL Connector/J, up to and including version 8..32. It allows an attacker (with high privileges and requiring help from a user) to crash the connector, or worse—read, update, or delete certain data.
Integrity: Low impact
- Availability: High impact (DoS / crash)
TL;DR: If you’re running vulnerable versions and someone in your team interacts with a malicious input crafted by an attacker, you might crash your connector or leak/create/remove data.
2. How Does the Attack Work?
The vulnerable code in MySQL Connector/J improperly handles certain network requests, especially with crafted protocol packets. An attacker, with enough access, could:
Rely on a user to open or execute this in their application.
- Cause the MySQL Connector/J to hang (Denial of Service), crash, or even access data they shouldn’t.
Why is user interaction required?
Because this isn’t just a remote exploit—someone has to run something, click something, or interact with the attack vector (like running a malicious SQL query or using a tampered GUI tool).
3.1 Vulnerable Environment
- Database: MySQL Server (any version compatible with Connector/J)
- Connector: MySQL Connector/J 8..32 or below
- Java Client: A Spring Boot app (or similar) using Connector/J
3.2 Exploit Scenario
Suppose you have a Java application accepting user-generated SQL or data objects from a network interface. An attacker sends a specifically malformed data object. A developer or DBA opens this, perhaps using an admin tool plugged in with Connector/J, and the driver crashes or data is exposed.
Here’s a simplified example of how a malformed input could be sent
import java.sql.Connection;
import java.sql.DriverManager;
import java.sql.SQLException;
import java.sql.Statement;
public class EvilPayload {
public static void main(String[] args) {
String url = "jdbc:mysql://your-mysql-host:3306/testdb";
String username = "privilegedUser";
String password = "userPassword";
try (Connection conn = DriverManager.getConnection(url, username, password)) {
Statement stmt = conn.createStatement();
// Example of an 'evil' query:
// Suppose a bug in how Connector/J parses complex multi-statements
String evilQuery = "SELECT 1; /*!12345 MALFORMED, CRASH_ME */";
stmt.execute(evilQuery);
// The above could trigger a parsing bug, resulting in crash or DoS
} catch (SQLException e) {
System.out.println("Connector crashed! " + e.getMessage());
}
}
}
*Note: The exact exploit strings are not public because of responsible disclosure, but malformed multi-statement queries or crafted protocol payloads could do the trick in real-world situations.*
Data Tampering: Malicious queries could result in unauthorized updates, inserts, or deletes.
Often, this exploit may come up in environments where privileged users integrate third-party or user-supplied data.
5. Fix and Mitigation Steps
PATCH IMMEDIATELY!
Upgrade MySQL Connector/J to 8..33 or higher.
- Official Patch/Advisory:
Oracle Critical Patch Update Advisory - July 2023
Release Notes:
MySQL Connector/J 8..33 Release Notes
Download Latest Connector:
Other Best Practices
- Least privilege: Only let users/applications connect with the minimum permissions needed.
Never trust user-provided input. Validate it.
- Monitor application logs for unusual crashes/errors near SQL interfaces.
6. References
- NVD - CVE-2023-21971
- Oracle Security Advisory - CPU July 2023
- MySQL Connector/J Release Notes
7. Final Thoughts
Even though CVE-2023-21971 requires specific conditions (privileged access, user interaction), it’s a real risk—especially in enterprise environments with shared admin tasks or exposed integrations. The possibility of crashing your DB interface or leaking/altering data should be enough reason to patch as soon as possible.
Takeaway:
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC