---
Introduction
In April 2023, Oracle published details about a fresh vulnerability tracked as CVE-2023-21984. This security weakness exists within the HTTP-processing libraries of *Oracle Solaris*, a popular enterprise-grade UNIX operating system.
Despite being rated only as a "medium" (6.5) on the CVSS v3.1 scale, this flaw is easily exploitable and could allow even low-privileged attackers to crash critical systems. In this article, we’ll break down what CVE-2023-21984 is, how it can be exploited, what the risks are, and how users and sysadmins can protect their Solaris installations.
Product: Oracle Solaris 11 (component: Libraries)
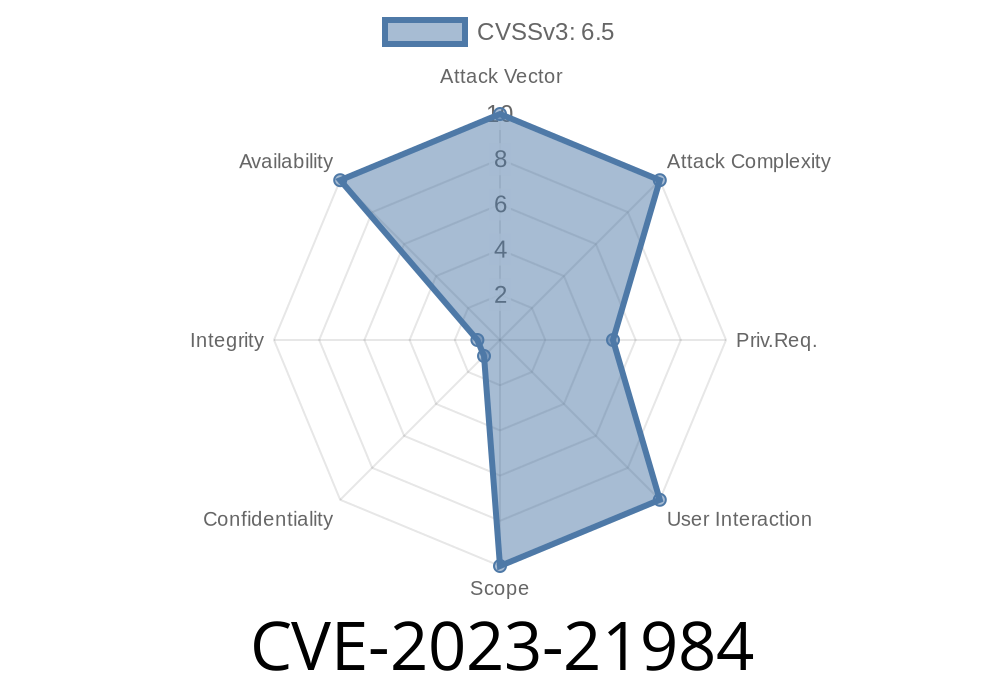
- CVE: CVE-2023-21984
User Interaction: None
- Impact: Complete Denial of Service (system hang/crash)
CVSS v3.1 Score: 6.5 (Availability impacts)
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H
How Does the Vulnerability Work?
The vulnerability resides in the HTTP-handling libraries bundled with Oracle Solaris 11. It allows a remote attacker with network access and minimal privileges to send specially-crafted HTTP requests that can crash or hang services, rendering the system unavailable.
This could be exploited in environments where Solaris is used to host web services, REST APIs, or any application using HTTP features in the system libraries.
Technical Breakdown
While Oracle's advisory does not reveal deep technical details (to prevent mass exploitation), the issue likely lies in the mishandling of some edge-case HTTP input when processed by system libraries.
Attacker connects to a vulnerable HTTP service running on the Solaris server.
2. They send an unusual or intentionally malformed HTTP request exploiting a parsing bug or buffer mishandling bug in the Solaris library.
3. This causes a memory corruption or triggers a code path leading to the process crashing and, in the worst cases, the *entire system hanging* or going down, causing a full Denial of Service.
Proof of Concept (PoC)
A real-life working exploit is not publicly available (as of June 2024), and Oracle has not published technical details. However, based on the description, a typical PoC could look like this, using Python to craft a malformed HTTP request:
import socket
target = 'solaris11-victim.example.com'
port = 808 # Port where the vulnerable HTTP service is running
# This payload should be adapted if further technical data surfaces
payload = b"GET /" + b"A" * 10000 + b" HTTP/1.1\r\nHost: %s\r\n\r\n" % target.encode()
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target, port))
s.send(payload)
s.close()
print("Payload sent, check if the service crashed.")
except Exception as e:
print("Exploit failed:", e)
*Adapt this payload as specific trigger details become available.*
Chain attacks to disrupt business operations or create a distraction for more targeted attacks.
*No evidence suggests potential for data exfiltration or integrity compromise, but a persistent DOS can have severe operational impacts.*
Oracle has released fixes for this vulnerability in their April 2023 Critical Patch Update.
Limit HTTP exposure.
Restrict network exposure for Solaris-based HTTP services, especially if they don’t need broad access.
Network Gateway Filtering.
Block traffic from untrusted sources to ports/services running on Solaris.
References
- CVE-2023-21984 NVD Entry
- Oracle CPU Advisory (April 2023)
- Solaris Security Updates
Conclusion
CVE-2023-21984 may seem minor compared to privilege escalation or RCE bugs, but its ease of exploitation and high availability impact make it dangerous in the real world. Because so many critical business and infrastructure servers still run Solaris 11, admins should apply the necessary patches as soon as possible and review the exposure of all networked services.
If you are running Oracle Solaris 11, make it a priority to review your systems, apply updates, and restrict HTTP access where feasible. Denial of Service may not steal secrets, but it can still stop business in its tracks.
Timeline
Published on: 04/18/2023 20:15:00 UTC
Last modified on: 04/18/2023 20:37:00 UTC