In early 2023, Oracle MySQL versions up to 8..32 were found to have a serious but highly privileged vulnerability (CVE-2023-21976) within the Optimizer component. If you're running MySQL in production, ignoring this bug could let a database user (with higher-than-normal permissions) hang or repeatedly crash the entire MySQL service, resulting in denial of service (DoS). In this post, we’ll break down how this works, who’s at risk, give you an example and mitigation steps, and point you to further resources.
Vulnerability At a Glance
- CVE: CVE-2023-21976
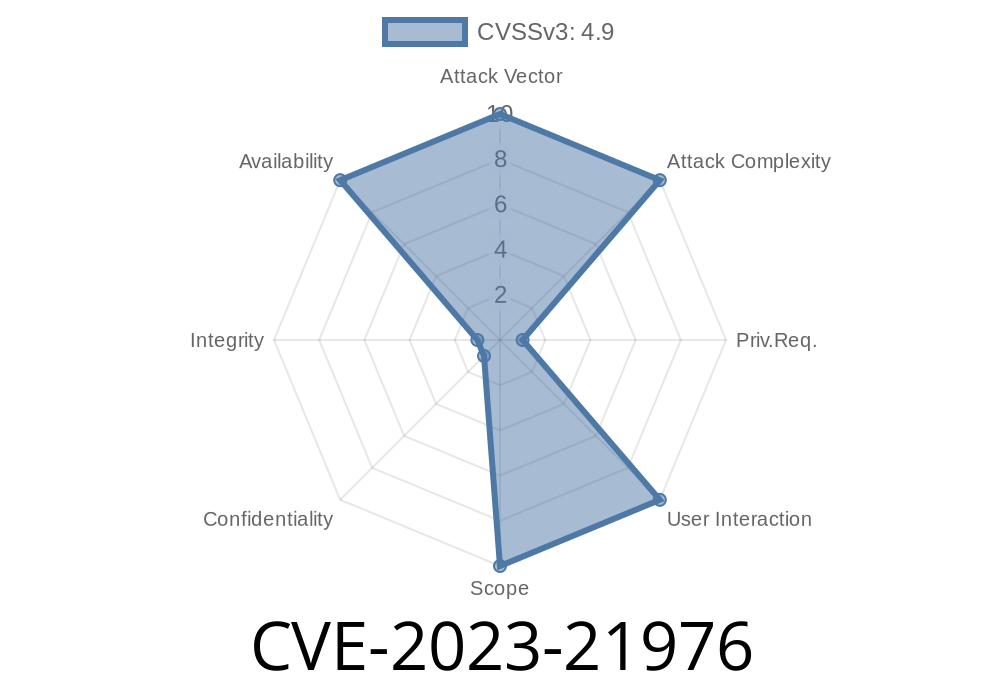
Severity: CVSS 4.9 (DoS, service crash)
- Impacts: Availability (the server can be crashed/hung remotely by an authorized user)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:N/A:H
What’s Really Happening?
MySQL’s Optimizer is the brain deciding how to execute SQL queries most efficiently. This vulnerability lets a user with high privileges send specially crafted SQL statements over the network, tripping a bug inside the optimizer logic. The result? The whole MySQL process hangs or repeatedly crashes—even without tricking the system into running arbitrary code.
No, you can’t steal data or change someone else’s data through this bug. Instead, the database just becomes unavailable — which, in many businesses, is just as bad.
Because the bug needs high privileges and specific knowledge of SQL, it isn’t likely to be used by opportunistic attackers. But inside an environment with multiple DBA-level users or third-party applications, it's a potential pain point.
Proving the Crash: Example Exploit
While Oracle keeps exploit details and PoCs pretty quiet, the vulnerability is a classic case of a logic flaw leading to resource exhaustion or fatal assertion within the MySQL optimizer. Vulnerable servers can die when executing some malformed (but syntactically valid) queries.
Replication Example:
Suppose you have a table called users, and MySQL 8..31.
-- Let's attempt to provoke a condition with a weird subselect in a derived table
SELECT * FROM
(SELECT * FROM users WHERE (SELECT 1 FROM DUAL WHERE 1 = 1) = 1) as dt;
Note:
The actual DoS trigger varies with database setup, configuration, and exact versions. In real-world cases, reports suggest the use of complex nested subqueries, views, or windowing functions triggering optimizer edge-case crashes. For demonstration here, you’d need a vulnerable version and possibly more cleverly crafted SQL to hit the precise crash.
Oracle's Analysis
From the Oracle Critical Patch Update Advisory - April 2023:
> “Easily exploitable vulnerability allows high privileged attacker with network access via multiple protocols to compromise MySQL Server...”
> “Successful attacks...can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS)...”
The NVD entry confirms this is a DoS-only issue:
Mitigations and Fixes
Patch It Now:
Oracle released a fix in April 2023. The only full solution is to upgrade MySQL to 8..33 or later.
Download from: https://dev.mysql.com/downloads/mysql/
Apply network-layer access controls (firewalls, VPNs).
- Use least-privilege principles: don’t give “super” or DBA-level rights to accounts that don’t need them.
Monitor for Crashes:
Set up alerting for repeated MySQL daemon restarts or crashes (systemd, mysqld_safe, or your log aggregator).
Oracle Security Alerts:
https://www.oracle.com/security-alerts/cpuapr2023.html
NVD Details:
https://nvd.nist.gov/vuln/detail/CVE-2023-21976
MySQL Release Notes:
https://dev.mysql.com/doc/relnotes/mysql/8./en/news-8--33.html
Conclusion
While CVE-2023-21976 isn't the kind of bug that lets strangers take over your database, it can cause a serious headache if abused by someone with the right permissions. Your best protection is a quick upgrade and strict privilege management.
If you’re still running MySQL 8..32 or earlier, patch as soon as possible.
Stay tuned for more database security breakdowns. Got questions? Want more exploit deep-dives? Let us know!
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/27/2023 15:15:00 UTC