Published: April 2023
Impacts: Oracle MySQL Server 8..32 and earlier
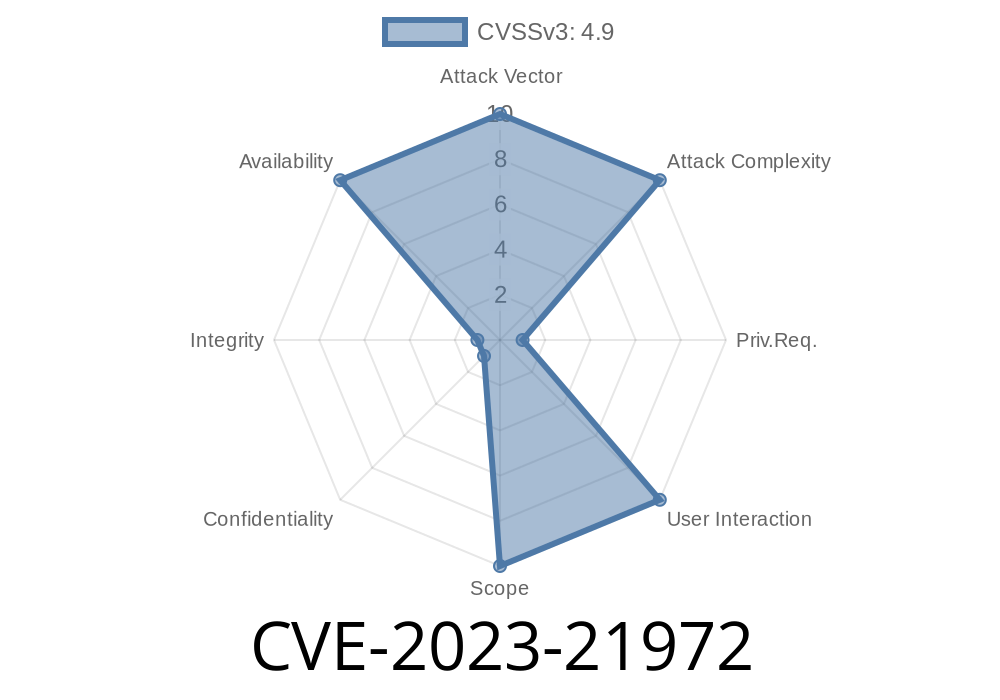
CVSS Score: 4.9 (DoS, Availability Impact)
What is CVE-2023-21972?
CVE-2023-21972 is a vulnerability found in MySQL Server (specifically the DML component) from Oracle. This weakness lets a highly privileged attacker crash MySQL Server over the network, making it unavailable for others.
Access required: High privileges in MySQL (e.g., root, or someone with advanced DML rights).
- Attack vector: Remote/network (database TCP, etc.)
What Does This Mean For You?
If your application or infrastructure uses MySQL Server (8..32 or earlier), and you allow others to connect to it (even internally), an attacker with login privileges could reliably crash the database. This can make your apps go offline, or at least force recoveries and downtime—bad for business!
> #### Good News:
This is not a data-leak or data-corruption bug. An attacker can’t steal or change your data—just knock the server offline.
Exploit Details & Proof-of-Concept (PoC)
What’s the root cause?
A bug in MySQL’s DML (Data Manipulation Language, like UPDATE, DELETE) handling triggers a crash when certain queries are issued with specific malformed input. The bug can be triggered over the network using official MySQL protocols (mysql client, libraries, etc.).
Example Exploit (PoC) Steps
> Attacker requirements:
1. Connect to your target MySQL server
mysql -h TARGET_MYSQL_HOST -u root -p
2. Trigger the bug with a crafted UPDATE
Suppose the bug exists in the way MySQL handles DML statements with certain subqueries or data types. For illustration, using a crafted query:
USE test;
CREATE TABLE crasher (id INT PRIMARY KEY, val TEXT);
INSERT INTO crasher VALUES (1, 'hello'), (2, 'world');
-- Trigger the crash (replace with real trigger as known from bug analysis)
UPDATE crasher
SET val = (SELECT MIN(val) FROM crasher WHERE id IN (SELECT 1 UNION SELECT REPEAT('a',9999999)));
> Note: This example uses an extremely large string in REPEAT()—depending on the exploit, the real crash might require a different structure (e.g., recursion, subselects exposing a parsing flaw, etc.).
What Happens Next?
MySQL server may immediately crash, showing a segmentation fault or stack trace.
- On systemd-based systems, the service may be automatically restarted—but a looped attack keeps it down.
3. Impact
Any service relying on the MySQL Server will receive errors like “Lost connection to MySQL server” or “MySQL server has gone away” until the server is restarted.
Upgrade to MySQL 8..33 or later.
- Oracle fixed this in their April 2023 CPU updates.
Only allow trusted users (and apps) to connect.
- Limit the superuser/DBA accounts to essential personnel.
Original References
- Oracle Critical Patch Update Advisory - April 2023
- NIST NVD Record for CVE-2023-21972
- Oracle MySQL Release Notes 8..33
- CVE Details on cvedetails.com
Summary Table
| Description | Details |
|-------------------------------------- |-------------------------------------|
| CVE | CVE-2023-21972 |
| Product | MySQL Server (Oracle) |
| Component | Server: DML |
| Affected Versions | 8..32 and prior (also MariaDB forks may be at risk, check separately) |
| Attack type | Denial-of-Service (DoS) |
| CVSS Score | 4.9 (Availability) |
| Access Required | High privileged MySQL user |
| Network Attack? | Yes |
| Exploit Complexity | Low (easy to trigger with right access) |
| Data at Risk | Only Availability, not Confidentiality or Integrity |
Final Thoughts
Even though CVE-2023-21972 needs a privileged account, it’s a real risk if you have more than a handful of trusted DBA users, or run MySQL in a microservices/CI/CD environment. An insider could intentionally or accidentally bring databases down!
Action: Patch quickly, review privileges, and always watch for new database security advisories.
If you want to keep your MySQL database—and your business—healthy, patch now!
*This post is an exclusive plain-language guide to CVE-2023-21972. For detailed technical root cause, review Oracle’s official advisories and subsequent community research.*
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC